This post is to show how to evade anti-virus detection using the Veil framework, which is a set of tools built for penetration testing.

Open-source analysis on an individual aim to uncover clues that connect information about a target to a wider context. User names are ideal for this because they are special and can be used to connect data across multiple accounts. We can use Sherlock to find social media accounts with a unique username across several social platforms in real-time.
With just a single cue like a username or email address, Sherlock can expand a target's history. Many people leave their online platforms' privacy settings to their defaults, making them easy targets. A single username will reveal the target's other social media accounts, photos, hobbies, family information, and more.
What is Sherlock?
Sherlock is the platform that helps to retrieve all the social media account linked with any username across the social media platforms.
What can you discover with Sherlock?
Social media accounts are a gold mine of information. One social media account contains links to others with different user names, requiring you to do another round of searches to include the new leads. When the target has a preferred profile picture, images from profile photos are simple to put into a reverse image search, allowing you to find other profiles using the same image.
A profile's description can be copied and pasted between profiles, allowing you to search for profiles that have the same profile content or descriptions.
Prerequisite
You will need python3.6 or higher. Along with that, you need to install pip3 for Sherlock. It’s a cross-platform so can be used on various Operating systems. You can download sherlock from here.
Let’s Begin
To get started, install sherlock. You can do that by following the instructions on the Github repository. You need to install all the dependencies along with sherlock from the requirments.txt using pip3.
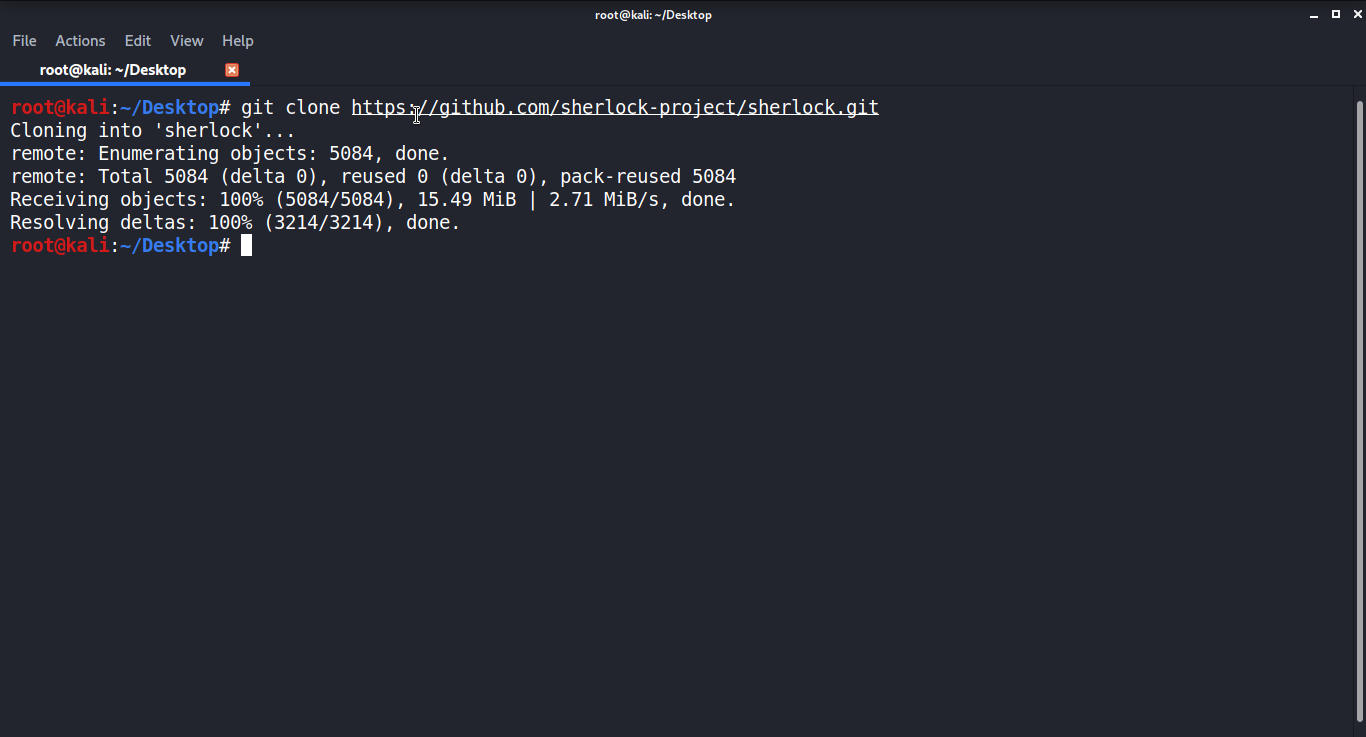
If something goes wrong, make sure you have python3 and python3-pip enabled because Sherlock needs them. To see the support menu, run python3 sherlock.py -h from inside the /sherlock folder once it's done downloading.
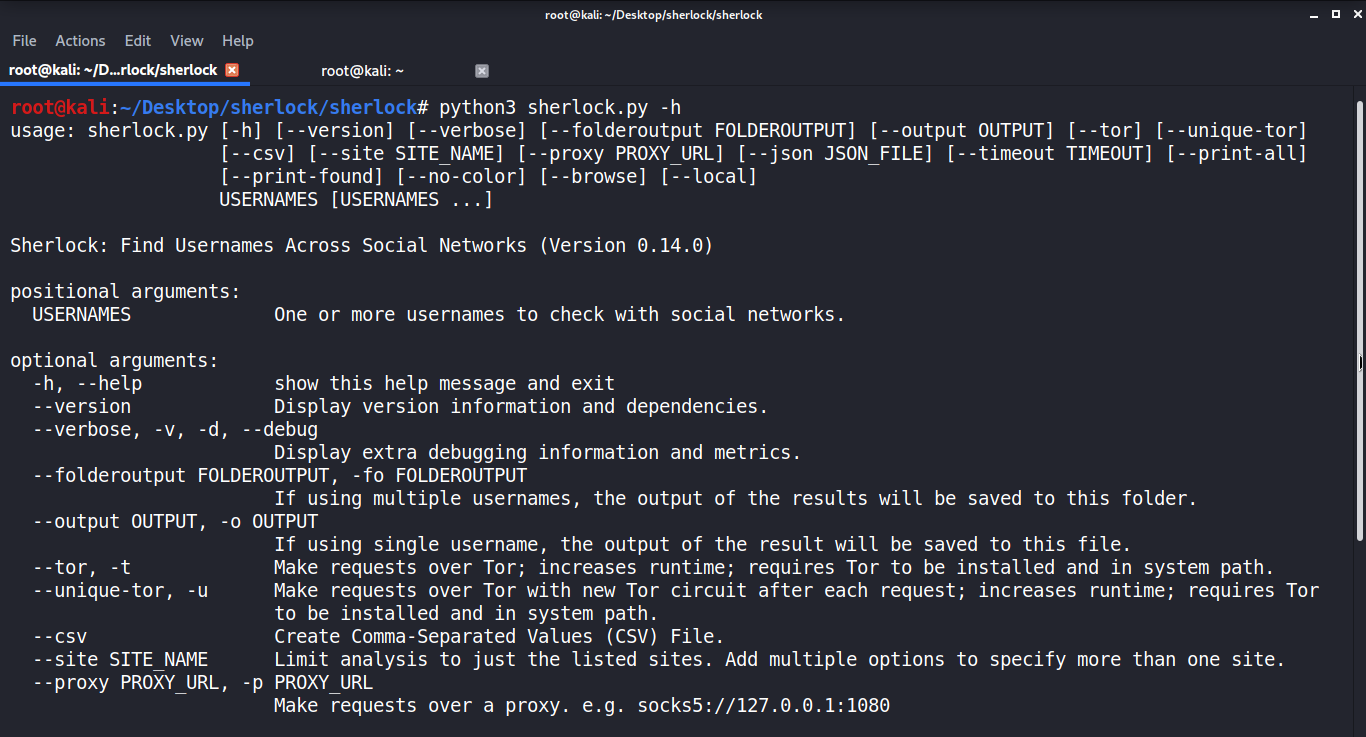
As you can see, there are numerous options here, including options to use Tor. Although we won't use them today, these features can be helpful when we don't want anyone to know who is making these requests directly.
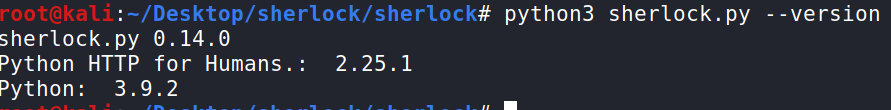
Check Version
You can check which version of Sherlock you are using with the command: python3 sherlock.py --version
Select the Username
For this tutorial, I'll use Neil Breen as an example, who has directed several intense films. But you can use a different person of your choice. Let’s find the username with a twitter search.
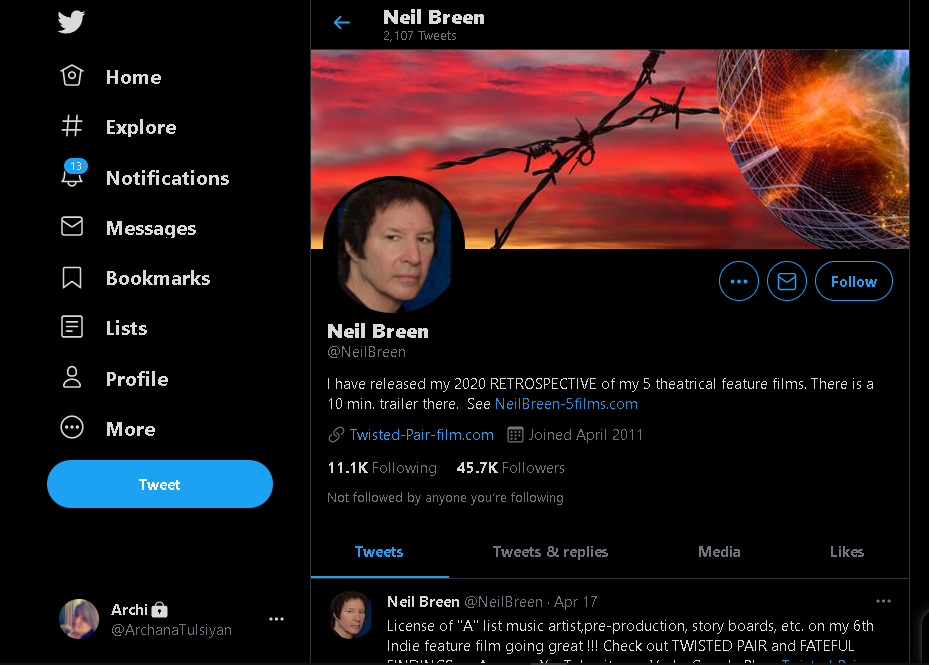
That's our guy over there. Neilbreen is the username we'll be looking for. We'll design that as the following instructions, which will look for profiles with the username "neilbreen" around the internet and print only the results. It will drastically reduce the performance since the vast majority of queries will be negative. Use the command python3 sherlock.py neilbreen
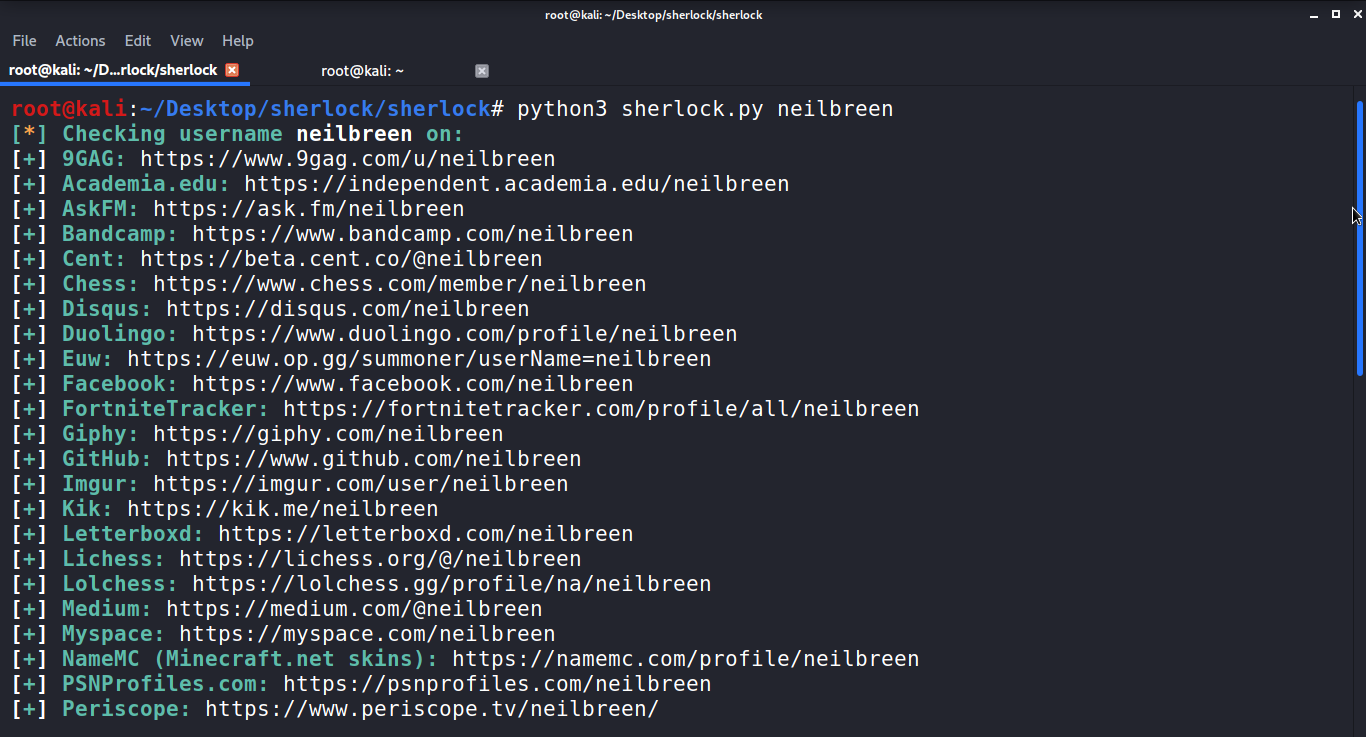
We also have a convenient text named neilbreen.txt file to store the results in addition to this output. Let's get started and see what we can find from the results now that we have some connections.
By entering the following cat command, you can check the details, which provides us with a large number of URL targets to choose from.
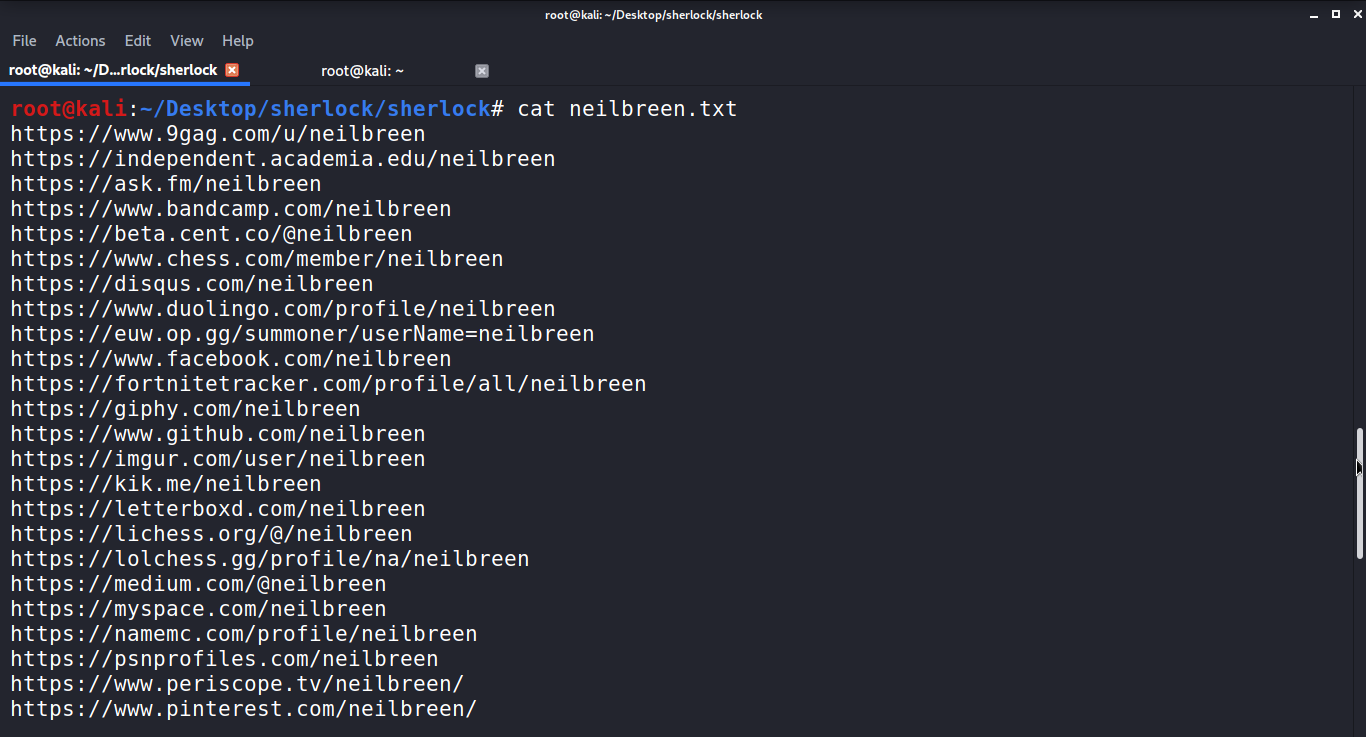
We can rule out a couple of these. Because of Neil Breen's international celebrity, there are a lot of fan accounts here. When trying to find out more about this living legend, we'll have to use some common-sense strategies to rule them out.
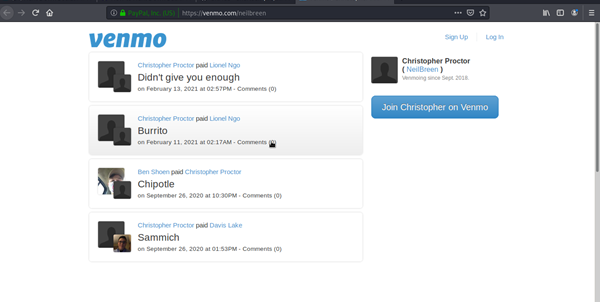
Venmo Account
First, we note that a Venmo account is mentioned. Although this isn't the case, many people make their Venmo payments public, allowing you to see who and what they're paying. This account seems to have been set up by a fan to receive donations on behalf of Neil Breen in this case. It's a dead end.
We then proceed down the list, which is sorted by a popularity ranking of the most popular pages. We're looking at an account that appears to be a personal account.
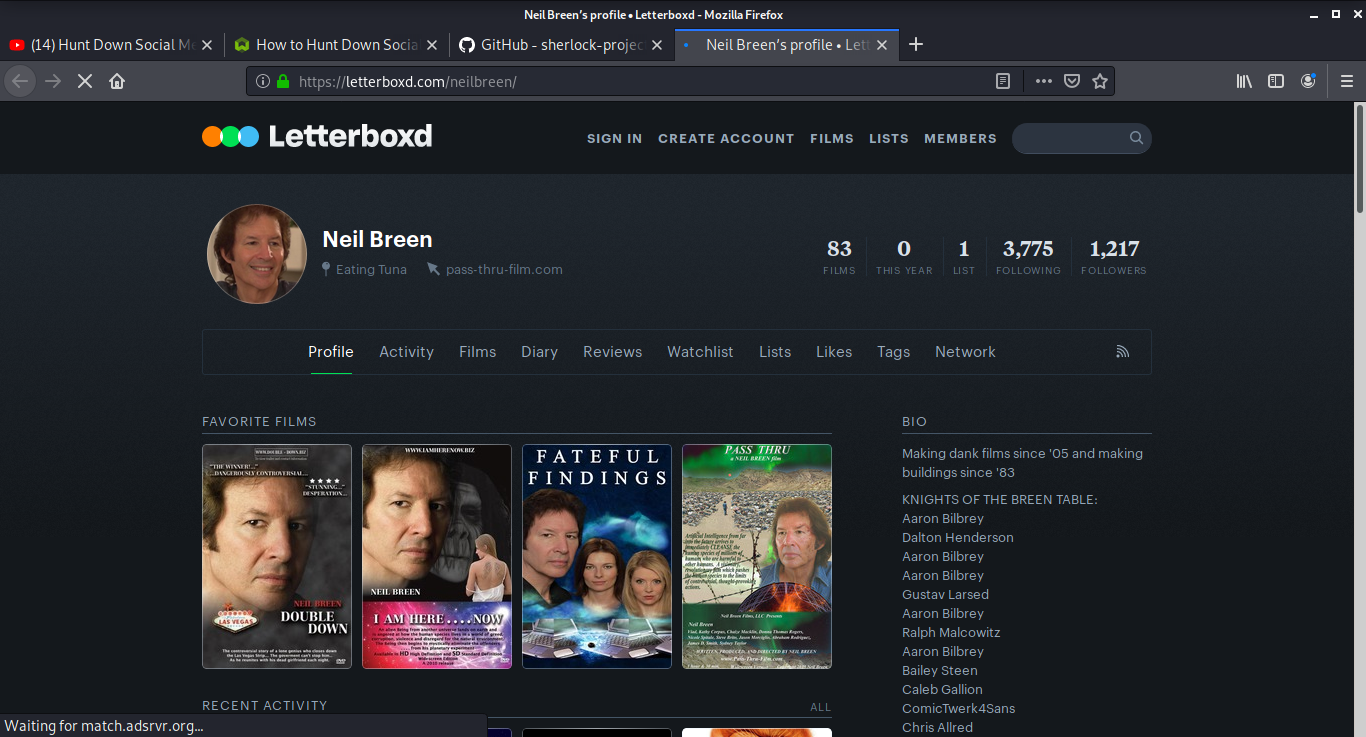
A reverse image search of Neil's Letterboxd and Twitter profile photos reveals that the target also uses the screen name neil-breen. It leads back to the target's active Quora account, where he gives unknown strangers advice.
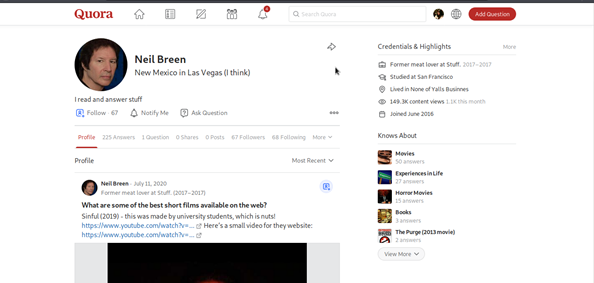
By using just one user name we have discovered another one with the help of profile picture.
Individuals often use websites to exchange information that makes them another common source of information. Like, Slideshare allows people to share presentations.
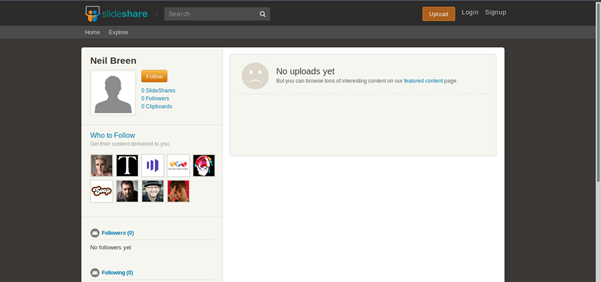
We can view all the presentations made by the purpose for business or personal purposes here. It's a dead-end in our situation. However, a search for the Reddit account we uncovered shows that it was created before he gained popularity
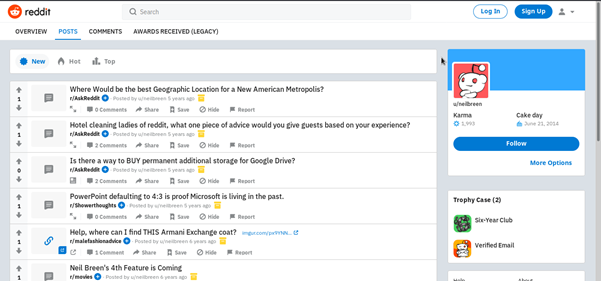
We can view all the presentations made by the purpose for business or personal purposes here. It's a dead-end in our situation. However, a search for the Reddit account we uncovered shows that it was created before he gained popularity
Finally, we have an active eBay account, which helps us to see what Neil buys and read reviews from sellers.
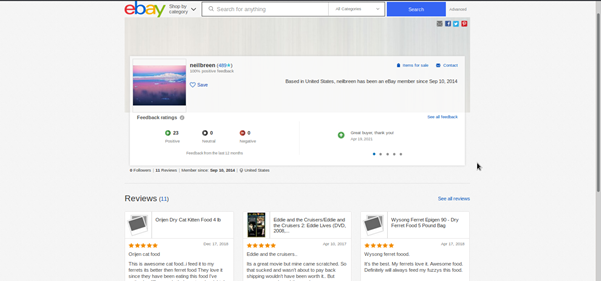
The information here allows us to look at hobbies, business ventures, and other details that have been revealed by eBay transactions that have been checked and are publicly identified under that screen name.
Conclusion
Therefore, we can say as discovered during our test analysis, Sherlock offers a wealth of cues for locating useful information about the victim. Sherlock can put in a startling amount of personal information, from Venmo financial transactions to alternate screen names discovered by looking for favorite profile images.
I hope you enjoyed this guide and learn something new.
Users also read:
How to perform Man in the middle attack with Ettercap
Man in the middle attack allows the attacker to eavesdrop between clients, servers, and people. This attack may include HTTPS connections, SSL/TLS connections, and more. In this tutorial, I am going to use Ettercap to perform Arp poising in the man-in-the-middle attack with the help of Wireshark.
How To Access Android Phone Camera Using Kali Linux
In this tutorial, we will take a picture from the victim's smartphone camera without their knowledge. However, please note that this is post is for educational purposes and I have no responsibility for any illegal activity.

