In this post, learn how to locate any device through Kali Linux using tools. Here, nGrok, sneeker, and IP locator tools are used. Before diving into the practical let’s take a look at some theoretical aspects.

Google has set out an update to Chrome web browser version 86.0.4240.111 that addresses five security bugs, including vulnerabilities that are proven to be actively exploited by attackers.
Google patched 2 more zero-day attacks last year which includes CVE-2019-5786 (Chrome 72.0.3626.121) in march and CVE-2019-13720 (Chrome 78.0.3904.8) in November.
The zero-day is tracked with the CVE-2020-15999 ID, and is identified as "type V8 uncertainty."
V8 is a part of Chrome which is responsible for processing JavaScript code.
A type confusion refers to coding bugs in which an app contains data execution using a particular "type" input. But is misled to treat the input as a "type" other than that.
The "type mistake" leads to logical errors in the memory of the app and can lead to an attacker running an unauthorized malicious code in the app.
This form of memory-corruption bug called heap buffer overflow in Freetype. A common open-source software development library for rendering fonts that come bundled with Chrome.
Security researcher Sergei Glazunov of the Google Project Zero discovered and announced the vulnerability on 19 October and was subject to a public release deadline of seven days as a result of the flaw in active exploitation.
Project Zero leader Ben Hawkes shared the information and the link on his Twitter account to the stable patch update. He says that FreeType's "actively abused" zero-day was used to target Chrome.
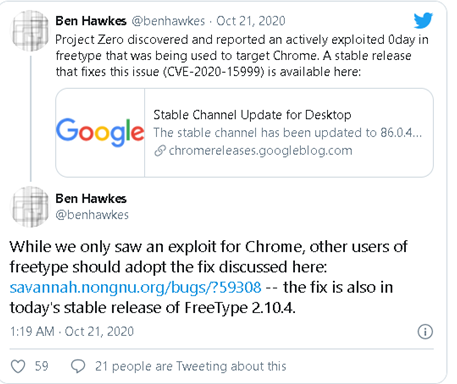
He also warned that while the bug was spotted in Chrome only, other FreeType library users should check whether or not they were under attack. He shared with the bug fix program the link to indicate that the fix was also included in FreeType 2.10.4's latest stable release.
Four other flaws are also patched with three of them high and one medium-sized bug.
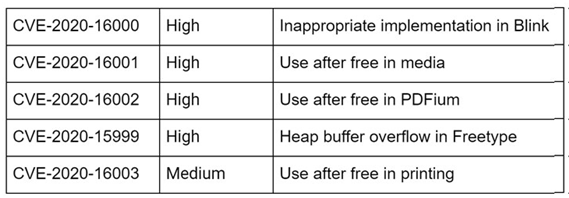
Whereas the Chrome Web browser automates the latest available version, users can activate the update by using the "Help Google Chrome" menu to manually activate the update process.
Users also read:
How to Snoop With Kali Linux on Bluetooth devices
Bluetooth has become a major component of our lives. Bluetooth devices used every day by many individuals around the globe.
How to do Server Side Includes Injection (SSI) Using bWAPP
On the HTML page, SSI directives are used for dynamic content. SSIs are used to run some activities before loading the current page.

