This vulnerability was so critical that Apple has to remove the FaceTime group chat before resolving the issue in the next iOS update.

A critical flaw was reported in January 2019, for Apple’s Facetime group chat feature. The flaw allows the users to initiate a video call and add their number as a third party even before the call was connected.
This vulnerability was so critical that Apple has to remove the FaceTime group chat before resolving the issue in the next iOS update.
Similarly, various such vulnerabilities were discovered by Google Project Zero researcher Natalie Silvanovich in various video chat apps such as Google duo, Signal, FB messenger, and Mocha.
“The bug was remarkable in both its impact and mechanism. The ability to force a target device to transmit audio to an attacker device without gaining code execution was an unusual and possibly unprecedented impact of a vulnerability.” Natalie noted in her work on Tuesday.
As stated by Natalie “While this bug was soon fixed, the fact that such a serious and easy to reach vulnerability had occurred due to a logic bug in a calling state machine -- an attack scenario I had never seen considered on any platform -- made me wonder whether other state machines had similar vulnerabilities as well.”
How WebRTC Signaling Functions.
The majority of video calling apps use WebRTC for communication, By exchanging call-up information between peers in Session Description Protocol (SDP), the WebRTC connections are established, a process called signalling. In a typical scenario, the caller sends an SDP offer to which the receivers replies with an SDP answer.
In simple words, when the user initiates the WebRTC call, a session named “offer” is generated which contains all the required information for the set-up of connection such as the type of media they are sent to, their format, the transfer protocol they are using and the IP and port no of the endpoint among other things. The receiver answers with the endpoint summary.
This whole process is known as a state machine which indicates where in the machine the offer/answer is talking place.
Additionally, the two peers can exchange a few types of SDP candidates over the network. These candidates are used by both the peers for connection. It contains details about the method used to connect irrespective of the network topology of a WebRTC framework known as Interactive Connectivity Establishment (ICE).
Despite the design, an application code using WebRTC must allow the transmission of audio or video from an input device directly. Typically this is achieved with a track feature. Each input device is considered to be a 'track' and each track must be connected to a special peer link before the audio or video is transmitted by calling addTrack (or language equivalents).
These tracks can also be disabled, which is useful for mute and camera off function. Each track has an RTPSender property, which can be used to change transmission properties and which can also be used to disable the transmission of audio or video.
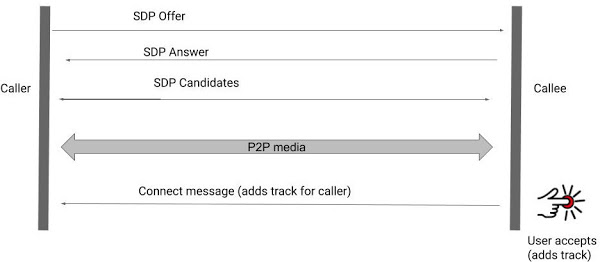
Source: Google Project Zero
Although it is anticipated that consent will be assured before audio and video transmission and that no data will be exchanged until the recipient has interacted with the call response application (i.e. before any communication tracks have been added), Silvanovich noticed the opposite.
Various Applications Affected
During the testing of WebRTC Exploit on various applications, a few of them were found vulnerable to the exploit.
Signal (fixed in September 2019) An audio call flaw was discovered in signal’s android app. The application didn’t check the receiving device allowing the caller device to receive connect message allowing the caller to hear the receiver’s surroundings.
Jio Chat & Mocha (Fixed in July and August 2020) Jio Chat & Mocha (Fixed in July and August 2020) The flaw allowed the caller to send the audio data in Jio chat and audio as well as video data in mocha without user consent. This flaw was developed because when the user sends an SDP offer/answer or answer the connection starts immediately.
Google Duo(fixed in December 2020) The rare flaw that allows the receiver to leak few video frames before disabling the transmission. It was a race between disabling the video and creating the connection.
Facebook Messenger (fixed in November 2020) A flaw that could have given the attacker the permission that is logged in application to initiate the call as well as send created messages to the victim who is logged in on another client as well such as the browser.
Few other applications were also tested like Telegram and Viber but no vulnerabilities were found in their state machines. However, challenges faced while reverse engineering of Viber made it less rigorous compared to other applications.
Natalie also stated that “The majority of calling state machines I investigated had logic vulnerabilities that allowed audio or video content to be transmitted from the callee to the caller without the callee’s consent. This is clearly an area that is often overlooked when securing WebRTC applications.”
“The majority of the bugs did not appear to be due to developer misunderstanding of WebRTC features. Instead, they were due to errors in how the state machines are implemented. That said, a lack of awareness of these types of issues was likely a factor. It is rare to find WebRTC documentation or tutorials that explicitly discuss the need for user consent when streaming audio or video from a user’s device.”
“Many of these state machines had needless complexity in how they handled call set-up, which was also a factor. Unnecessary threading, reliance on obscure features, and large numbers of states and input types increase the likelihood of this type of vulnerability occurring in a signalling state machine.”
You can find the whole write-up here.
Users also read:
Google collapse: YouTube, Google meet, Maps Stop working around the globe
Google experienced difficulties on a large scale for it’s online services, such as YouTube, Google Meet, Google Maps, Google Calendar.
Microsoft rolls out final patches for 2020: Covers 58 security flaws
Microsoft has released the security patches for recently discovered 58 security flaws as it’s final patch Tuesday for 2020. With these patches, the total number of CVE has reached 1250 for this year.

