This post is to show how to evade anti-virus detection using the Veil framework, which is a set of tools built for penetration testing.

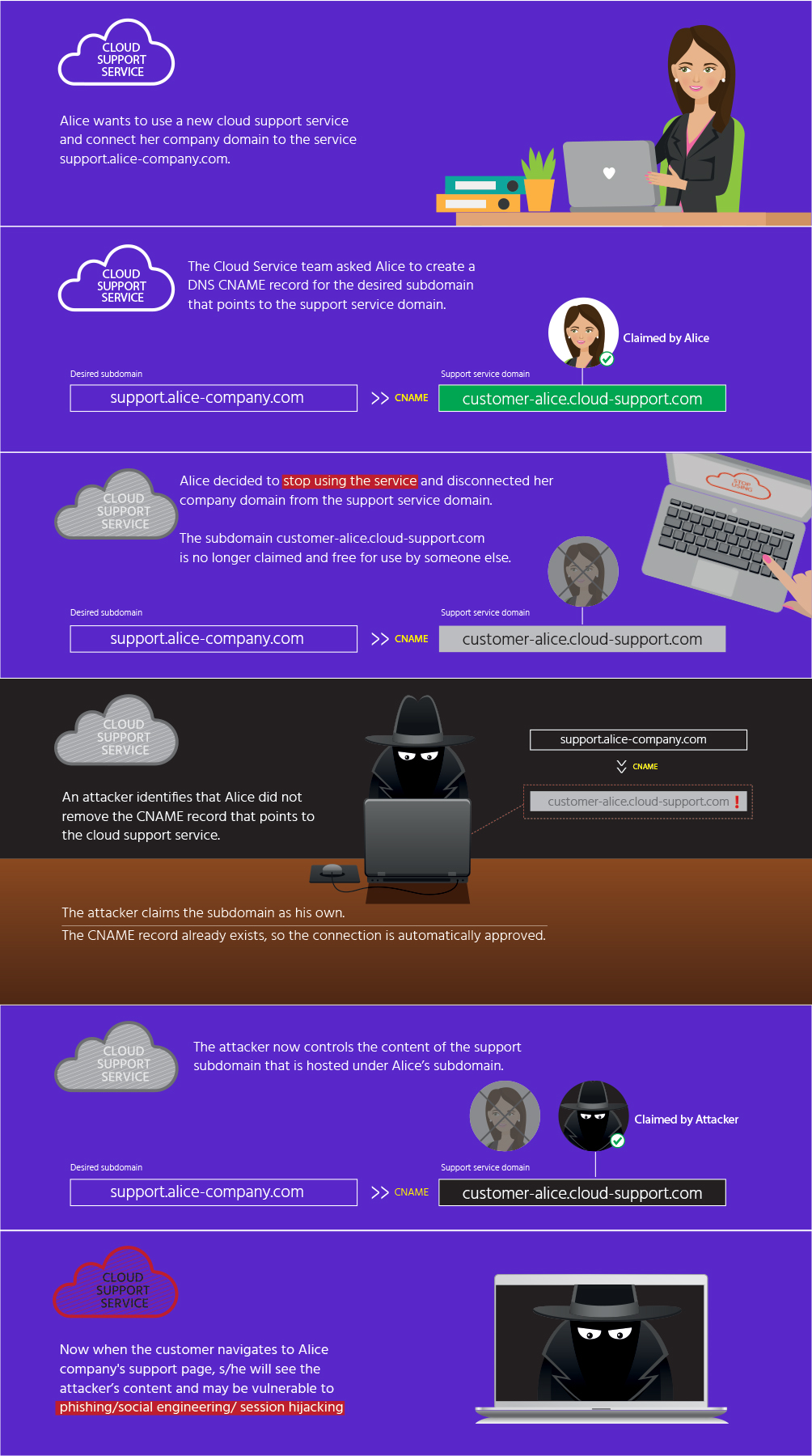
Subdomain Takeover or Domain Hijacking is a well-known security issue that can be faced in many ways.
The domain registration of perl.com was taken over on 28 January 2021. This is only one example of this. Organizations are faced with a number of these types of attacks.
What is Subdomain Takeover?
The takeover of subdomains is a process by which the ignored DNS is used to manipulate the website. Besides social engineering and unauthorized access to the owner's account, the use of subdomain takeovers is becoming widespread.
Take a look at the typical scenario.
A domain name is registered using a CNAME of another domain name (test.example.com).
The DNS expires after some time and is eligible for registration. But the DNS is not deleted from the company's records.
An intruder may use test.example.com to have complete control of example.com as long as the CNAME is not removed from the record.
The takeover of subdomains can be crucial. An attacker may send phishing emails, launch an XSS attack, or harm the goodwill of an organization linked to the domain. In this post, we will see how sub-domain takeover works, sub-domain takeover with aquatone and Github, Mitigation of a sub-domain takeover, and conclusion.
How does it works?
Source: takeover.cyberint.com
Let’s start with the automated tool Aquatone.
What is Aquatone?
Aquatone tool is written in Go. Various resources are available for subdomain enumeration, such as Sublstr3r, Gobuster, and Sub Brute. A typical method is the enumeration of brute force. However, Aquatone is taking additional steps by using open source and internet resources.
Aquatone is divided into three phases
Discovery
Scan
Takeover
Discovery: Here, to use the AQUA TONE I'm using pogo.corp.yahoo.com as the yahoo bug bounty program contains all of the *yahoo.com domain.
Start with aquatone-discovery-d domain-you-selected. This command will recognize the designated name server along with the wildcard detection. After that, a list of the subdomains will be obtained from the collector module.
The following collector modules are provided by AQUATONE
Dictionary brute force
DNSDB.org
Google Transparency Report
HackerTarget
Netcraft
Shodan (requires API key)
ThreatCrowd
VirusTotal (requires API key)
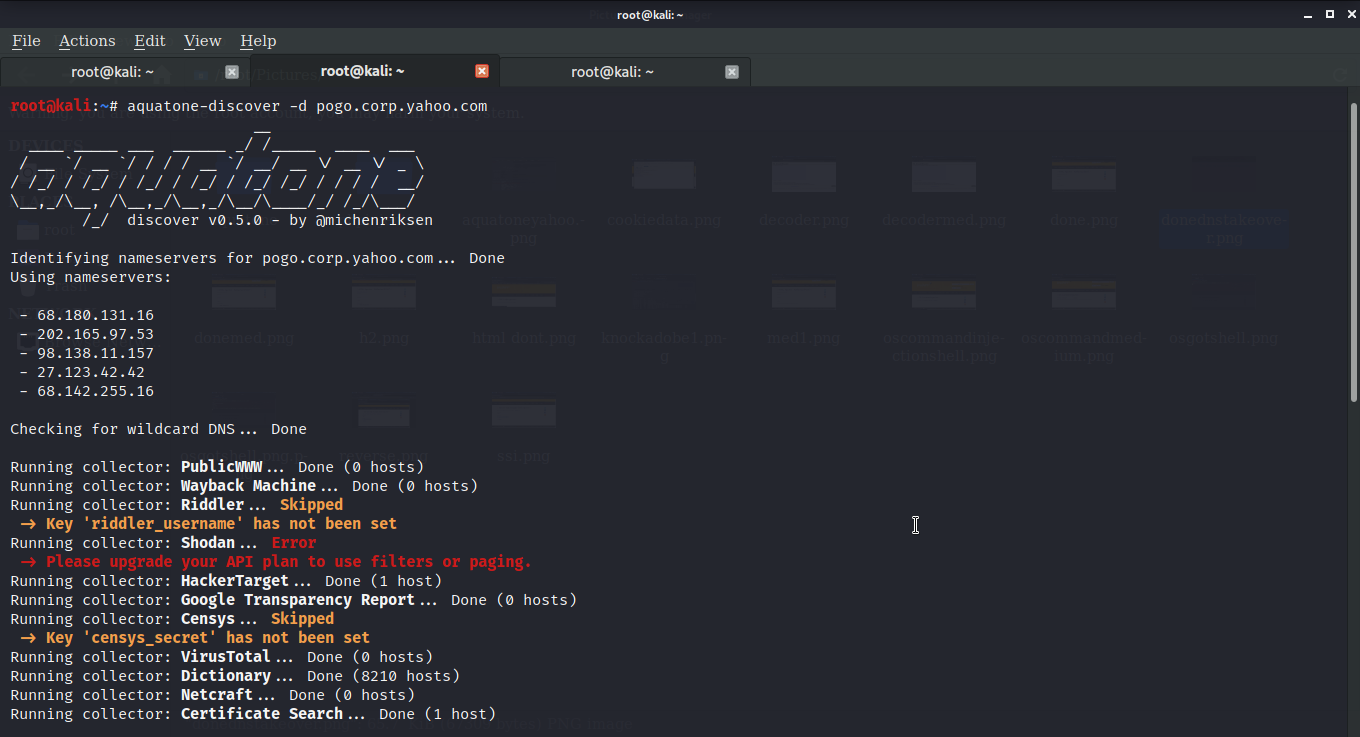
Print a list of domains identified by the collector modules and generate a file called hosts.txt and hosts.json containing the name and IP address of the subdomain separated by a comma. The JSON file can be useful if you choose to use this information in customized scripts.
Scan: The information discovered is now very useful. We can stop here and use details with a variety of resources and manual searching, but AQUATONE makes it simple for us to work with aquatone-scan-d pogo.crop.yahoo. This command will find a host that could be used to host web content.
The command found a log of open http ports on various hosts. By default, TCP Ports checked for are 80, 443, 8000, 8080, which are very popular ports on the web service.
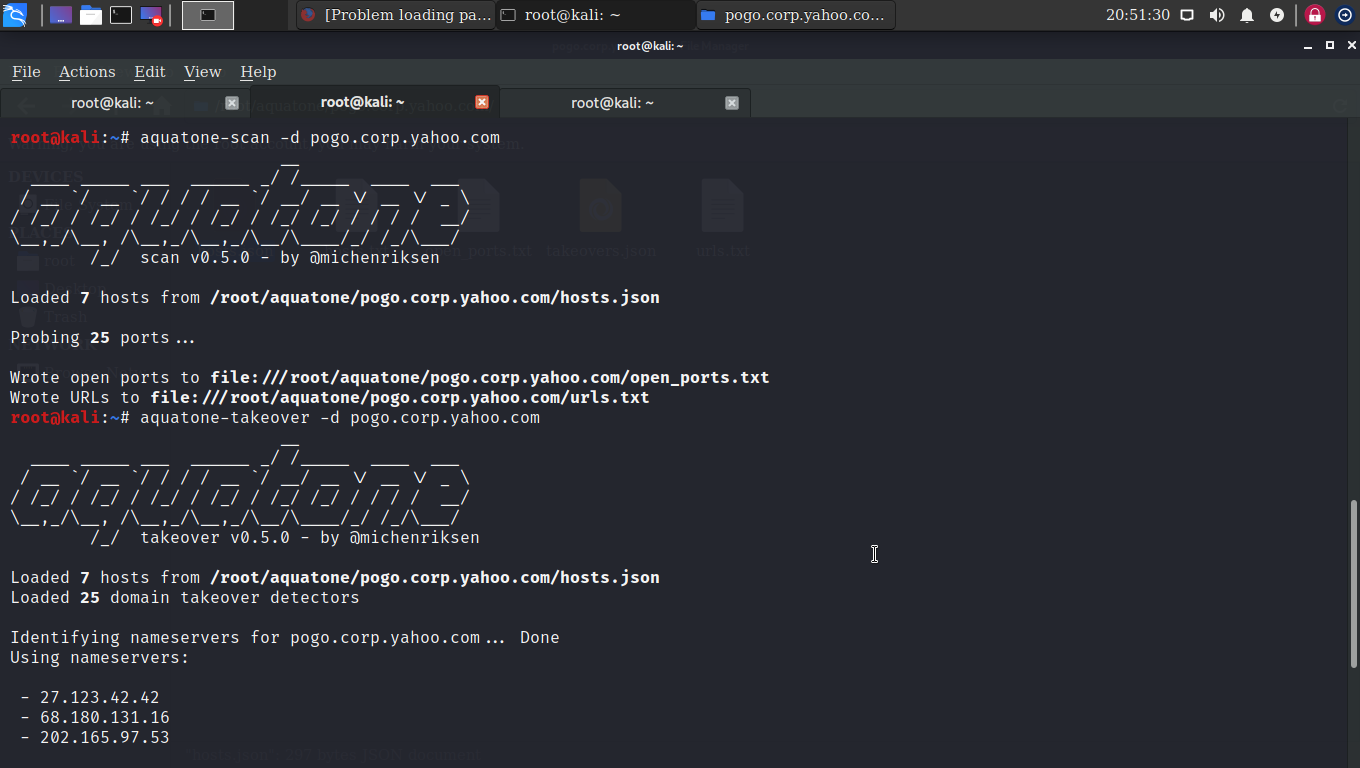
You can adjust the list by using the—port option. The command created two new files called open port.txt and url.txt.
Open port.txt will include the host list and the open port separated by a comma. And url.txt will contain URLs that can be used to navigate to the web pages of the open port.
Takeover: The information that has now been found is used for the final method. Domain Takeover is a serious problem that can affect the company in several ways. The aquatone-takeover command is used to find a takeover flaw in a list of domains discovered by the scan option.
Aquatone-takeover can identify possible subdomain takeover situations from 25 different service providers, including GitHub Pages, Heroku, Amazon S3, Desk, and WPEgine.
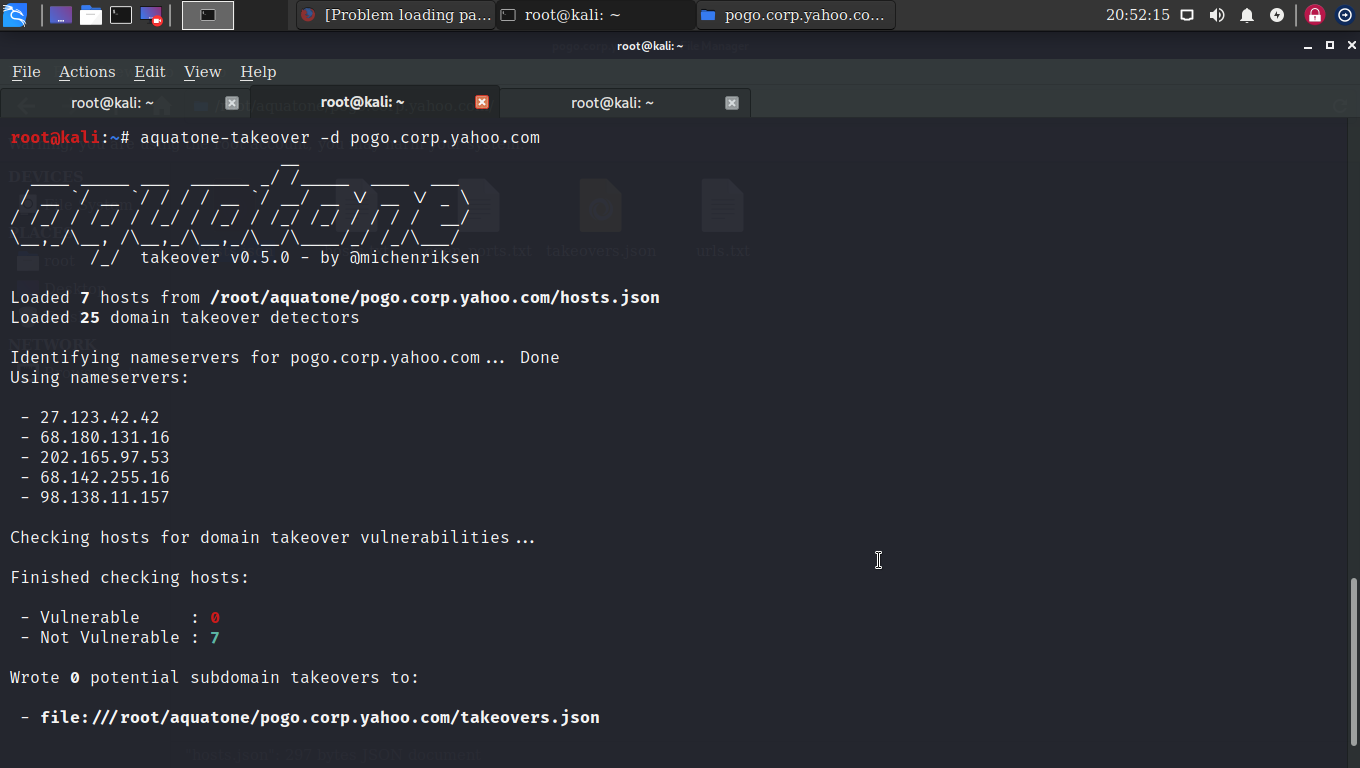
Aquatone-takeover will create a takeovers.json file in the domain analysis directory containing information in JSON format on any possible subdomain takeover vulnerabilities
Using Automated tools helps in the process of subdomain takeover. You can also do a subdomain takeover from Github. Let’s see how we can do that.
GitHub (Manually)
Here, I'm using the same domain I used for Aquatone. You can use google dork or automated software to find subdomains like knockpy, Sublist3r, and more. In this method, you will have to find the pages that have 404 errors.
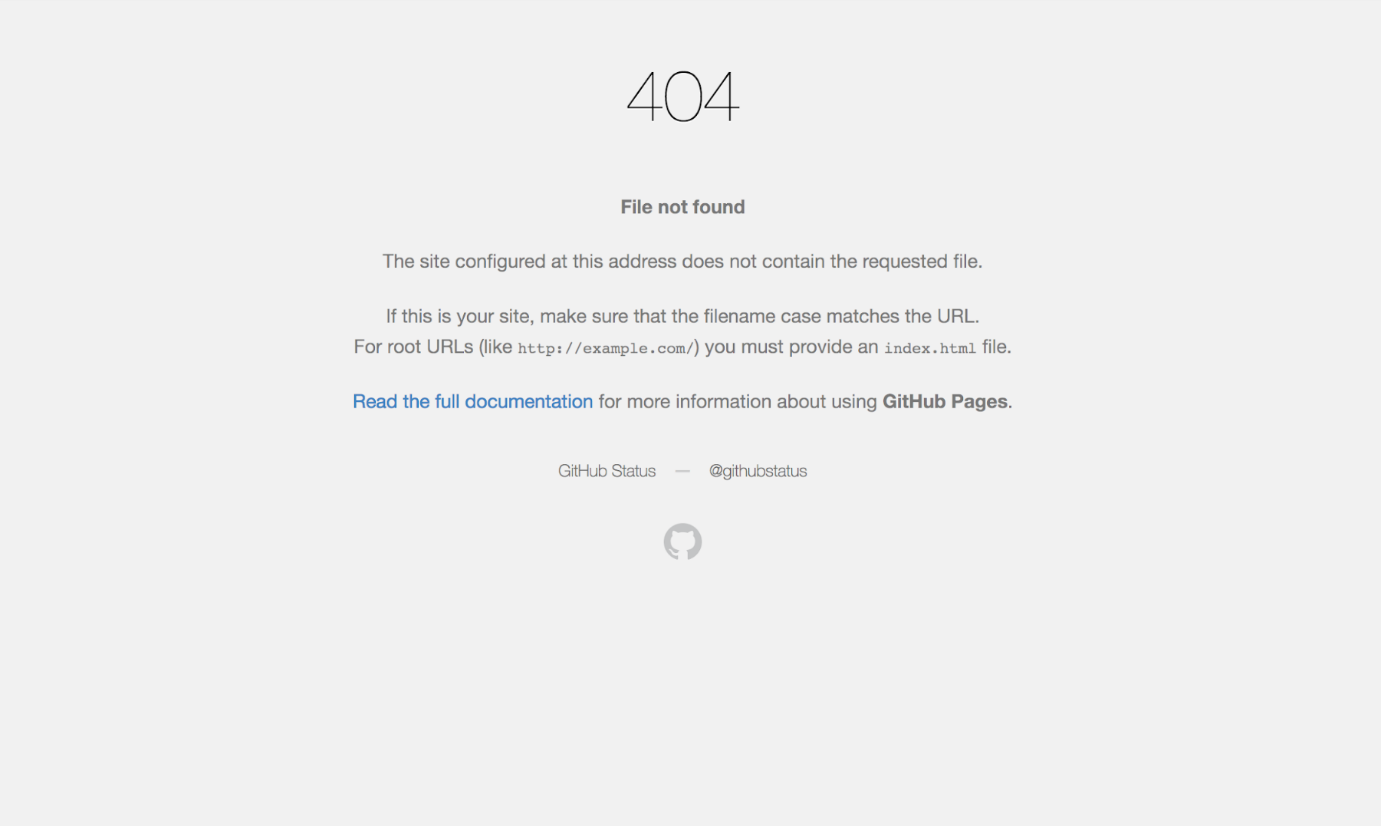
At this point most of the penetrators are excited. 404 error means there is no content in the Top Directory and we can attempt to do subdomain takeover. We should try to add the subdomain to our personal Github repository. It’s not necessary that every time it will work. Some applications check both HTTP and HTTPS for takeovers and some might not be vulnerable at all.
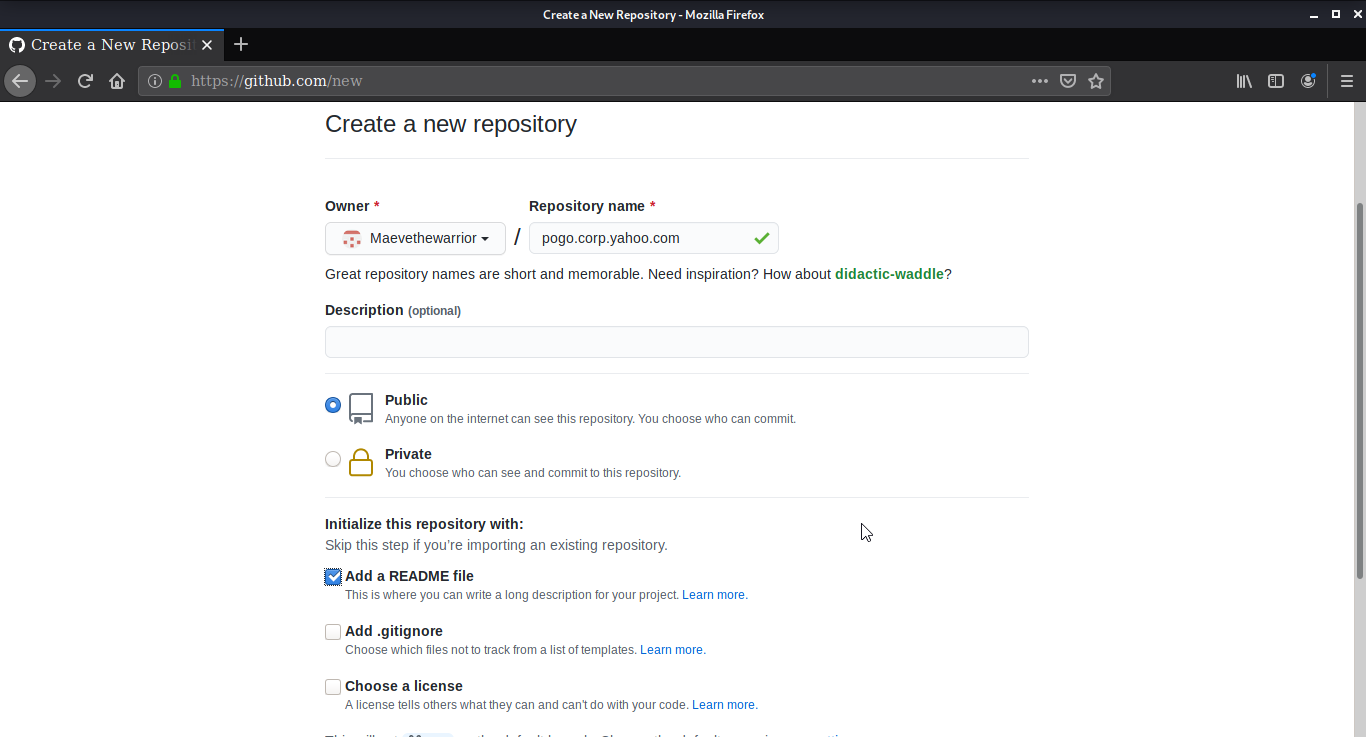
Select the main branch in Settings of GitHub page section. Add the file you want to show while the domain is takenover using add file option. Save the setting after that add the custom of domain and save the same.
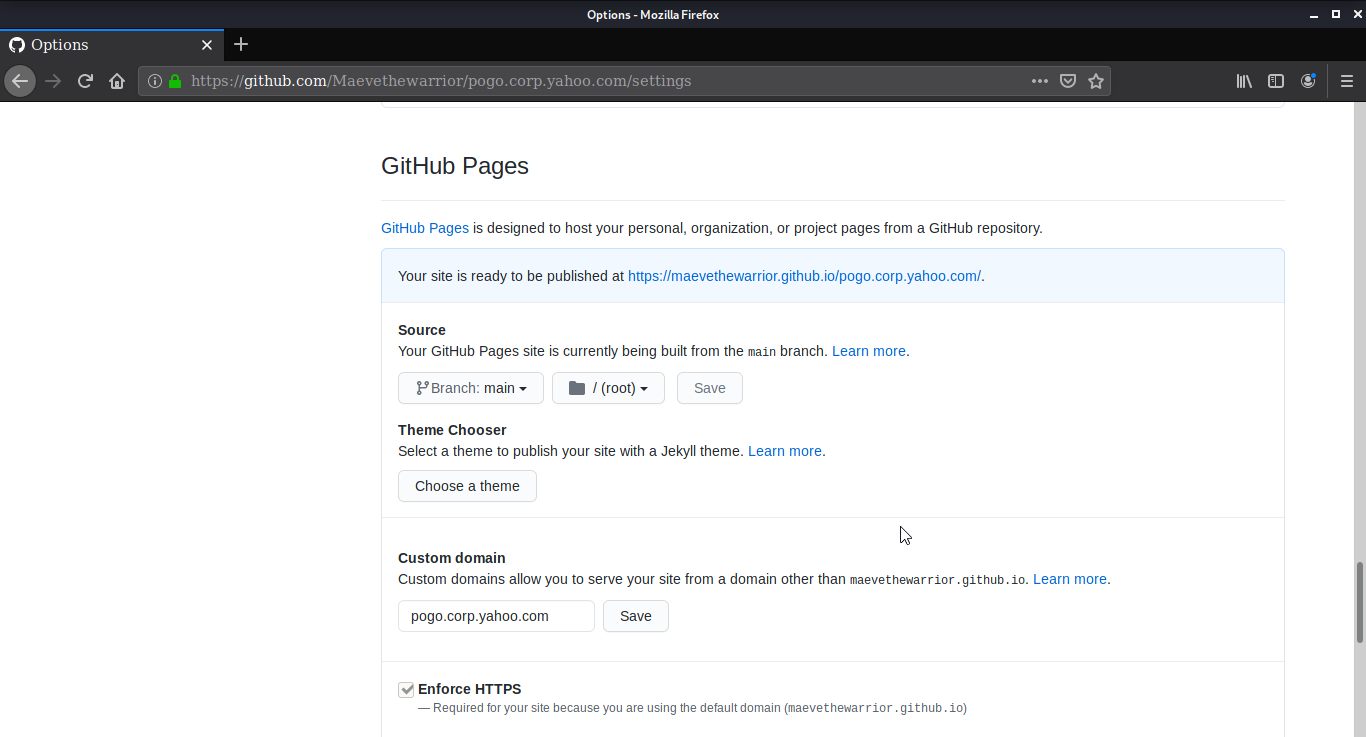
If everything is okay and the page is vulnerable you should be able to takeover subdomain.
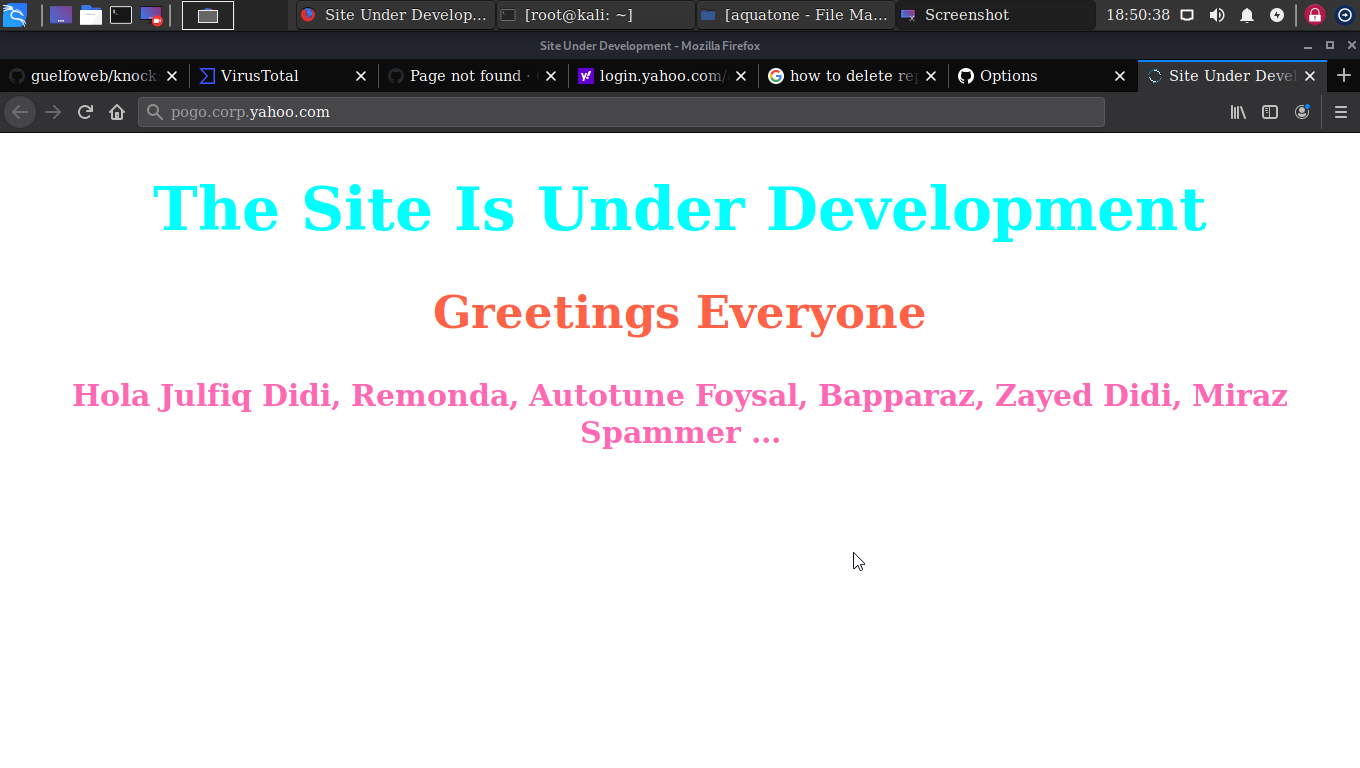
Now, the question arises, how do we revert the subdomain? The answer is simple, either remove the CNAME or delete the repository from the settings.
Mitigation of Subdomain Takeover
Remove any DNS record of your external services mapped on your subdomain. In the event that you have forgotten that your sub-domain points to an external service, which is not being changed.
Keep track of any changes in your digital infrastructure and be on the lookout for any malicious activity related to your digital properties.
Conclusion
Using this attack is simple, you just need to register a subdomain registered to an expired domain. The biggest advantage of this assault is that it is a silent attack. No notice shall be sent to the owner of the domain.
These abandoned domains and subdomains make the attacker's entry point simple. To enter the company and expose it to hijacking and takeover attacks.
Users also read:
How to perform Man in the middle attack with Ettercap
Man in the middle attack allows the attacker to eavesdrop between clients, servers, and people. This attack may include HTTPS connections, SSL/TLS connections, and more. In this tutorial, I am going to use Ettercap to perform Arp poising in the man-in-the-middle attack with the help of Wireshark.
How to Track Social Media Accounts by User Name Using Sherlock.
Sherlock is the platform that helps to retrieve all the social media account linked with any username across the social media platforms.

