This post is to show how to evade anti-virus detection using the Veil framework, which is a set of tools built for penetration testing.
How to Anonymously Conceal Desired Data Within An Image Or Audio File.
April 21, 2021
Browse All Blogs
Steganography is the art of hiding data in plain sight, and I'll show you how to do it with Steghide, a really easy command-line tool. I'll also go through some conceptual context to help you understand what's going on. This is an easy, configurable tool that hides information in a variety of file types in just a few seconds. You can download the tool from here. Let’s clear some basic theoretical concepts before jumping to the practical.
What is Steganography?
Unlike encryption, steganography hides data in plain sight within a file such as an image. In aspects of photographs, it appears to anyone who isn't aware that it contains secret data to be a regular, innocent photograph.
Steganography comes in handy when sending encrypted messages sparks suspicion, such as in countries where freedom of speech is controlled. It's also commonly used as a digital watermark to track down plagiarized images or audio files. On a more pleasant note, it's just cool.
How is Steganography Used
There are a variety of strategies for hiding data inside ordinary files. The least significant bit technique, also known as LSB, is one of the most commonly used and perhaps easiest to comprehend. This technique encrypts a message by changing the last few bits of a byte, which is particularly useful in images, where each pixel's red, green, and blue values are expressed by eight bits (one byte) varying from 0 to 255 in decimal or 00000000 to 11111111 in binary.
Changing the last two bits of a fully red pixel from 11111111 to 11111101 just changes the red value from 255 to 253, which is nearly imperceptible to the naked eye but helps us to encode data inside the image.
Efficient Use of Stenography.
Keeping in mind that some digital steganography methods are better than others, it's best to skip the LSB method and go for something a little more advanced instead. In reality, if you already have solid coding and math skills, creating your steganography algorithm isn't too difficult. However, LSB, which Steghide uses, will suffice here to get a feel for how steganography works.
Encryption and compression are two other factors to consider. Encrypting data before embedding it provides an extra layer of protection while compressing it allows you to fit more into your cover file. Steghide supports both encryption and compression schemes as optional parameters.
What is Steghide?
Steghide is a steganography software that can conceal information in a variety of image and audio files. Since the color- and sample frequencies are not altered, the embedding is immune to first-order statistical tests.
0.5.1 is the most recent edition.
Features
Compression of embedded data
Encryption of embedded data
Embedding of a checksum to ensure the integrity of the extracted data
JPEG, BMP, WAV, AU files supported
Let’s begin without further ado.
Install Steghide
It's very easy to use Steghide. In Linux, use the following command to install it from the terminal: apt-get install steghide
Embed File
Once the installation is complete embed the file you want to transfer using the following command: steghide embed -ef secret file -cf cover file -sf outputFile -p Passwordsteghide embed -ef secret file -cf cover file -sf outputFile -p Password-you-want-to-give
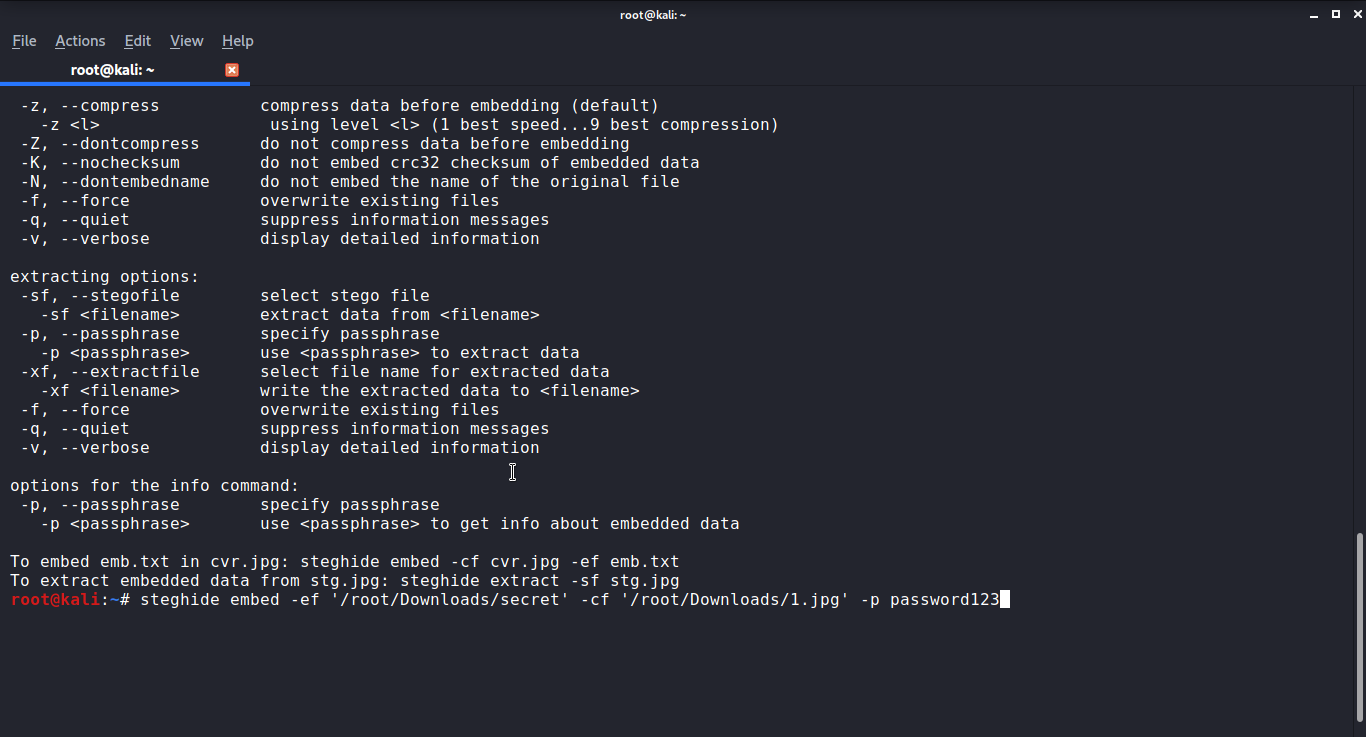
The arguments are as follows:
-ef specifies the path to the file you want to hide. You can include any type of data inside the cover file, such as Python scripts or shell files.
-cf specifies the file in which the data is embedded. This only applies to BMP, JPEG, WAV, and AU files.
-sf The optional argument specifies the output file. If you leave this out, your new steganographic file will overwrite the original cover file.
Here I am using a picture of the pier, once you have executed the command it will take few seconds to hide your data (time depends on the size of your data) in an image or audio file.


As you can see in the above images that you can’t see the difference between the embedded image or the actual image.
Extraction of Concealed Data.
Extracting the hidden data is even easier. Use the following command to pull the data from the hidden file.
steghide extract -sf stegoFile -xf outputFilesteghide extract -sf stegoFile -xf outputFile
After this command, you'll be asked to enter the same password you created earlier to extract the file.
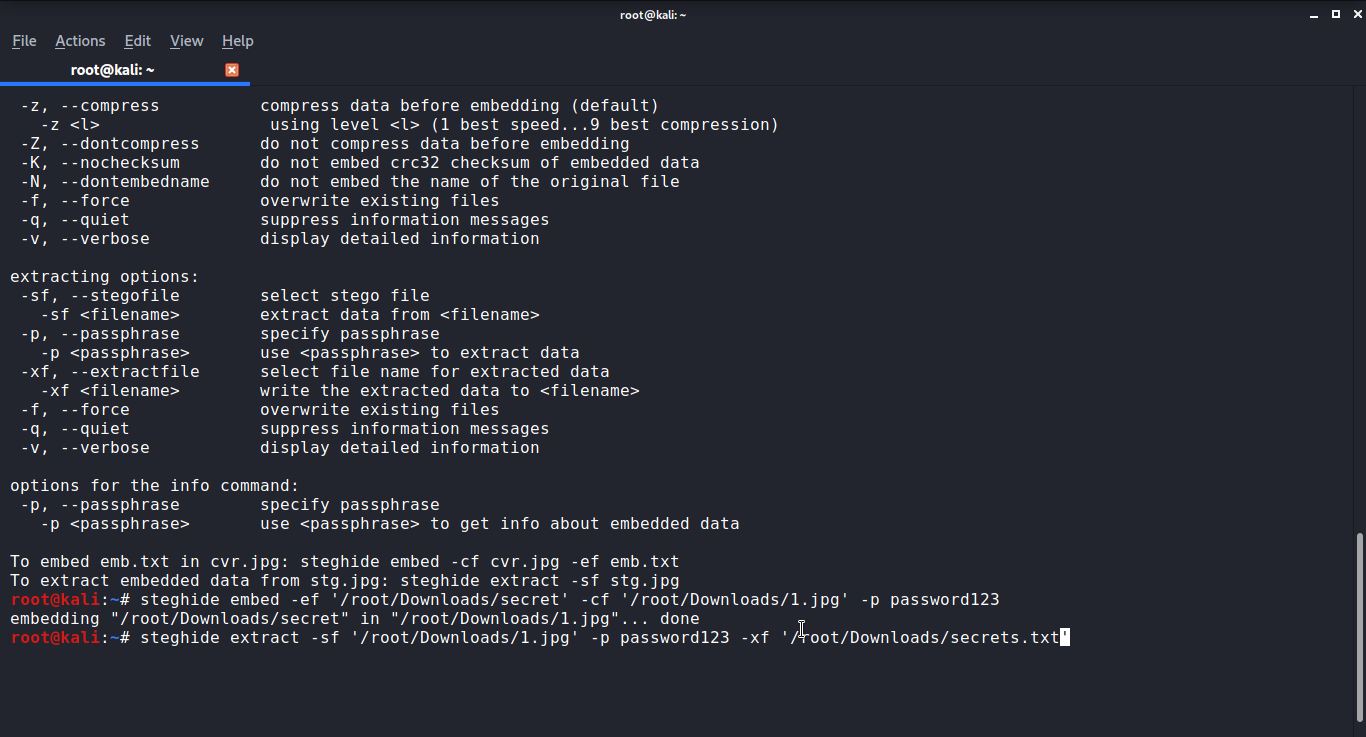
Here you will be able to create a new output file where you can get the information from the hidden file.
Concealing the Data in the Images is too Easy.
The benefit of steganography is that it allows you to conceal data in plain sight, but it can also backfire if you fail to follow basic guidelines. First, unless you have the original, the slight variations by steganography are difficult to detect. Using an image you find on the internet without changing it makes it much easier to detect hidden details in an image. To double-check, run a reverse Google Image search to see if the original is still available.
Conclusion
I hope you enjoyed this tutorial and learned how easy steganography is to use. It just takes a few seconds to conceal hidden messages inside media files, and steganography has a wide range of uses, whether you're doing it for copyright protection or just to be cool.
Users also read:
How to perform Man in the middle attack with Ettercap
Man in the middle attack allows the attacker to eavesdrop between clients, servers, and people. This attack may include HTTPS connections, SSL/TLS connections, and more. In this tutorial, I am going to use Ettercap to perform Arp poising in the man-in-the-middle attack with the help of Wireshark.
How To Access Android Phone Camera Using Kali Linux
In this tutorial, we will take a picture from the victim's smartphone camera without their knowledge. However, please note that this is post is for educational purposes and I have no responsibility for any illegal activity.

