This post is to show how to evade anti-virus detection using the Veil framework, which is a set of tools built for penetration testing.

Microsoft Office is one of the most used software programs in the world. It includes Microsoft Word, Excel, and PowerPoint, as well as Notebook, Outlook, Publisher, and Visio. Word, Excel, and Presentation are the vast commonly in use.
Millions of people use word documents in their daily lives to move documents or data, and password-protected files to keep the data secure. But, are these files, are they safe? You can quickly crack the password using hashes if you know your way around.
It has come to light that the simple tool office2john can extract the hash from an earlier version of the office. John The Ripper or Hashcat will crack the hashes that have been extracted.
This tool is Python program and can run from the command line. It will work on any password-protected Word, Excel, PowerPoint, OneNote, Project, Access, and Outlook file generated with Office 97, Office 2000, Office XP, Office 2003, Office 2007, Office 2010, and Office 2013 versions, including the Office for Mac versions. We saved a DOCX in Office 2016 that was classified as Office 2013, so it does not fit in newer versions of Office.
Let’s Begin
We'll start by downloading office2john from Github, which you can get here. Since it is not included in John the Ripper, you must install it ( Already Installed in most of Kali Linux). Using the wget command, you can easily download it.
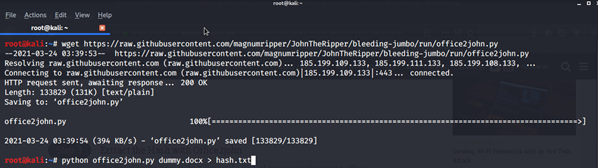
Keep Everything in the same directory
We'll need to change it into the same directory where office2john was built to run it with Python. For the most part, this will be Home (just type cd), but you can make a separate directory if you like. After that, we'll need a suitable file to test this on. I'm using a simple DOCX file called "dummy.docx" that I built in Word 2007 and password-protected. "password123" is the password.
Hash Extraction Using office2john
Let’s start with extracting the hash from the password-protected file and save it in hash.txt for later use. Use the following command: python office2john.py dummy.docx > hash.txt
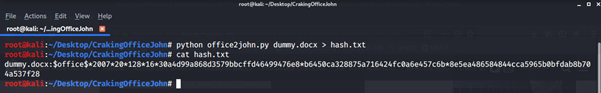
Use the cat command to check whether the hash was successfully extracted.
Crack the Hash
There are two methods to crack the hash. You can either use John the Ripper & The Hashcat. We will cover both of the methods here.
Option 1: John The Ripper
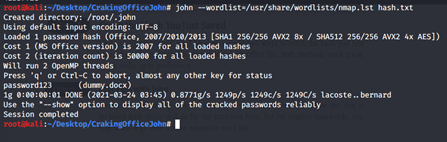
Set the --wordlist flag to your favorite word list's spot. For our purposes, the one included with Nmap will suffice, but for more difficult passwords, you will want to use a more comprehensive word list. Use command: john --wordlist=/usr/share/wordlists/nmap.lst hash.txt
Use command: john --wordlist=/usr/share/wordlists/nmap.lst hash.txt
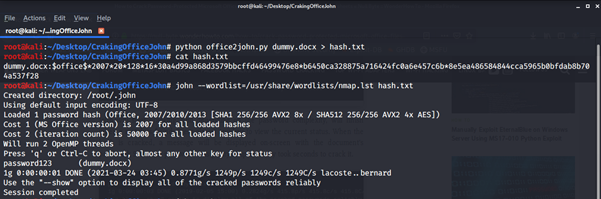
John will start the work and time will depend on the complexity of the password. A message with the document's password appears on the screen when the hash cracks. As our password is easy it took less time.
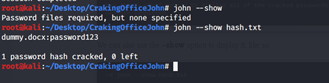
The other way to see the password is to use the option --show. We have covered one method of cracking the hash. Let’s start with another.
Option 2: Hashcat
Start with -- help menu for Hashcat. This will give us a lot of useful information, such as usage options, hash modes, and other features.
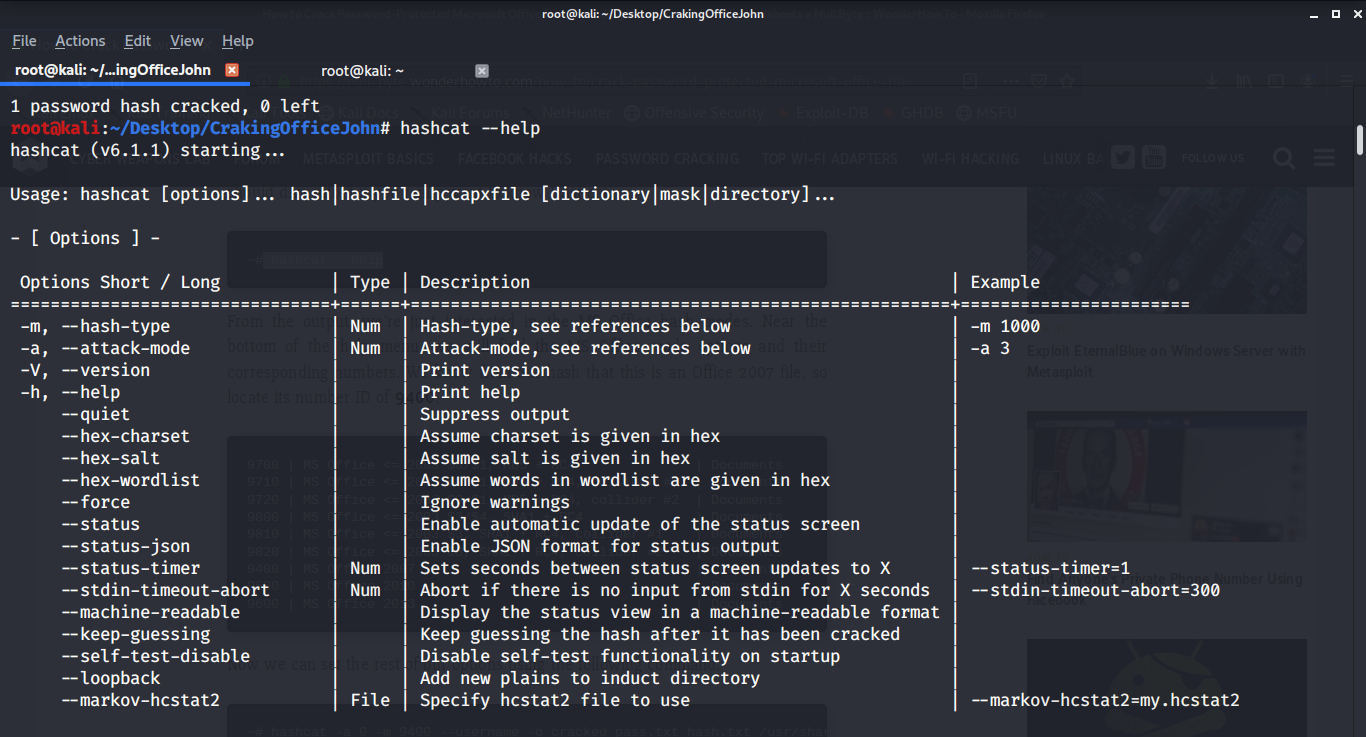
You’ll get a lot of information but we just want MSOffice hash mode. In this example, we are using the office 2007 file so the module is 9400.
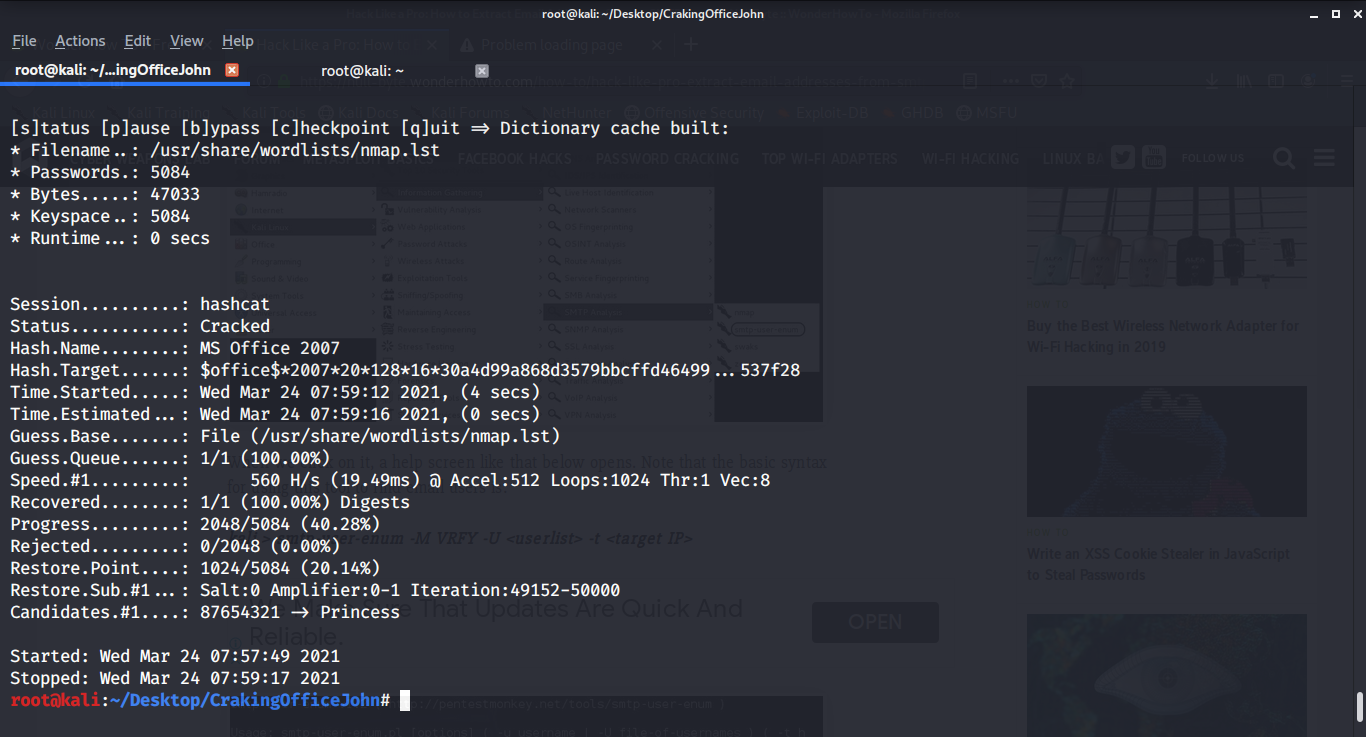
As our password is easy here we are using an inbuilt nmap list of passwords but if it is difficult you can use the password list of your choice. Use the command below to crack the password using Hashcat:
hashcat -a 0 -m 9400 --username -o cracked_pass.txt hash.txt /usr/share/wordlists/nmap.lst
hashcat -a 0 -m 9400 --username -o cracked_pass.txt hash.txt /usr/share/wordlists/nmap.lst
As soon as you click to enter the Hashcat will do its job depending on the complexity time will be taken, as our password is easy it was fast.
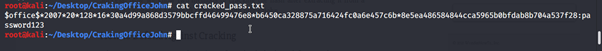
You can use the cat command with the output file cracked_pass.txt to see hash with password in Plain text.
Mitigation
When it comes to password cracking, using password best practices is the best security strategy. This entails creating a one-of-a-kind password list that is lengthy and difficult to guess. Although recent research has shown that simply using long phrases with high entropy is preferable, it helps to use a combination of upper and lowercase letters, numbers, and symbols. Long randomly created passwords are almost impossible to crack.
Conclusion
Using Microsoft Office 2016 or 2019 documents or newer might not be successful in this attack as office2john is configured to run on earlier versions of Office,. However, as seen above, Office 2016 may very well spit out a 2013 document without the user's knowledge, so that doesn't rule out the possibility of cracking a "new" file. Furthermore, there are still a lot of old Microsoft Office papers lying around, and some companies still use them, so this attack is still quite possible today
Users also read:
How to perform Man in the middle attack with Ettercap
Man in the middle attack allows the attacker to eavesdrop between clients, servers, and people. This attack may include HTTPS connections, SSL/TLS connections, and more. In this tutorial, I am going to use Ettercap to perform Arp poising in the man-in-the-middle attack with the help of Wireshark.
How To Access Android Phone Camera Using Kali Linux
In this tutorial, we will take a picture from the victim's smartphone camera without their knowledge. However, please note that this is post is for educational purposes and I have no responsibility for any illegal activity.

