This post is to show how to evade anti-virus detection using the Veil framework, which is a set of tools built for penetration testing.
In this article, we will go through the web security vulnerability known as Server Side Request Forgery. The topics covered are as follows:
Introduction to SSRF
Impact of SSRF
How SSRF works
Types of SSRF
Performing SSRF using Charles proxy
SSRF Prevention Methods
Conclusion
Introduction to SSRF
SSRF stands for Server-Side Request Forgery. This vulnerability is also known as Cross-Site Port Attack. It is a Web Security Vulnerability that allows the attacker to send the malicious HTTP request to the server & gain access to internal resources that are protected by WAF (Web Application Firewall).
In short, we can say that in this vulnerability attacker uses HTTP requests to attack the arbitrary domain of his choice.
In short, we can say that in this vulnerability attacker uses HTTP requests to attack the arbitrary domain of his choice.
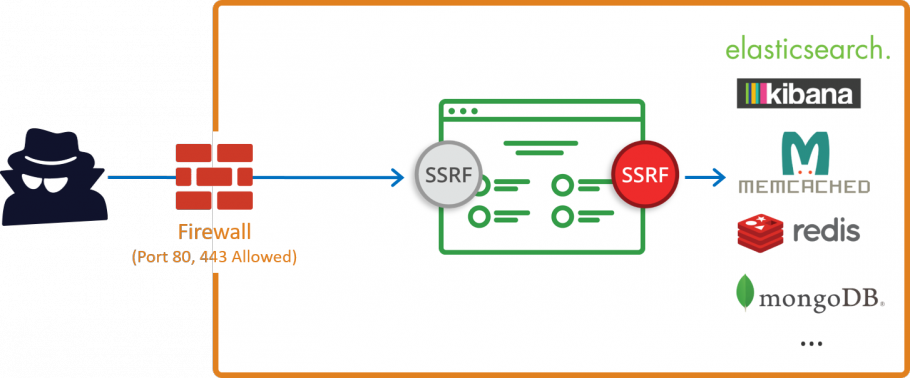
Source : Acunetix
Impact of SSRF
A successful SSRF attack can often result in unauthorized action or access within the system through a third-party application, either in the application itself or on the back-end application through which the application communicates.
With a successful SSRF attack, you can perform various other things including port scan, internal scan, read resources that are not accessible to them, abusing the vulnerable server, retrieve sensitive information, and many more.
With a successful SSRF attack, you can perform various other things including port scan, internal scan, read resources that are not accessible to them, abusing the vulnerable server, retrieve sensitive information, and many more.
How SSRF Works
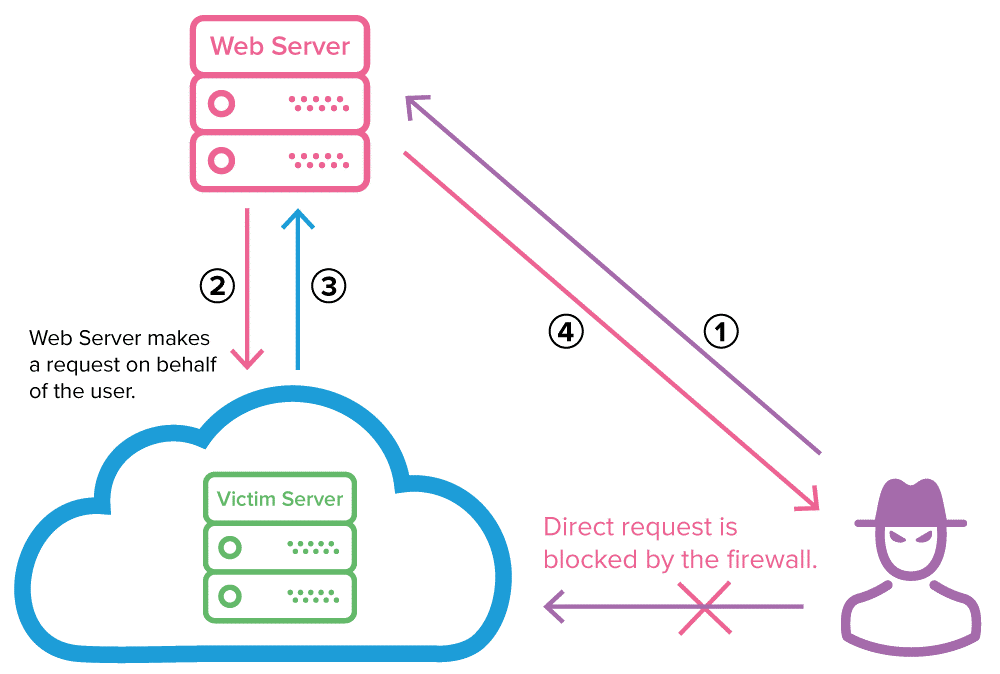
Source: DZone
An attacker sends the requests of the vulnerable server.
The vulnerable server requests the victim server which is protected with a Firewall
The victim server responds to the vulnerable server
An attacker sends the requests of the vulnerable server.
Types of SSRF
There are two types of SSRF vulnerabilities
1. Basic SSRF: The one which displays the result to the attacker
2. Blind SSRF: The one which does not show a response.
1. Basic SSRF: The one which displays the result to the attacker
2. Blind SSRF: The one which does not show a response.
Let’s take a look at the common SSRF attacks
SSRF Attack Against Itself
In this type of attack, the attacker tempts the server of making an HTTP request to the server that’s hosting the application. This request will generally include the loopback address i.e 127.0.0.1 or localhost
For e.g: A shopping site allows users to check the stock of products in 3 different cities targeting the particular store. To show the stock remaining the application must query the server that contains all the information. This requires to send the URL to the server at the end-point using an HTTP request. So when the stock has viewed the request made by the browser is:
For e.g: A shopping site allows users to check the stock of products in 3 different cities targeting the particular store. To show the stock remaining the application must query the server that contains all the information. This requires to send the URL to the server at the end-point using an HTTP request. So when the stock has viewed the request made by the browser is:
POST/product/stockHTTP/1.0
Content-Type:application/x-www-form-urlencoded
Content-Length:118
stockApi=http://stock.weliketoshop.net:8080/product/stock/check%3FproductId%3D6%26storeId%3D1
Content-Type:application/x-www-form-urlencoded
Content-Length:118
stockApi=http://stock.weliketoshop.net:8080/product/stock/check%3FproductId%3D6%26storeId%3D1
Here, the browser will request a specific URL, get stock status, and return the information. During this whole process, the attacker can fetch the URL and modify it to query the server itself.
For example:
For example:
POST/product/stockHTTP/1.0
Content-Type:application/x-www-form-urlencoded
Content-Length:118
stockApi=http://localhost/admin
Content-Type:application/x-www-form-urlencoded
Content-Length:118
stockApi=http://localhost/admin
Here the attacker will be able to gain the resources of admin. Due to this, the attacker will have full access to all the administrative resources. Due to this SSRF is a critical vulnerability.
SSRF Attack Against Other Back-end Systems.
Another type of attack is when the server can interact with other back-end-devices that are not generally accessible to the end-user. These systems have a non-routable private IP address. Generally, these types of devices are protected with network topology so they have weaker security. Sometimes these types of devices are accessible directly if you can access the backend devices without authentication.
Performing SSRF Using Charles Proxy
In this video, we have explained how you can exploit SSRF vulnerability using Charles proxy.
So the question arises that what is Charles's proxy?
Charles proxy is a web proxy (HTTP Proxy / HTTP Monitor) that works on your personal computer. You can configure your browser to use the internet through Charles. It can display the results of data and received between browser and client.
So the question arises that what is Charles's proxy?
Charles proxy is a web proxy (HTTP Proxy / HTTP Monitor) that works on your personal computer. You can configure your browser to use the internet through Charles. It can display the results of data and received between browser and client.
SSRF Prevention Methods
The following are the methods that can help to take preventive measures against SSRF.
Whitelisting the IP & DNS
The most efficient way to prevent SSRF is whitelisting the Ip address or DNS name that your system needs to access. But if whitelisting is not possible for you you can always go for blacklisting but the attacker can always bypass the blacklisting. It is important to validate user input.
Sanitize the User Input
Don’t accept the request blindly from the trusted user too. Every request should be validated and then accepted from user input to avoid SSRF
Response Management
To prevent data leakage to the attacker customized error page should be generated. The raw response body of the server request must not be submitted to the client under any circumstances.
Disable the Use Of Unused URL
If your application is using HTTP or HTTPS then every other protocol should be blacklisted. In other words, you can whitelist these two protocols and blacklist every other protocol so that other schemas such as file:///, direct://, FTP://, touch://, and more cant be used.
Authenticate Internal Resources
There is some application such as MongoDB that doesn’t require authentication. This type of application can be accessed by an attacker to launch an SSRF attack. Therefore, it is best to authenticate internal resources whenever possible.
Install Firewalls
Installing a firewall doesn’t make your data secure it just creates another barrier between the attacker and your data. But it is recommended to install a good firewall with strong policies.
Conclusion
Not all SSRF needs to use the HTTP protocol. The attacker can use any other protocol or they can even redirect the protocol. Luckily the SSRF vulnerability is not very common but it can cause a serious security breach. SSRF is beginning to be a problem for those also who have the infrastructure in the cloud. It’s best to take precautions before you are a victim of SSRF or any other Web Security vulnerabilities. Join our AWAPT course for more knowledge of various ways to exploit the vulnerabilities and prevention techniques.
Users also read:
How to perform Man in the middle attack with Ettercap
Man in the middle attack allows the attacker to eavesdrop between clients, servers, and people. This attack may include HTTPS connections, SSL/TLS connections, and more. In this tutorial, I am going to use Ettercap to perform Arp poising in the man-in-the-middle attack with the help of Wireshark.
How to Track Social Media Accounts by User Name Using Sherlock.
Sherlock is the platform that helps to retrieve all the social media account linked with any username across the social media platforms.

